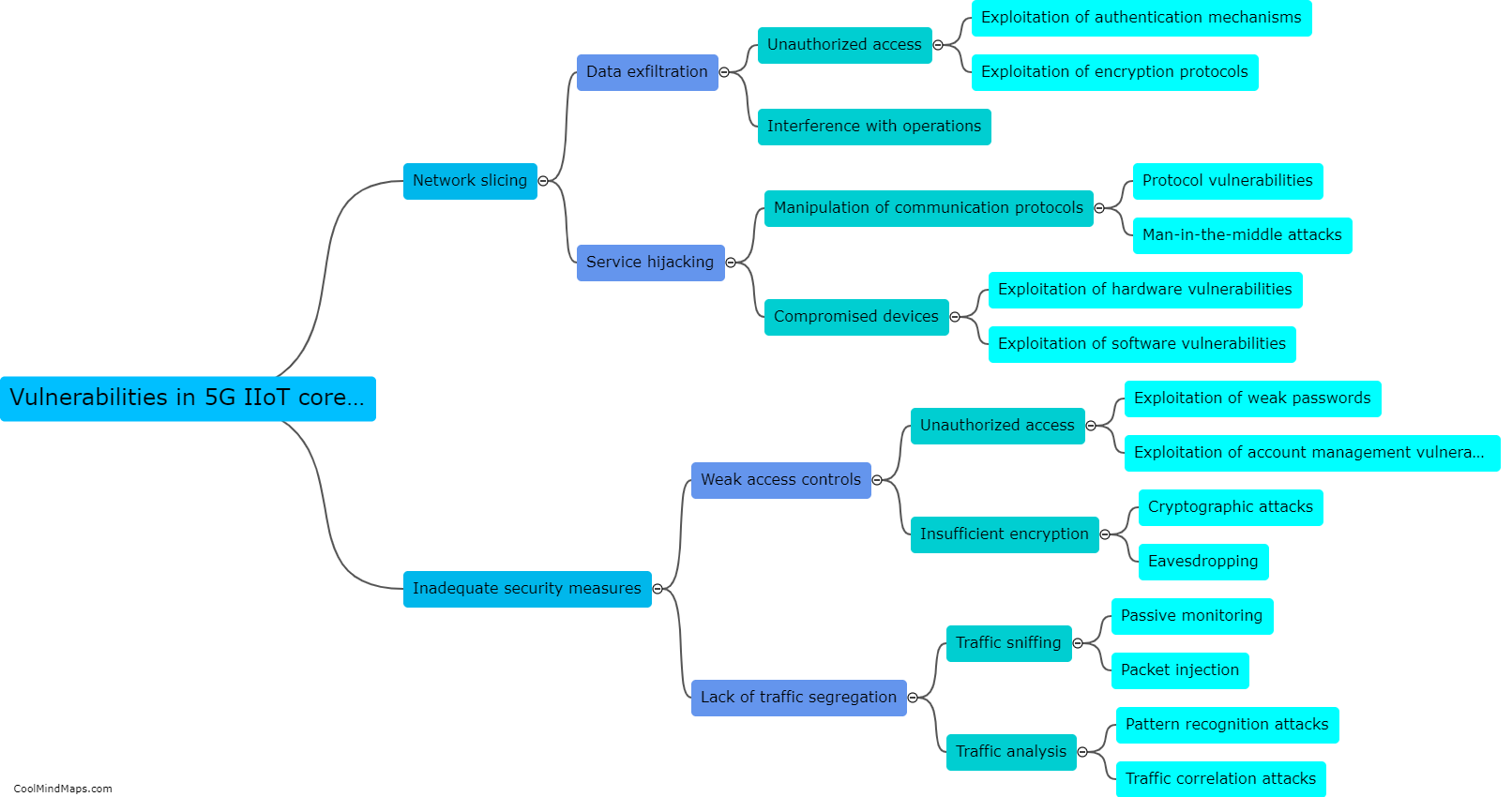
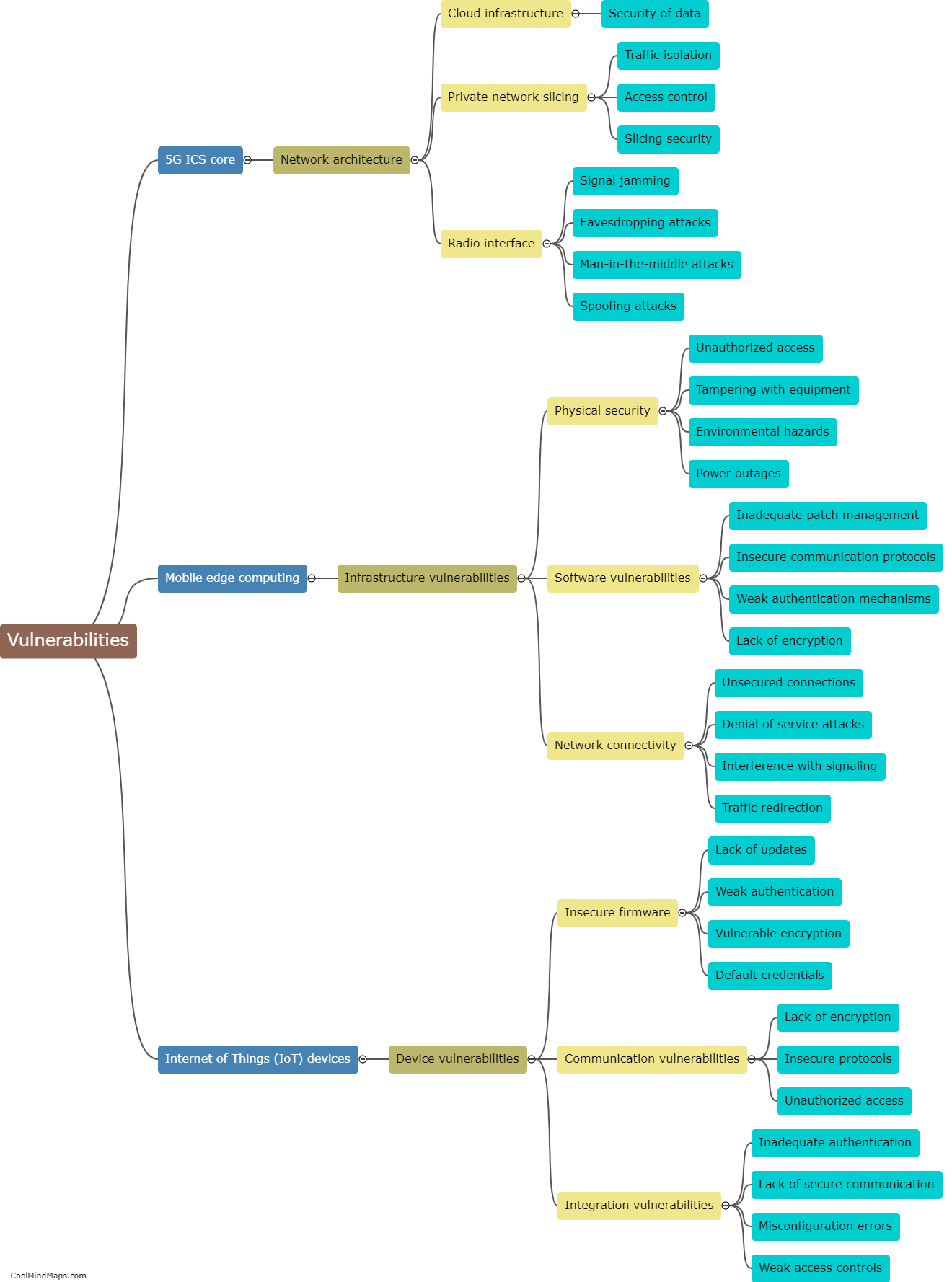
How can the campus network be secured against 5G IIoT attacks?
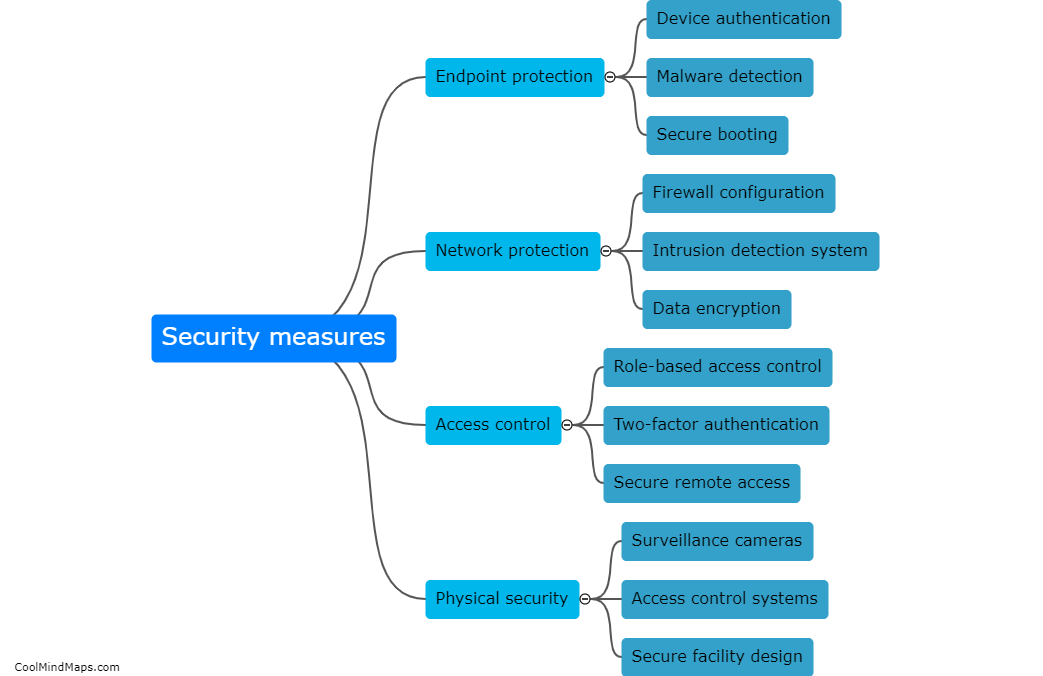
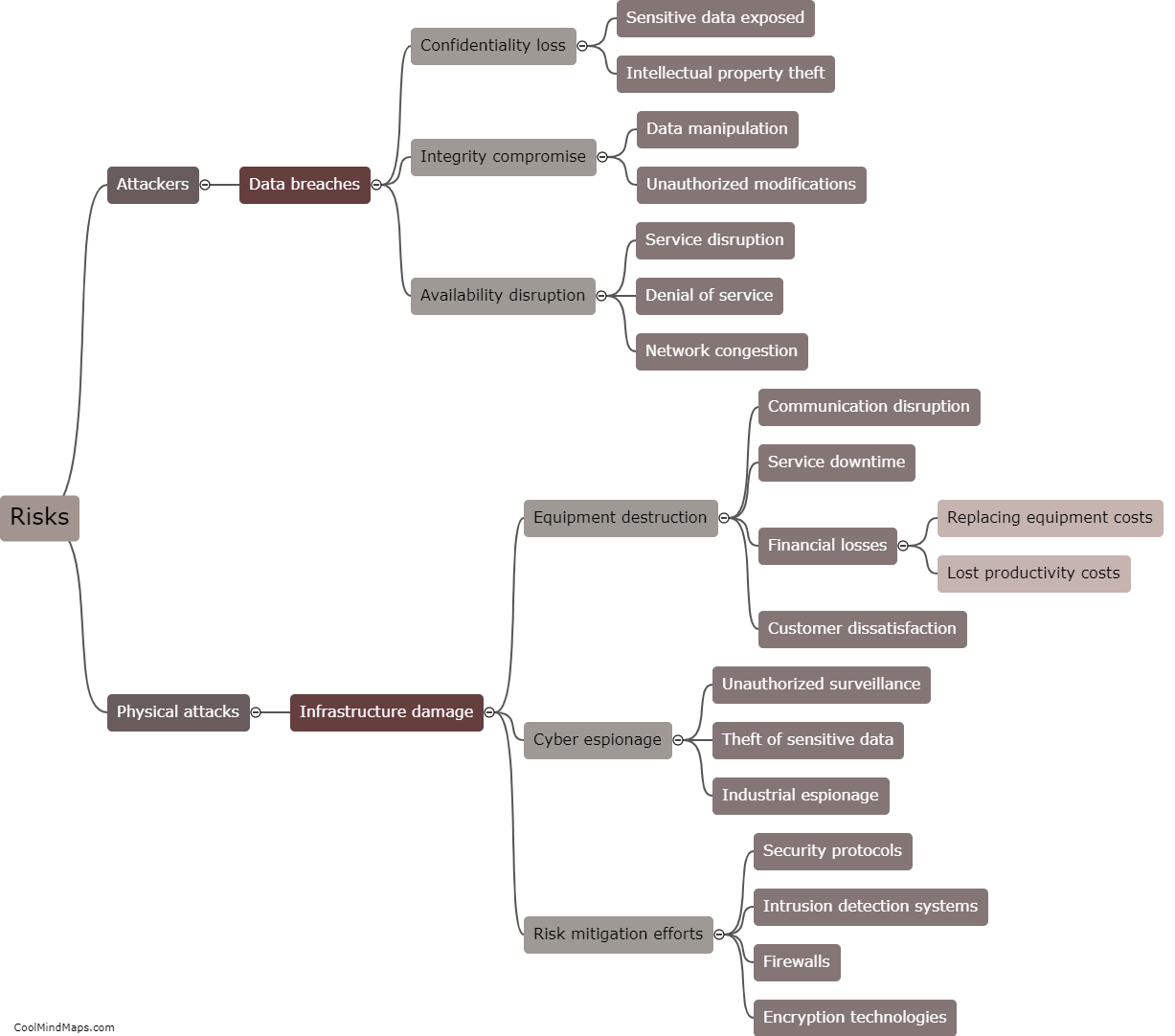
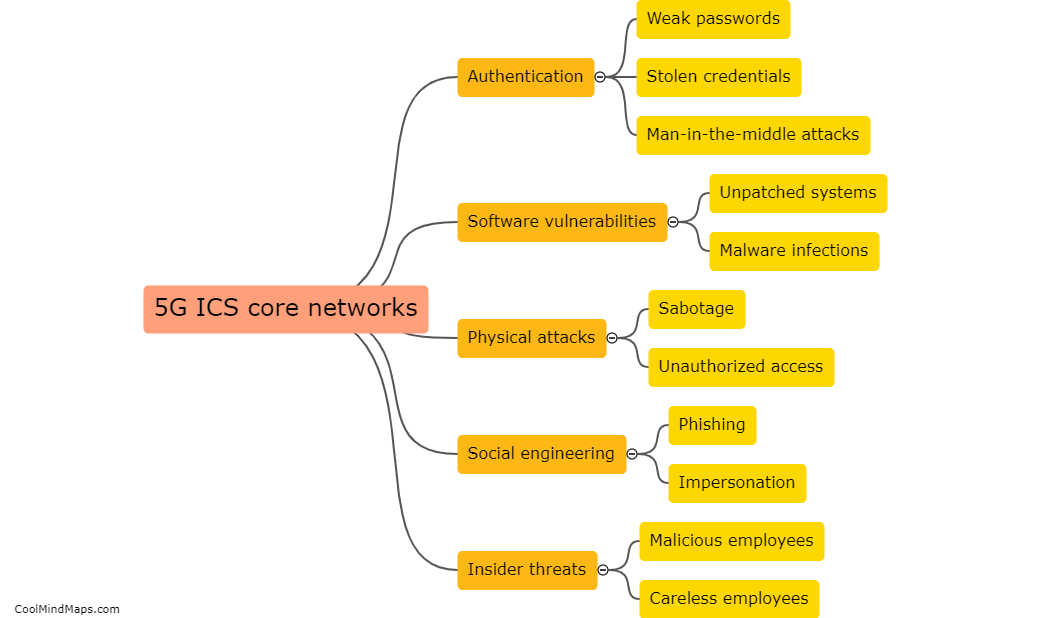
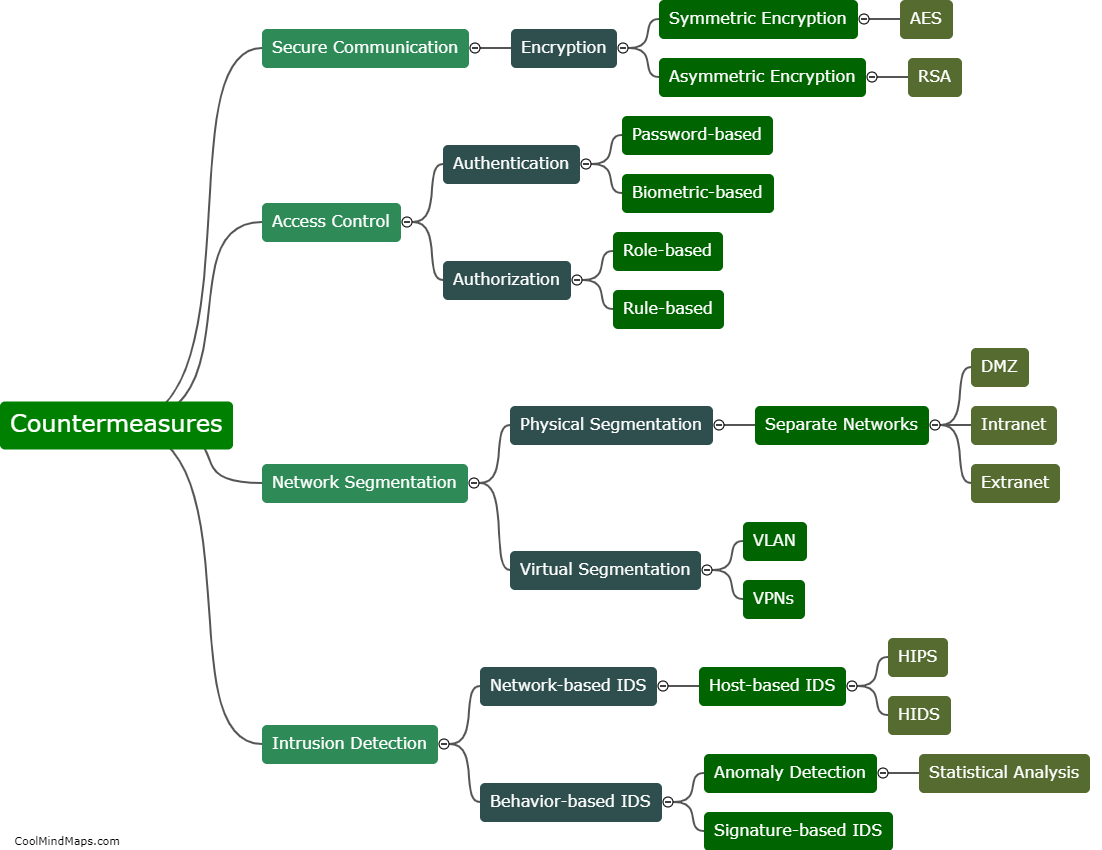
Securing the campus network against 5G IIoT attacks requires a multi-faceted approach. Firstly, implementing strong network encryption and authentication protocols can ensure that data transmitted between devices and the network remains secure and unbreachable. Utilizing advanced intrusion detection and prevention systems (IDPS) can also help in identifying and mitigating potential threats. Developing and enforcing robust access control policies, including proper authentication and authorization mechanisms, can restrict unauthorized devices or users from accessing the network. Regular security audits and vulnerability assessments should be conducted to identify and address any weaknesses in the network infrastructure. Additionally, educating the campus community about cybersecurity best practices can help in reducing human errors and raising awareness about potential security threats. By adopting these measures, the campus network can be better safeguarded against 5G IIoT attacks.

This mind map was published on 27 January 2024 and has been viewed 93 times.