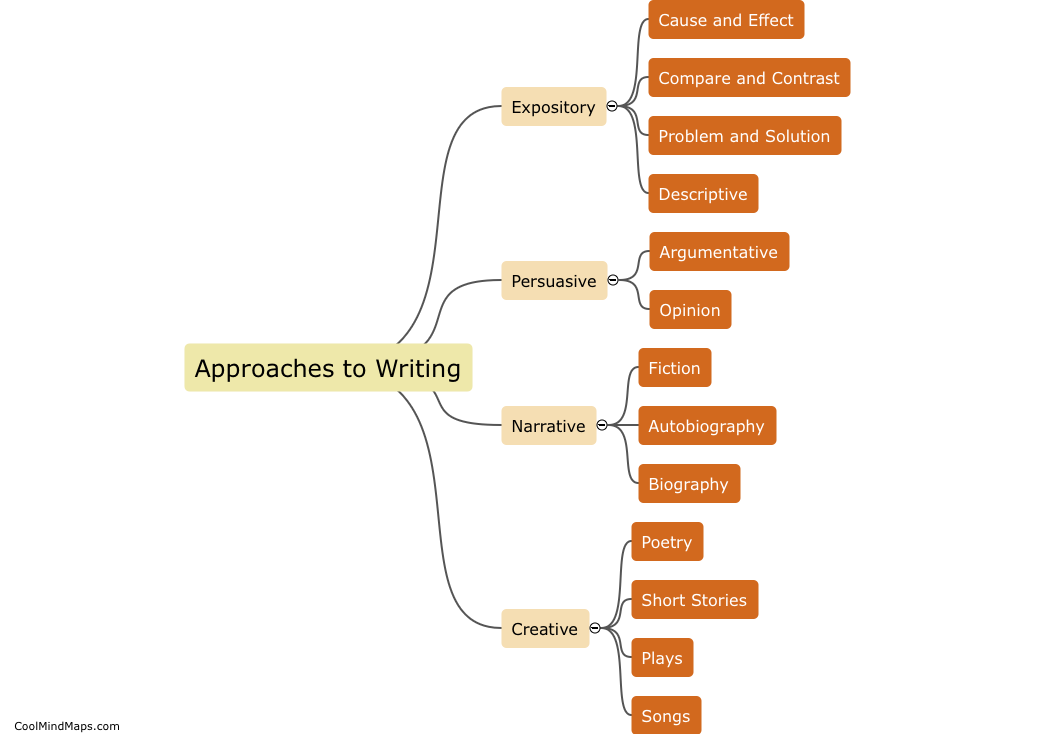
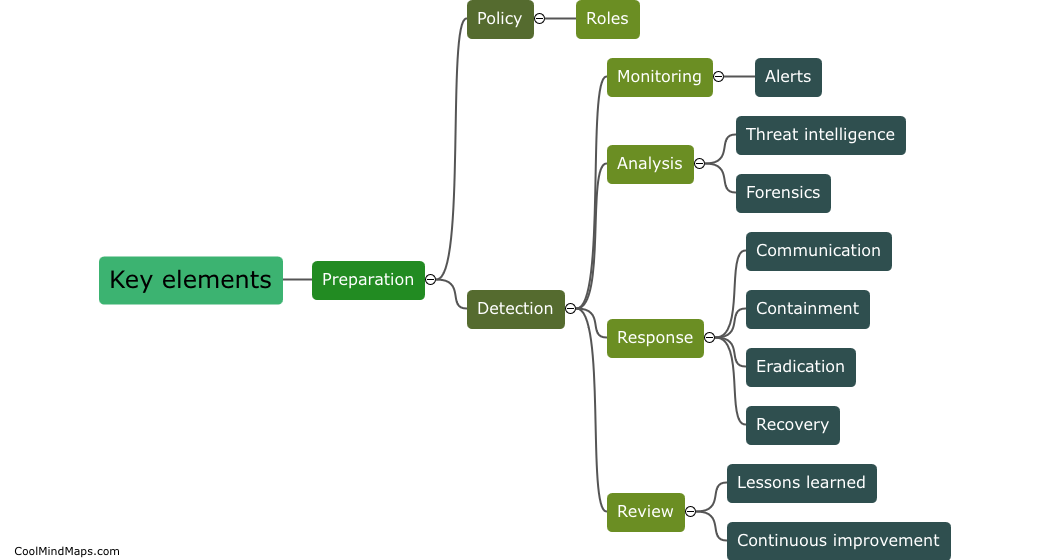
What strategies can be implemented to mitigate identified risks in an information security risk management program?
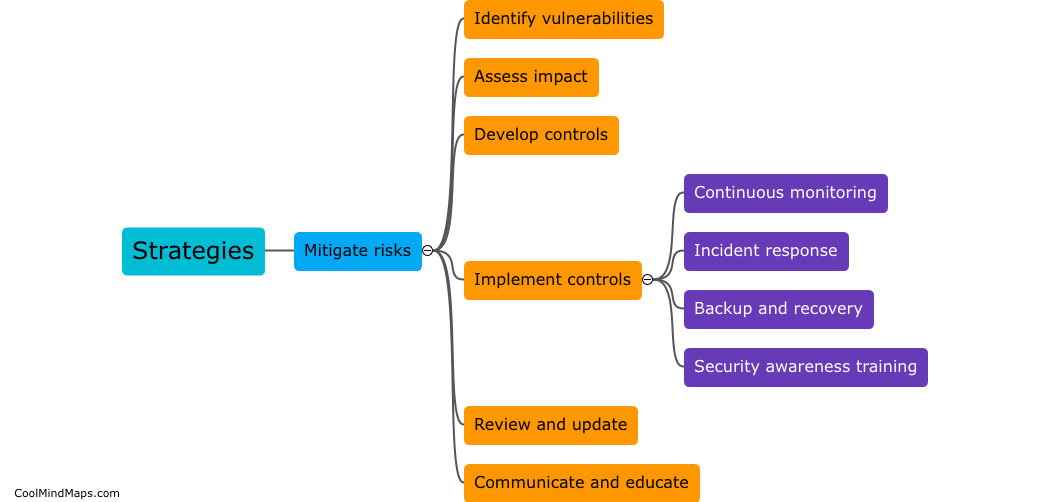
Implementing strategies to mitigate identified risks in an information security risk management program is crucial to protect sensitive data and ensure the continuity of operations. One strategy is to regularly conduct risk assessments to identify potential threats and vulnerabilities. This allows organizations to prioritize and allocate resources effectively. Implementing strong access controls and authentication mechanisms, such as two-factor authentication and role-based access controls, helps limit data exposure and unauthorized access. Regularly updating and patching software and systems reduces the risk of exploitation from known vulnerabilities. Additionally, implementing security awareness and training programs educates employees about potential risks and enables them to adopt best practices. Maintaining a comprehensive incident response plan helps organizations respond swiftly and effectively in the event of a security breach. By incorporating these strategies, organizations can build a robust information security risk management program that minimizes risks and safeguards their valuable data and assets.
This mind map was published on 15 February 2024 and has been viewed 43 times.