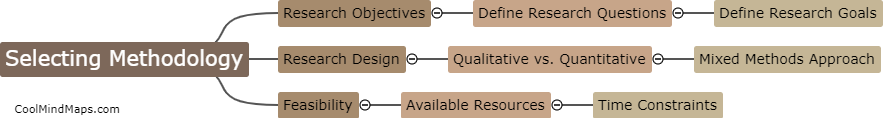
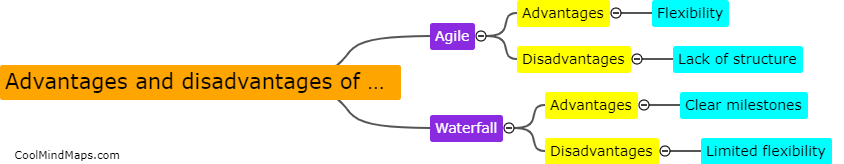
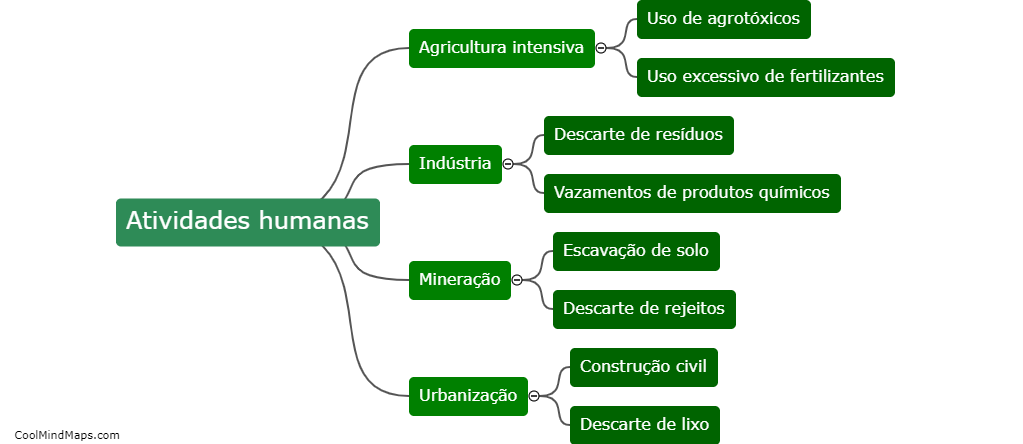
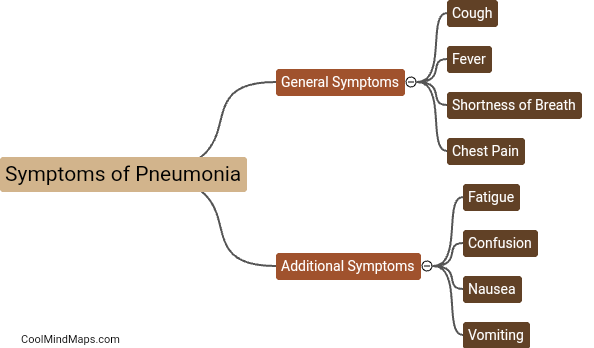
What are the post-installation steps for Keycloak setup?
After the Keycloak setup process is complete, there are several important post-installation steps that should be taken to ensure the system is secure and functioning properly. These steps include configuring user authentication and authorization settings, setting up user roles and permissions, enabling email verification for new users, configuring SSL for secure communication, configuring realm settings such as themes and login page customization, and setting up identity brokering for social media login options. It is also recommended to regularly update Keycloak to the latest version to benefit from security patches and new features. By following these post-installation steps, administrators can ensure a smooth and secure user authentication experience for their applications.
This mind map was published on 10 July 2024 and has been viewed 63 times.