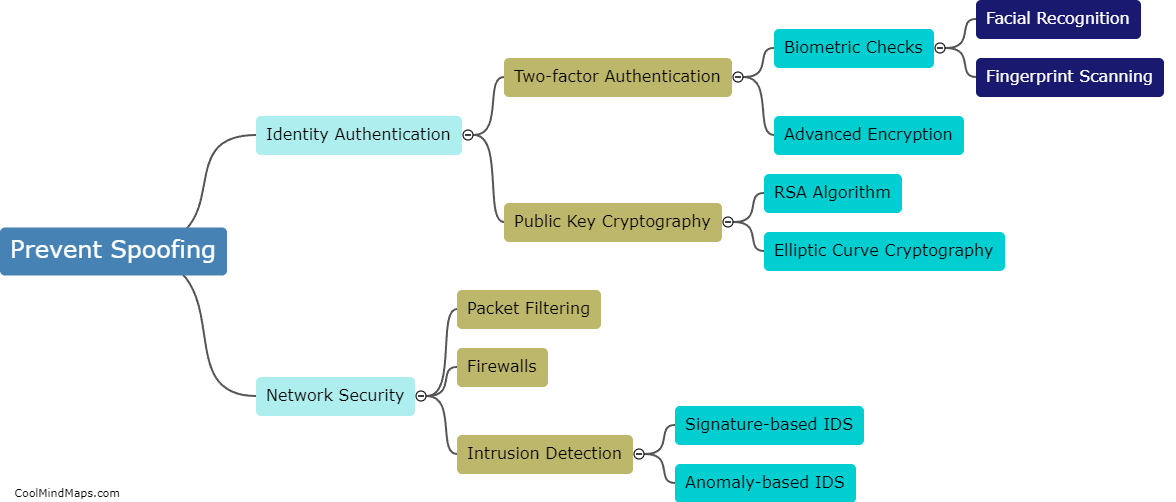
How can spoofing be prevented?
Spoofing can be prevented through a combination of technical and procedural measures. One approach is to configure firewalls and intrusion detection systems to identify and block IP addresses associated with spoofed traffic. Implementing cryptographic authentication and encryption mechanisms can also help prevent spoofing by verifying the identity of the sender and ensuring the integrity of the data. Additionally, organizations should provide education and training to employees to raise awareness of the risks associated with spoofing and to encourage best practices for securing network systems and data. Overall, a comprehensive security strategy that includes multiple layers of protection is necessary to prevent spoofing and safeguard against other types of cyber threats.
This mind map was published on 16 May 2023 and has been viewed 104 times.