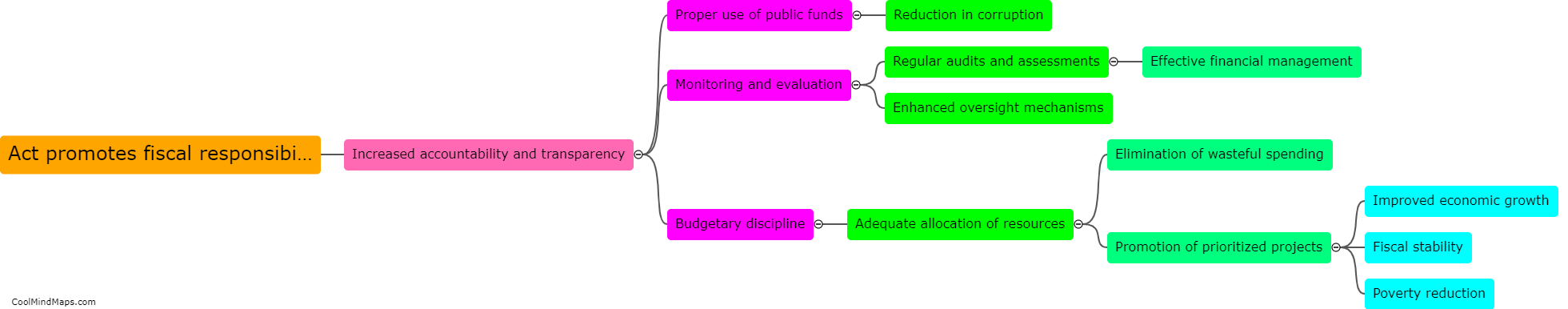
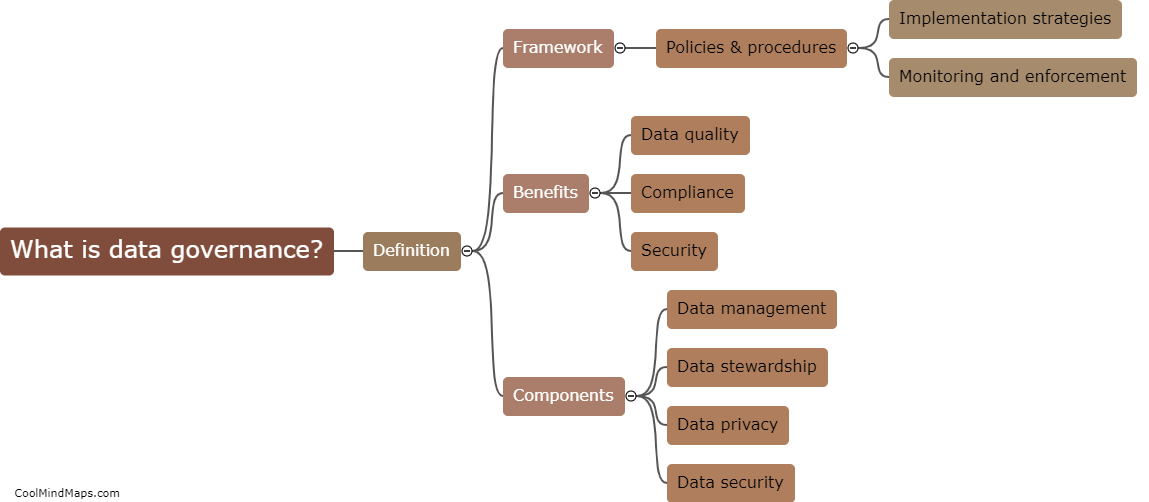
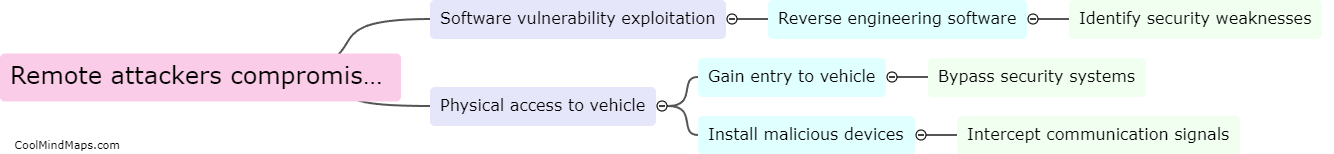
How can remote attackers compromise vehicle security?
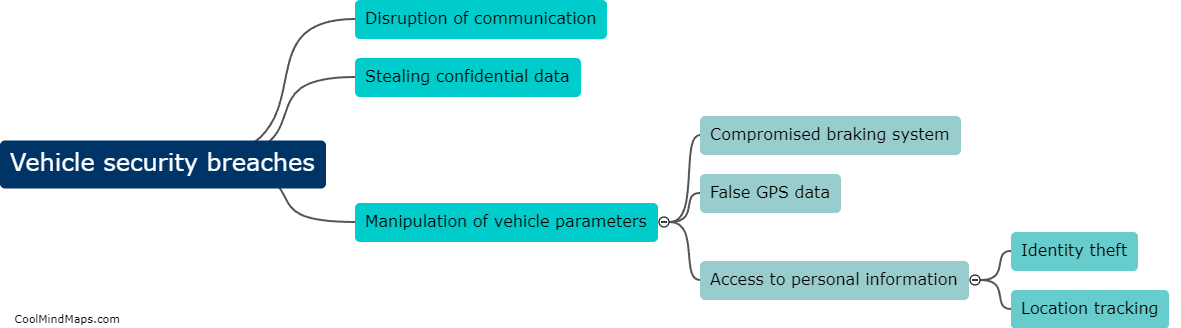
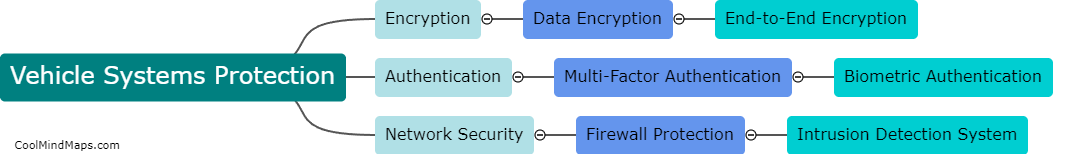
Remote attackers can compromise vehicle security through various means, such as exploiting vulnerabilities in the vehicle's software and firmware, hacking into wireless communication systems like Bluetooth or Wi-Fi, or compromising the vehicle's keyless entry system. Once attackers gain access to the vehicle's systems, they can potentially take control of critical functions like steering, braking, and acceleration, putting the driver and passengers at risk. Additionally, attackers can also steal personal data stored in the vehicle's infotainment system or use the vehicle's network connection to access other connected devices or systems. It is crucial for vehicle manufacturers to continuously update and secure their software and systems to prevent these types of attacks.
This mind map was published on 14 May 2024 and has been viewed 71 times.