How does a SCADA security system work?
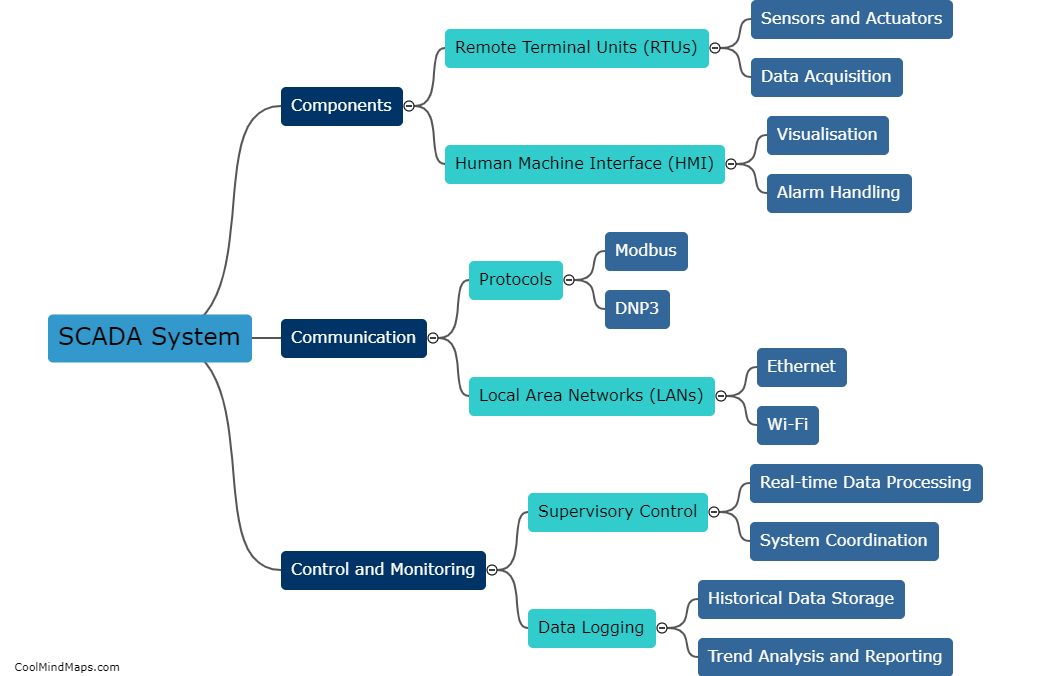
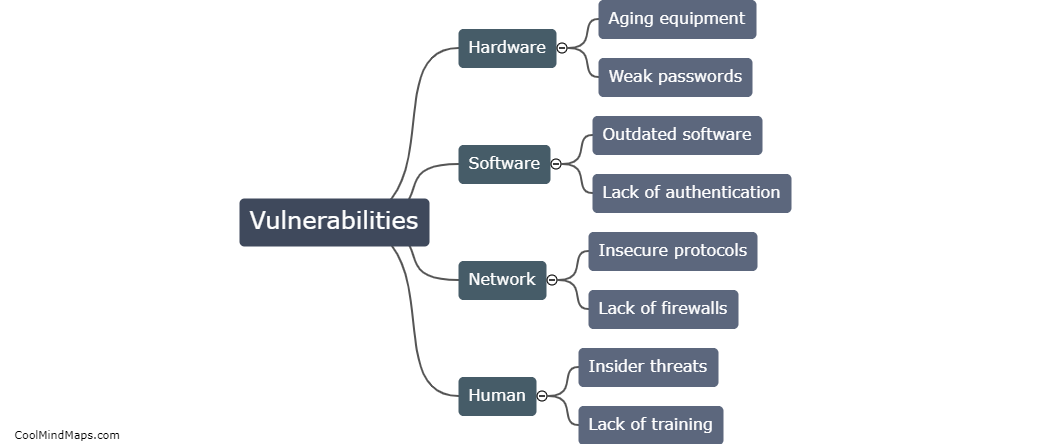
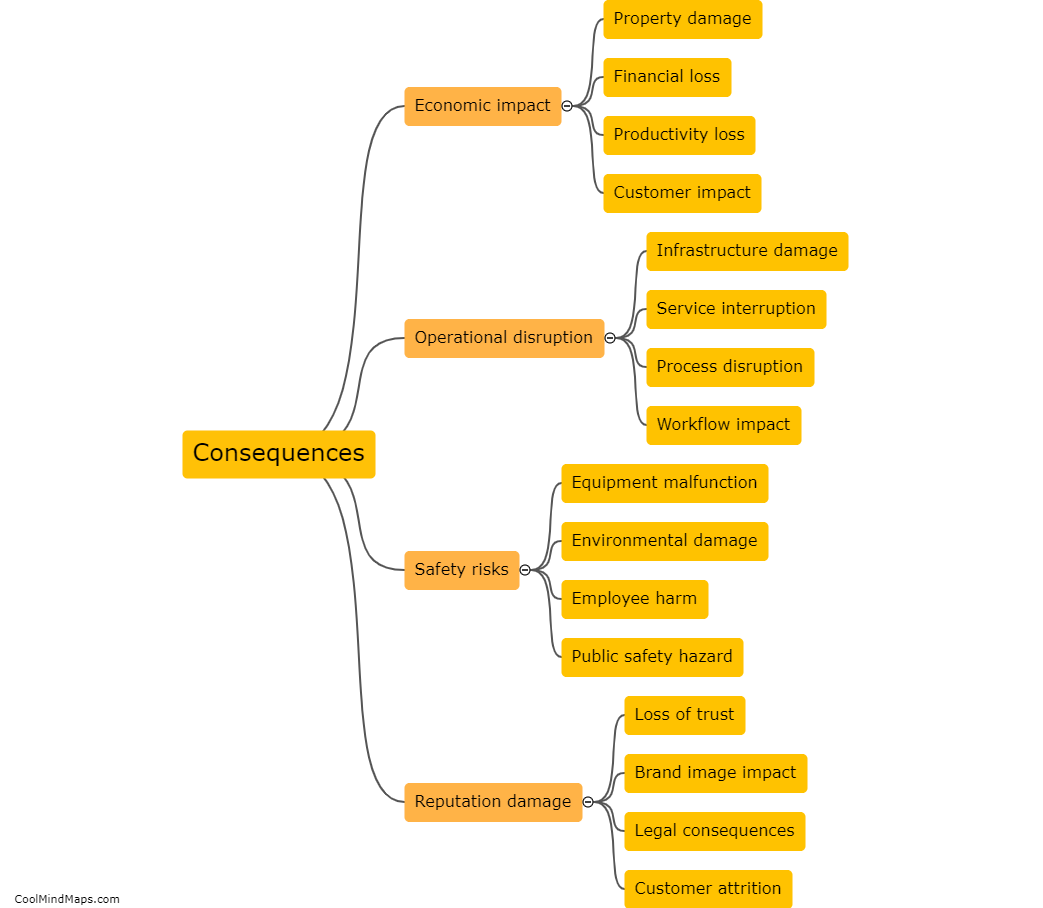
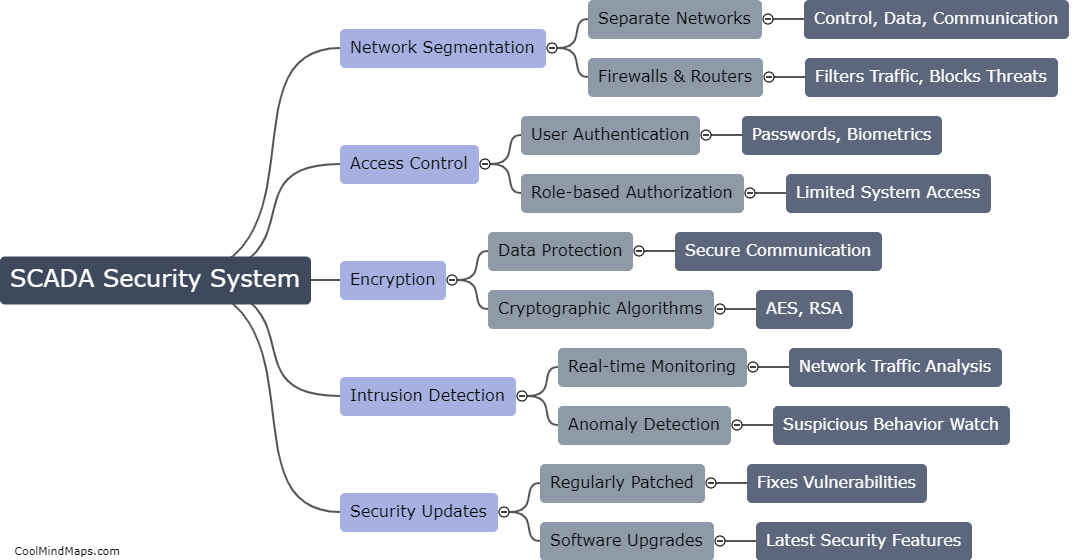
A SCADA (Supervisory Control and Data Acquisition) security system functions by implementing various measures to protect critical infrastructure and industrial control systems from cyber threats. It involves the integration of multiple layers of security controls to ensure the confidentiality, integrity, and availability of data and control functionalities. These systems typically employ firewalls, intrusion detection and prevention systems, access control mechanisms, and encrypted communication protocols to safeguard against unauthorized access, data manipulation, and other potential risks. Additionally, continuous monitoring and regular vulnerability assessments are conducted to identify and address any potential security vulnerabilities or cyber attacks, thereby maintaining the overall security and operational integrity of the SCADA system.
This mind map was published on 26 January 2024 and has been viewed 96 times.