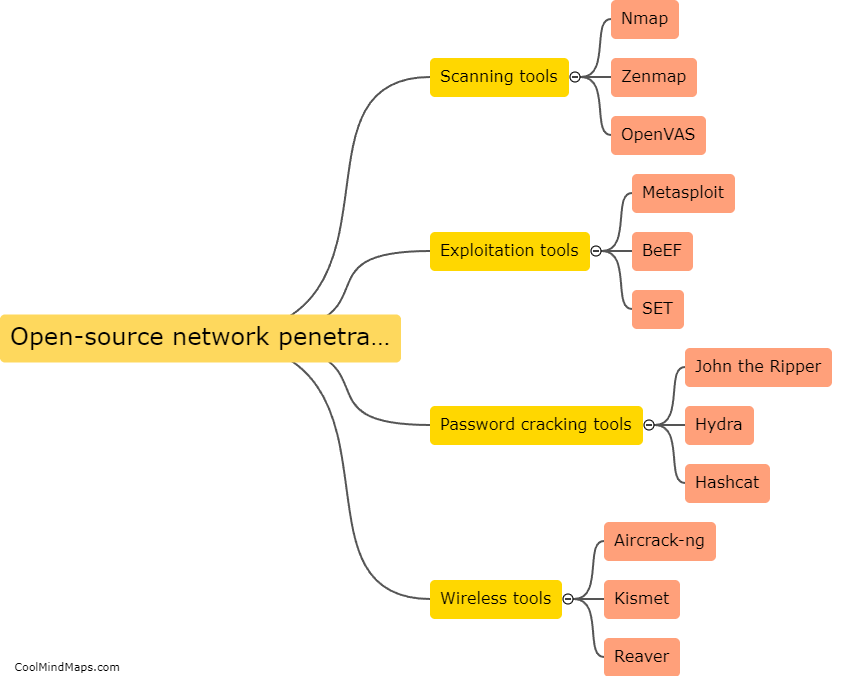
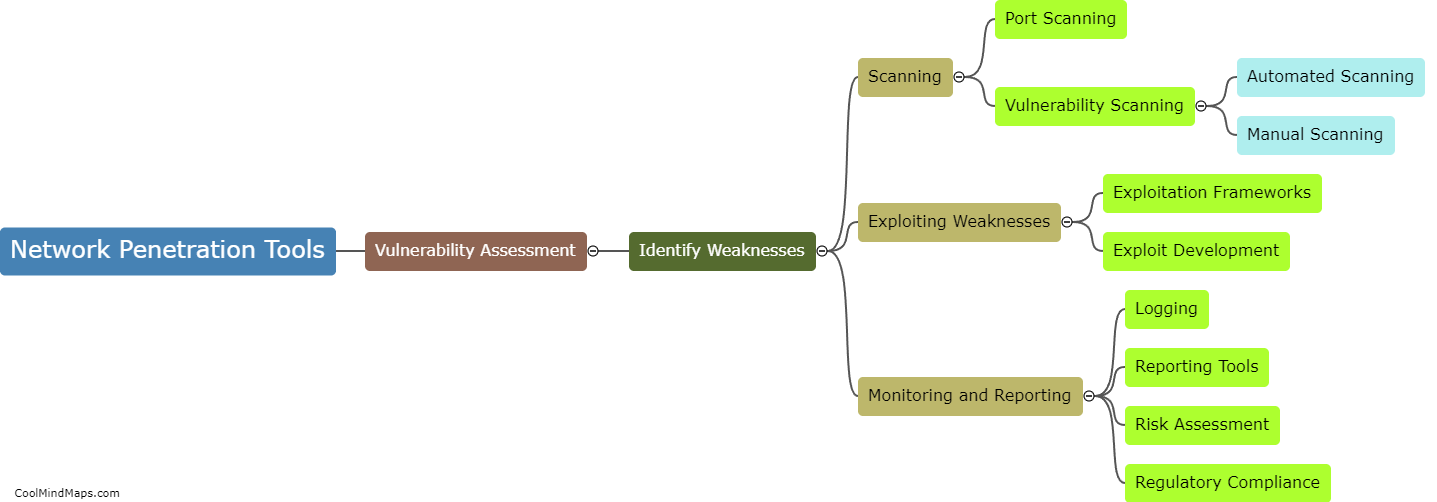
How can network penetration tools be used for vulnerability assessment?
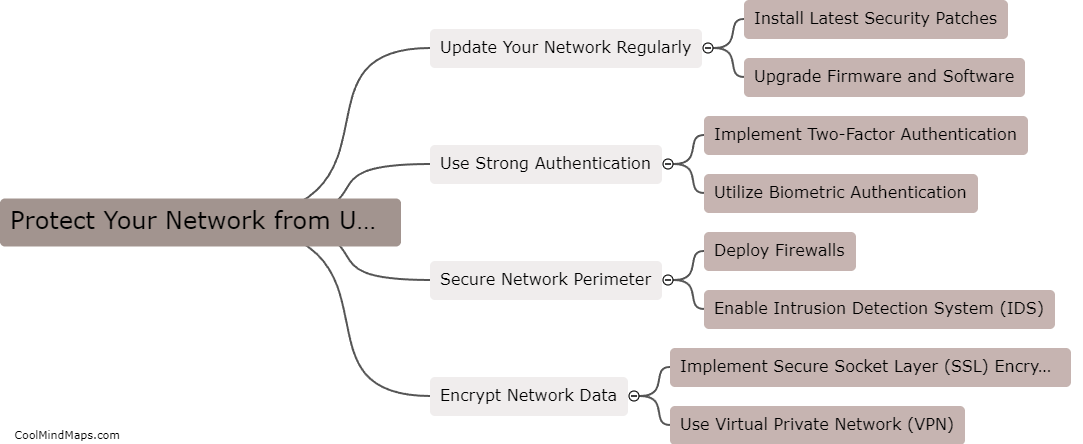
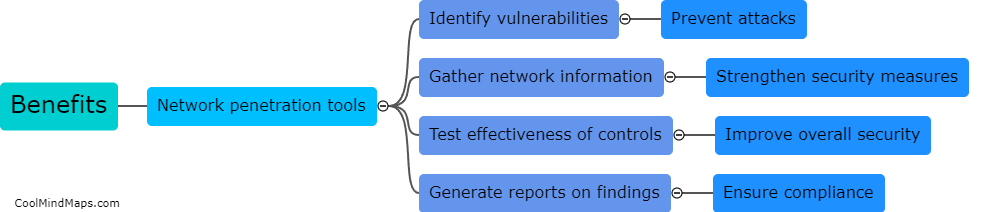
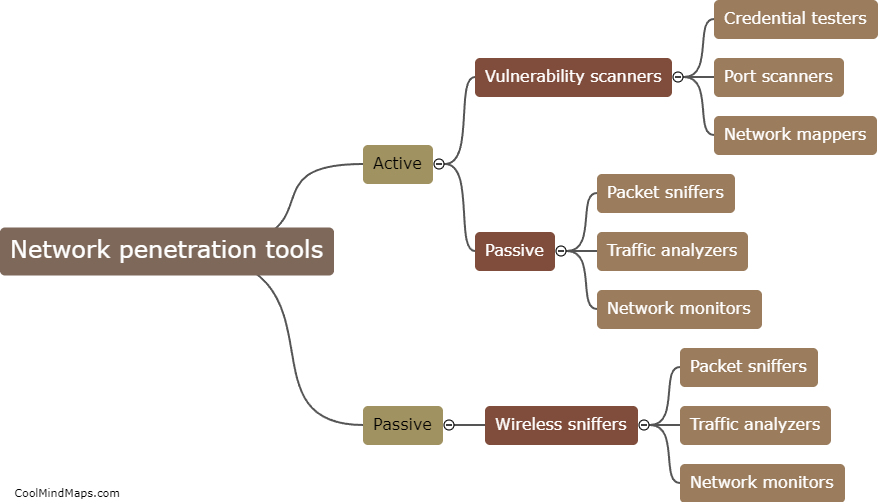
Network penetration tools can be highly effective in conducting vulnerability assessments as they provide a comprehensive evaluation of a network's security posture. These tools are designed to simulate real-world attacks and identify potential weaknesses or vulnerabilities in a network's infrastructure. By scanning for open ports, misconfigured devices, or outdated software, penetration tools can analyze the network for potential entry points that could be exploited by malicious actors. Additionally, these tools can perform detailed analysis and provide actionable recommendations to strengthen the network's security defenses. Overall, network penetration tools play a crucial role in identifying and mitigating vulnerabilities before any real-world attacks occur.
This mind map was published on 9 October 2023 and has been viewed 94 times.