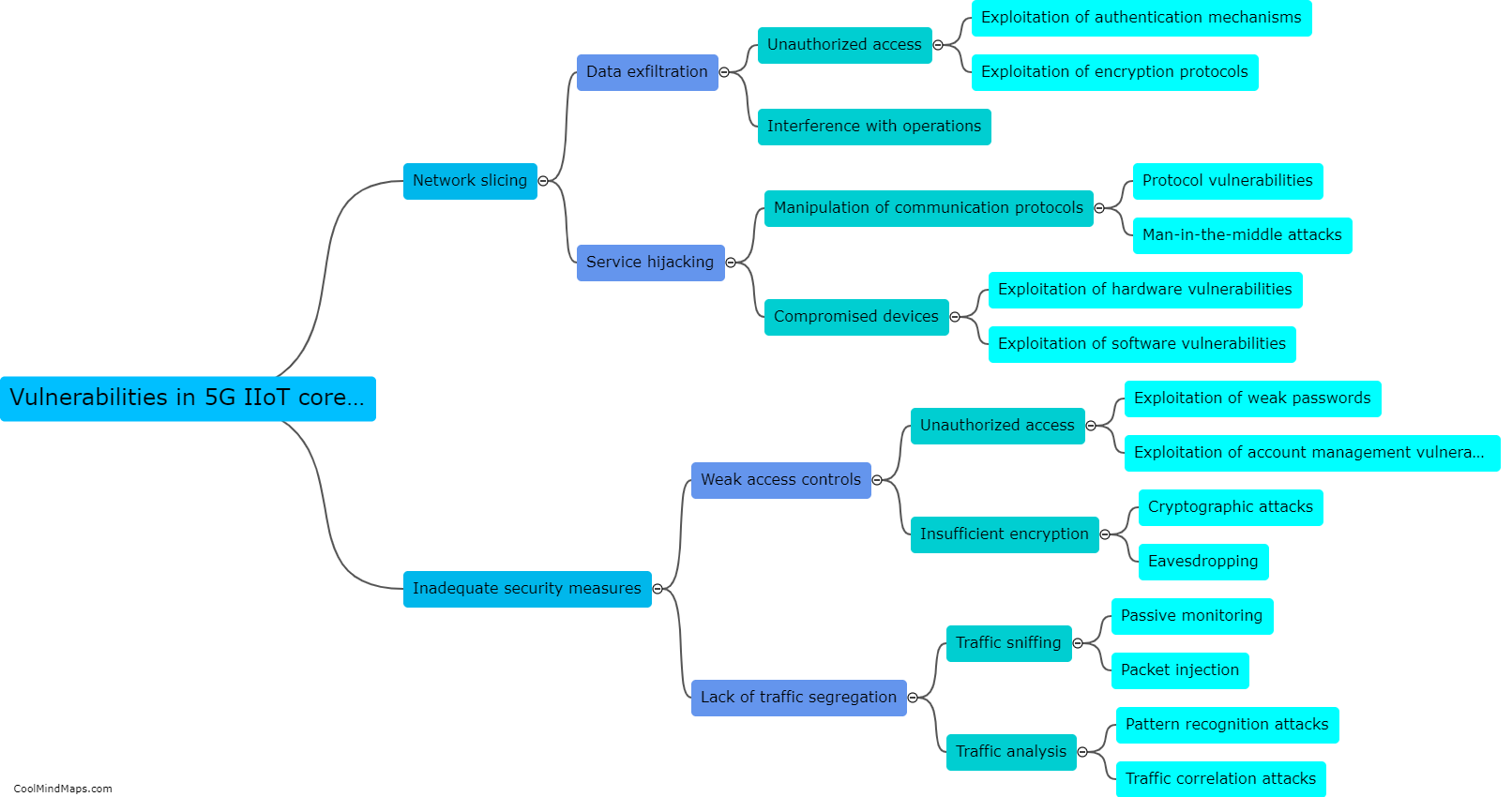
What security measures can be implemented to protect 5G IIoT core networks?
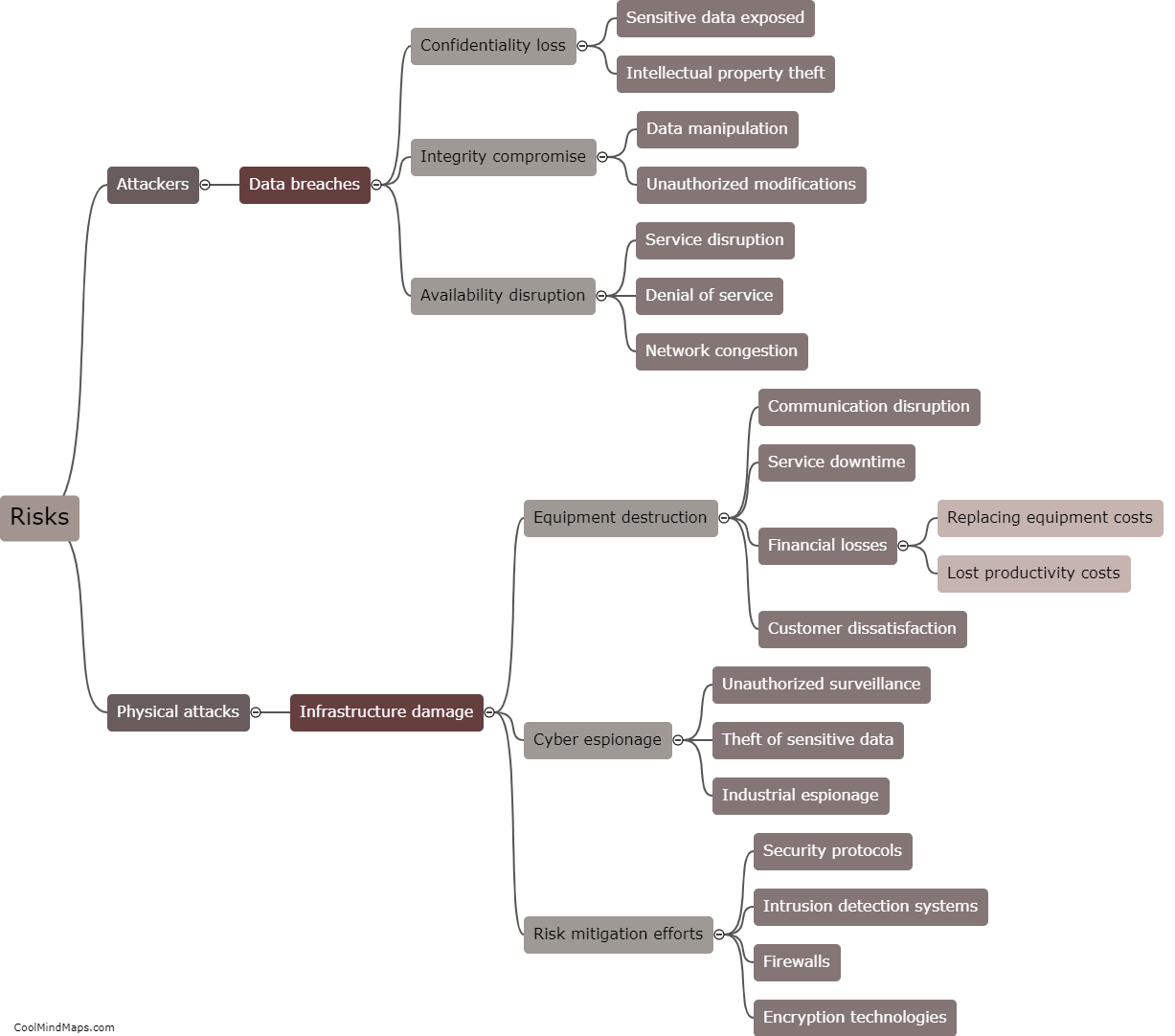
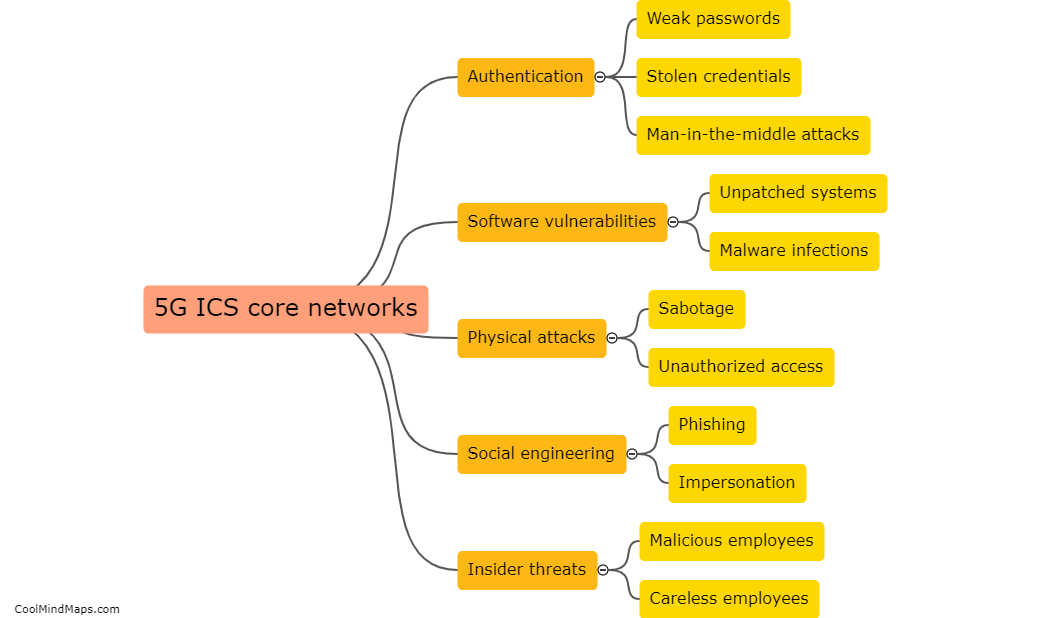
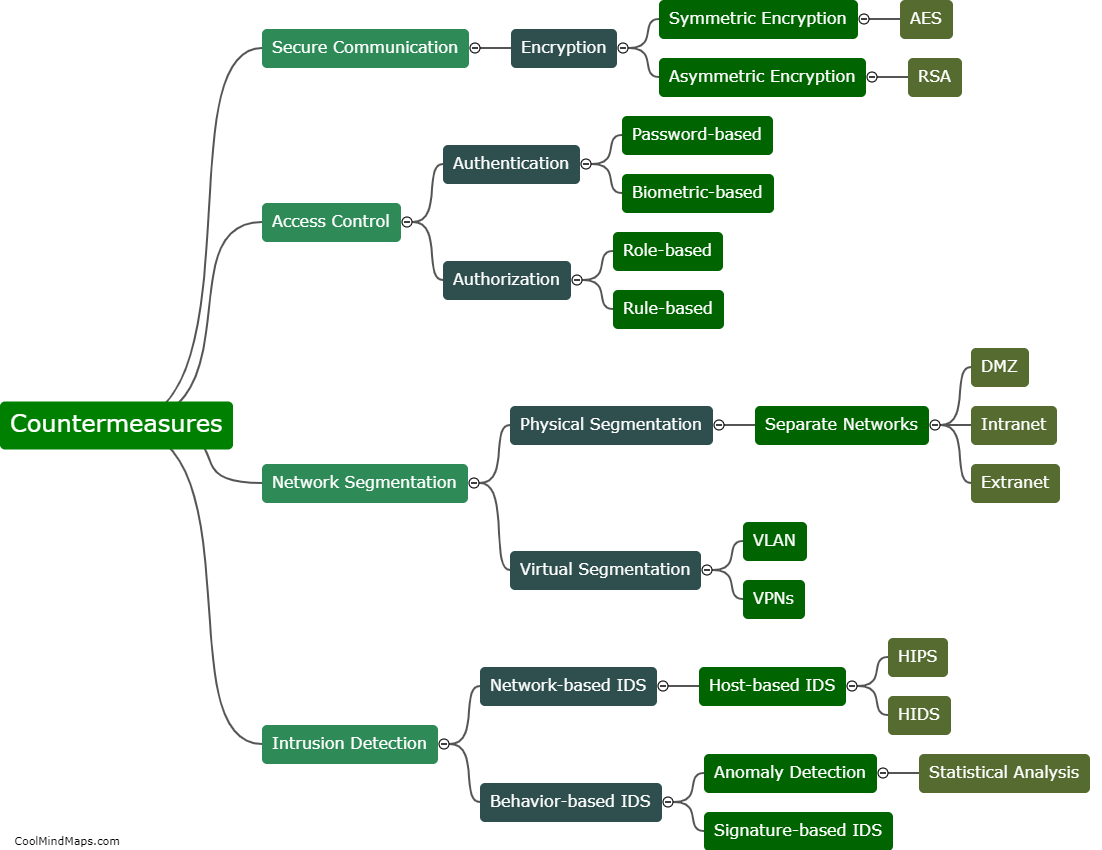
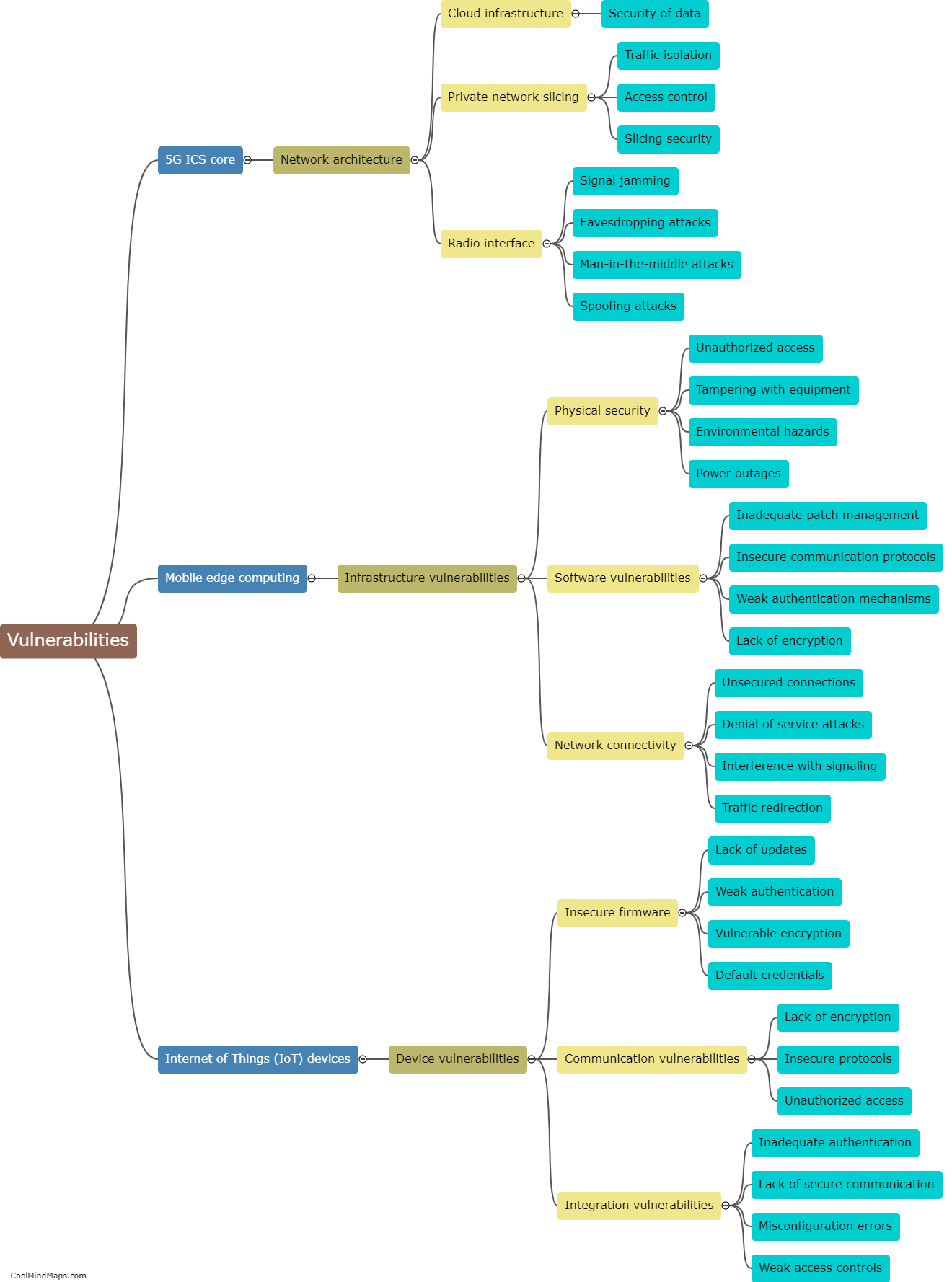
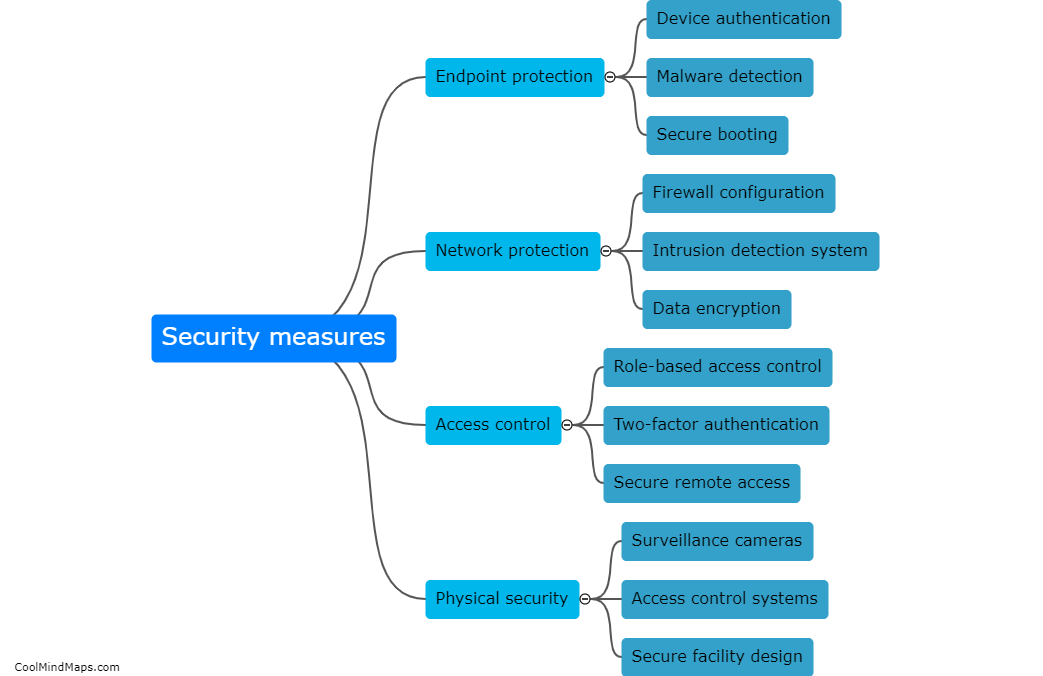
To protect 5G IIoT (Industrial Internet of Things) core networks, various security measures can be implemented. Firstly, strong authentication and access controls should be employed to ensure that only authorized devices and users can access the network. Multi-factor authentication, such as combining a password with a biometric scan, can add an extra layer of security. Additionally, encryption techniques, such as transport layer security (TLS), should be utilized to safeguard the data transmitted over the network. Network segmentation can help isolate critical components and sections of the network, preventing unauthorized access to sensitive areas. Intrusion detection and prevention systems (IDPS) can be deployed to detect and respond to any malicious activities or attacks. Regular security audits and updates should be conducted to address any vulnerabilities and ensure that the network's security measures remain robust and up to date. Finally, employee training and awareness programs about potential security threats can help prevent social engineering attacks and enhance overall security.
This mind map was published on 27 January 2024 and has been viewed 82 times.