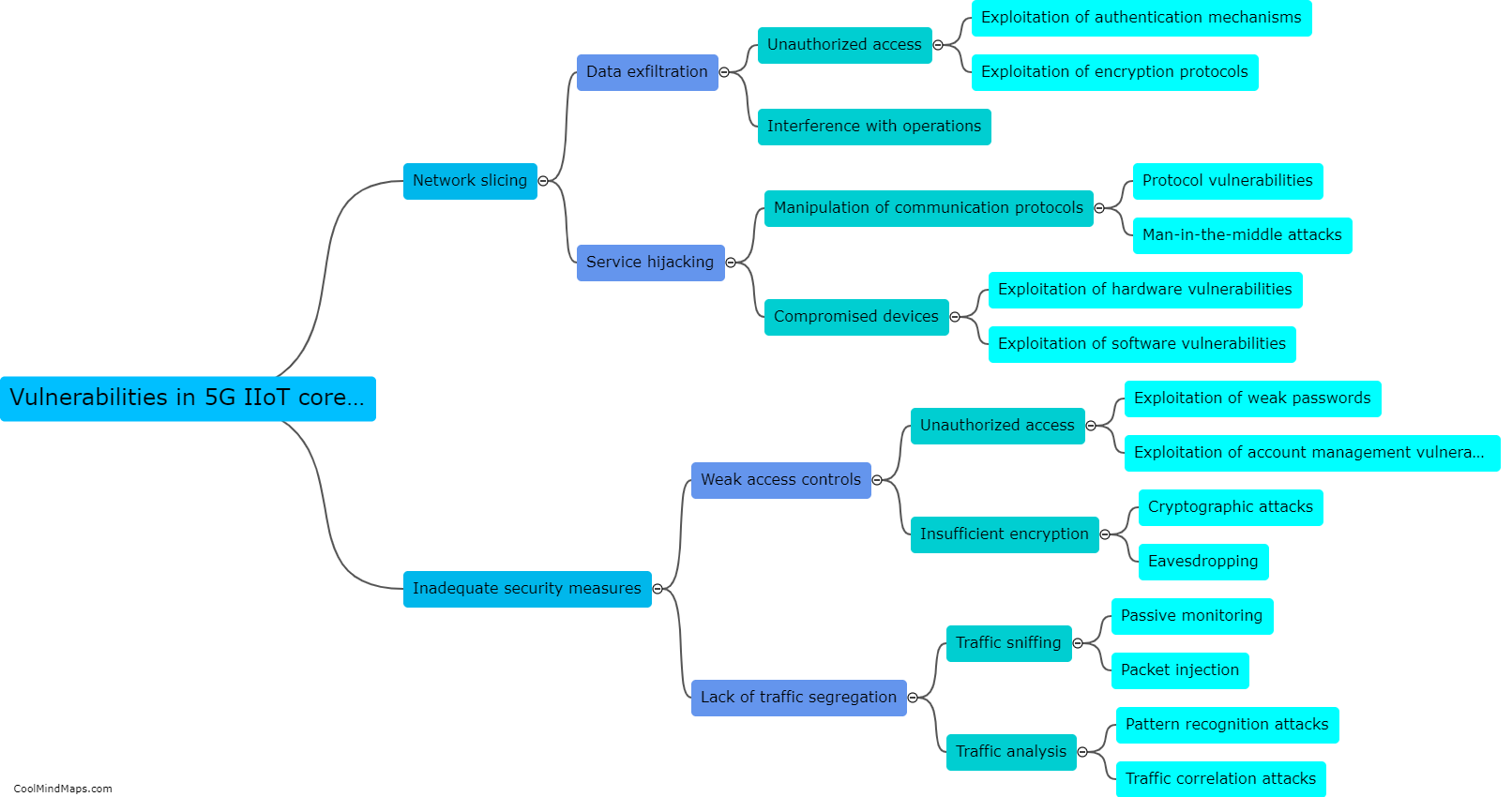
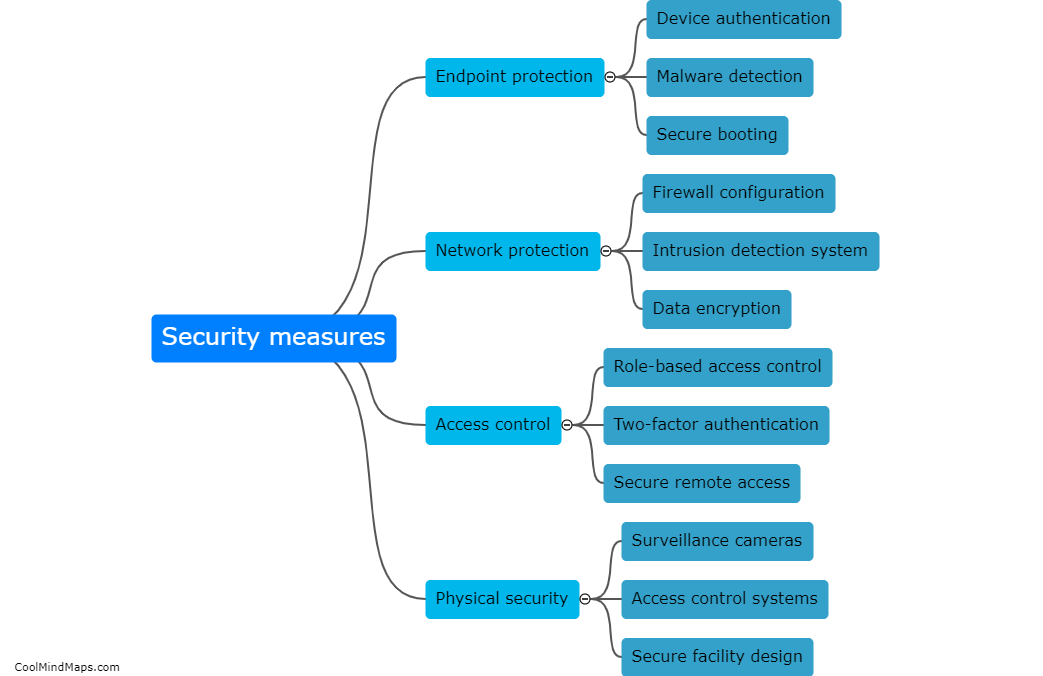
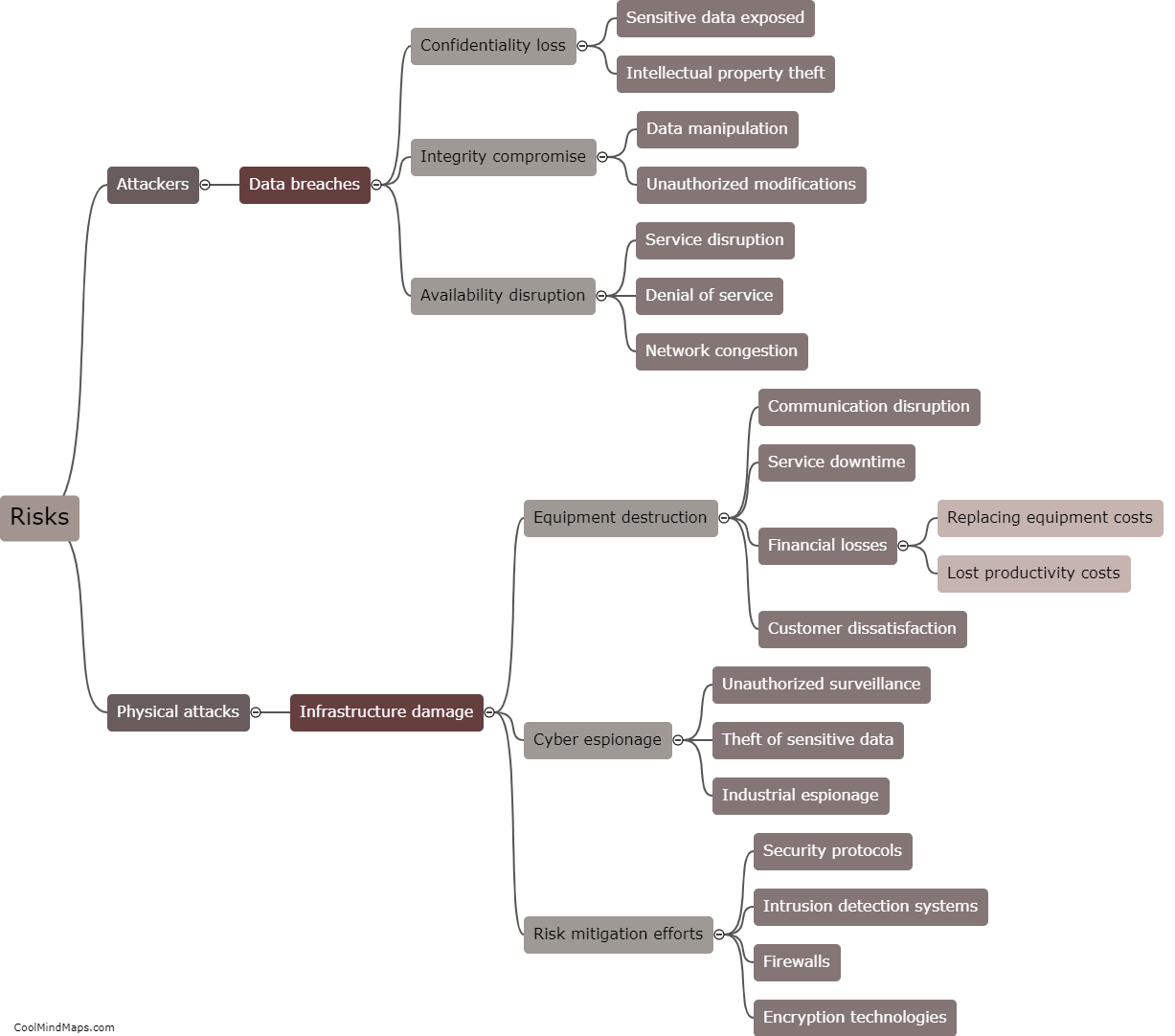
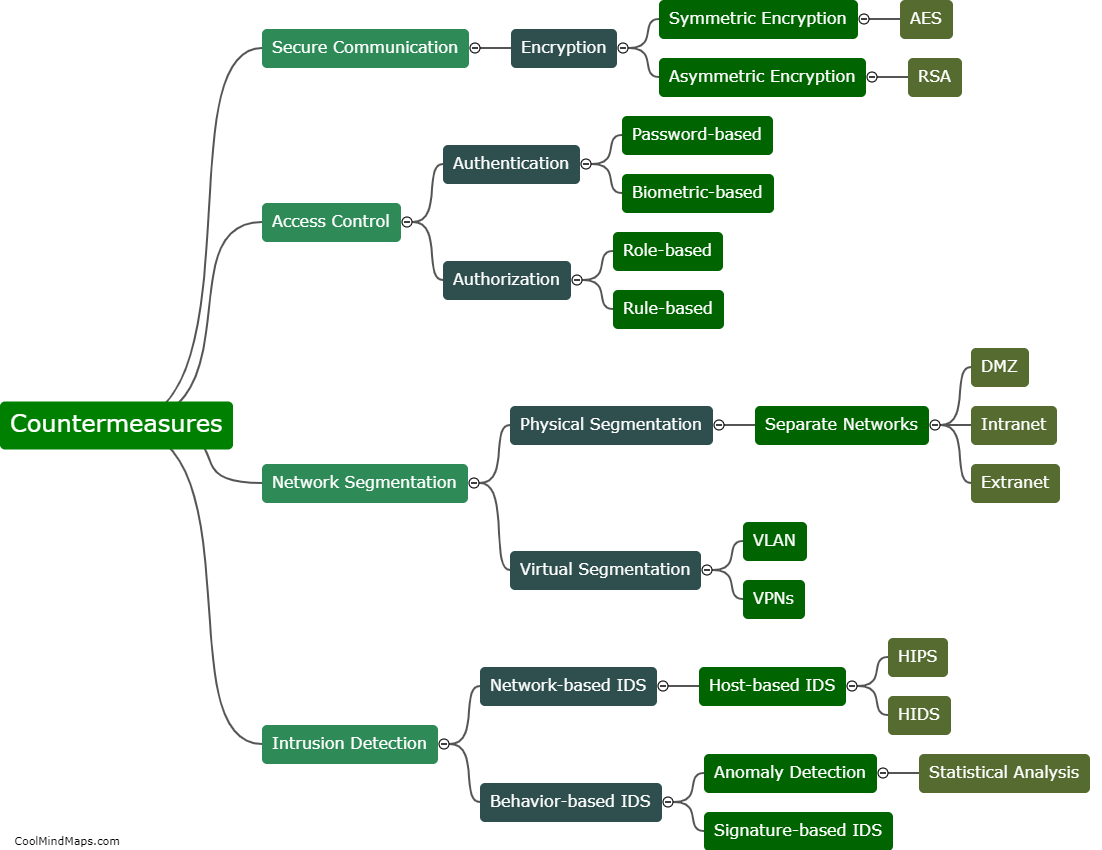
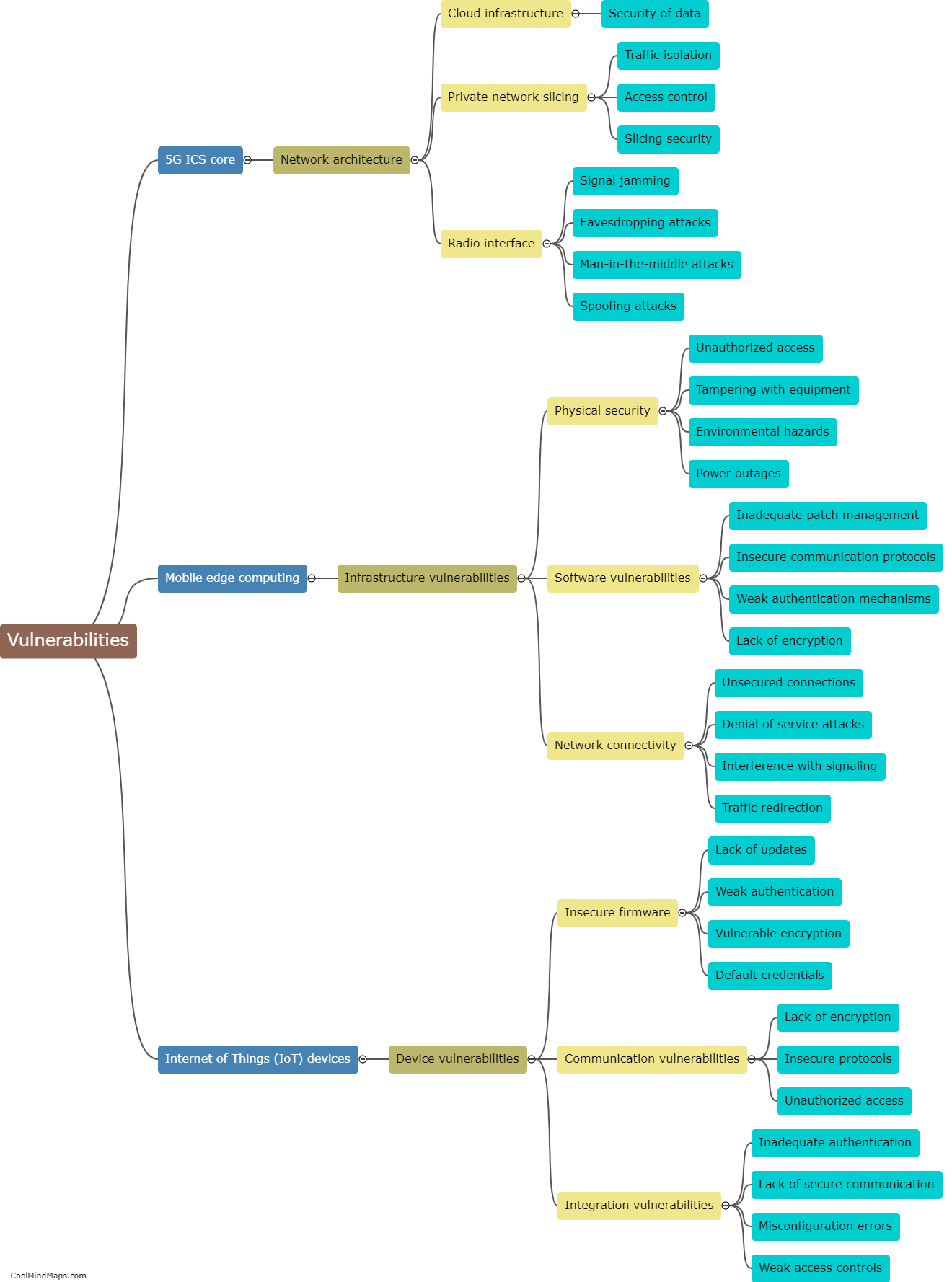
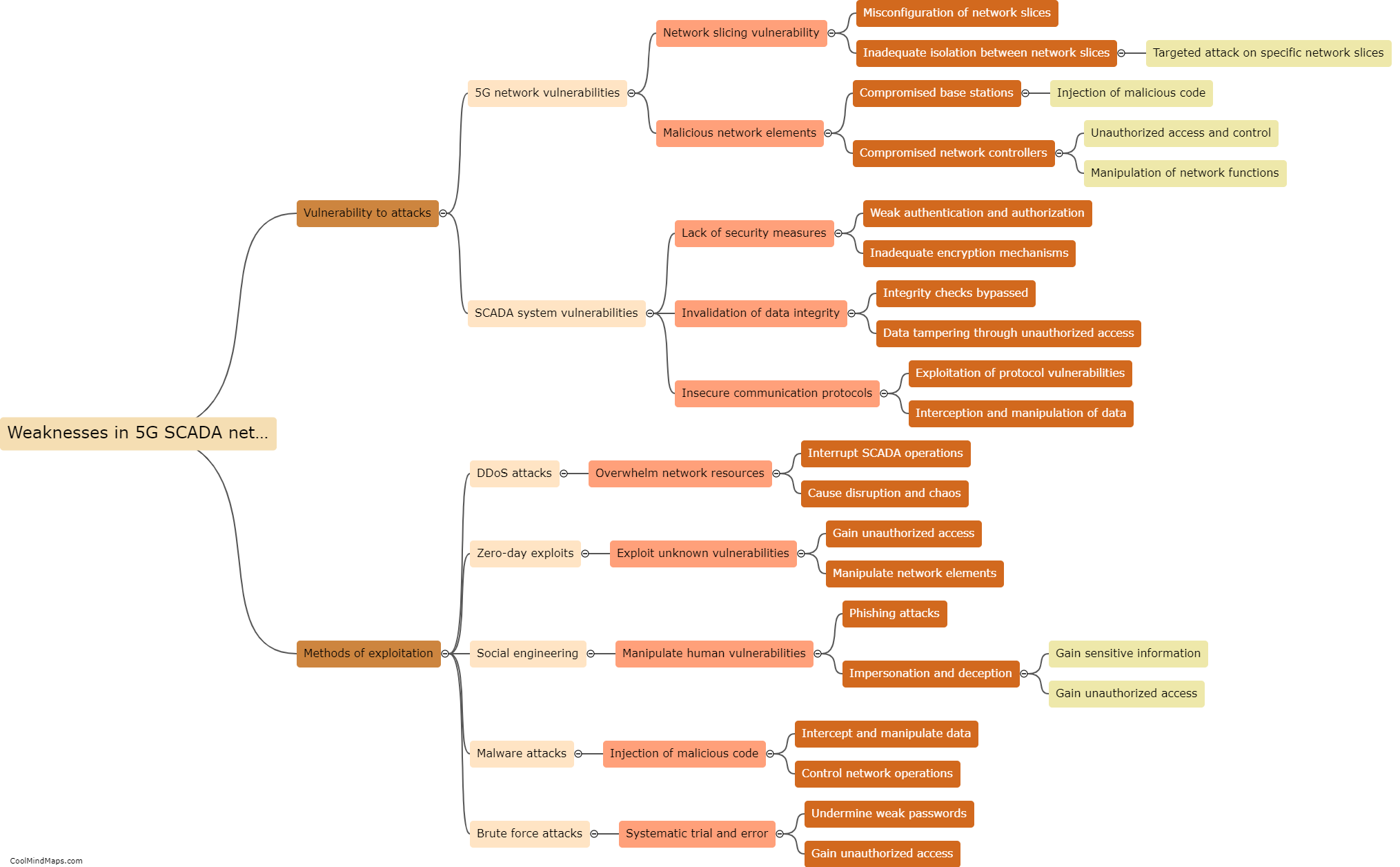
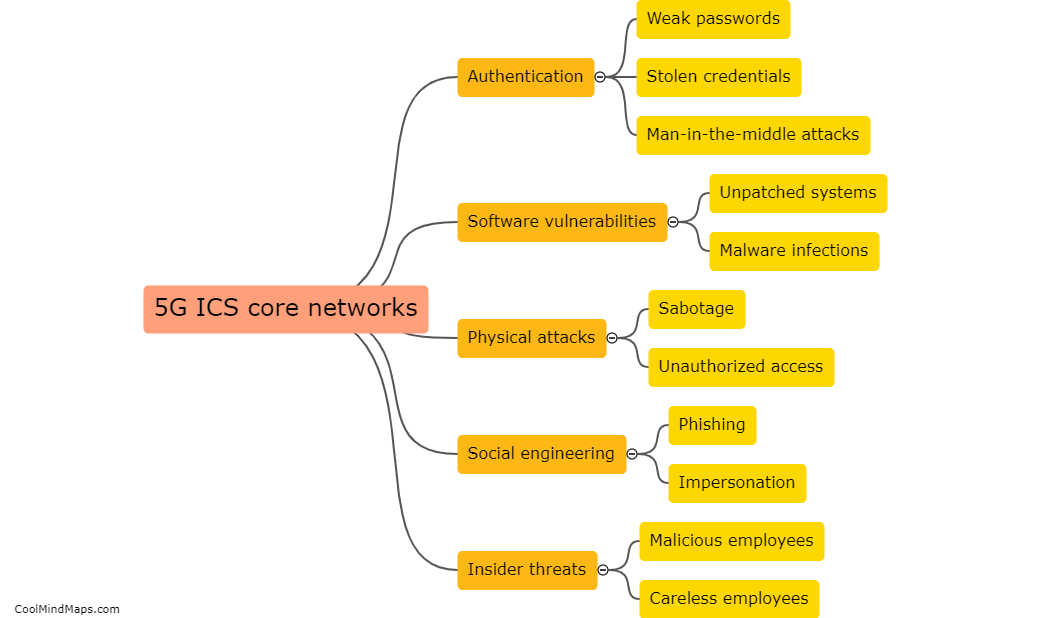
How can 5G ICS core networks be compromised?
5G ICS (Industrial Control Systems) core networks can be compromised through various avenues. One potential vulnerability is the reliance on interconnected devices and infrastructure, which increases the attack surface for cybercriminals. Weaknesses in network architecture, software vulnerabilities, or outdated firmware can also provide entry points for exploitation. Additionally, a lack of proper security measures, such as inadequate authentication protocols, encryption, and access controls, can leave ICS core networks susceptible to unauthorized access and compromise. Moreover, sophisticated techniques like social engineering or spear-phishing attacks targeting individuals with access to critical systems can be employed to gain unauthorized entry. Consequently, comprehensive security frameworks and continual monitoring are essential to address these potential risks and ensure the resilience of 5G ICS core networks.
This mind map was published on 27 January 2024 and has been viewed 101 times.