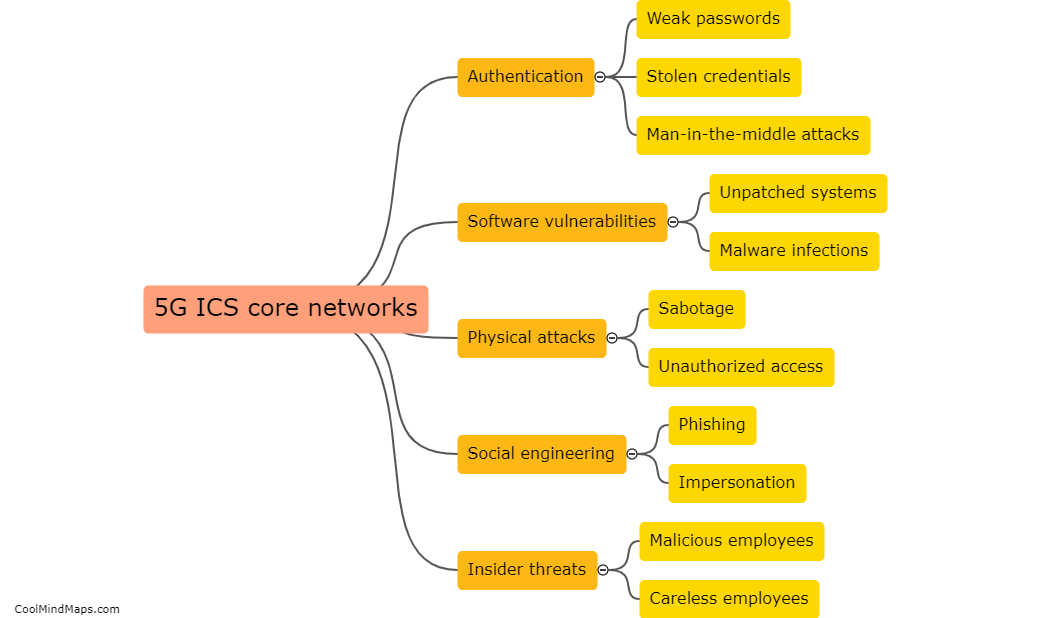
How can SCADA systems be targeted in 5G networks?
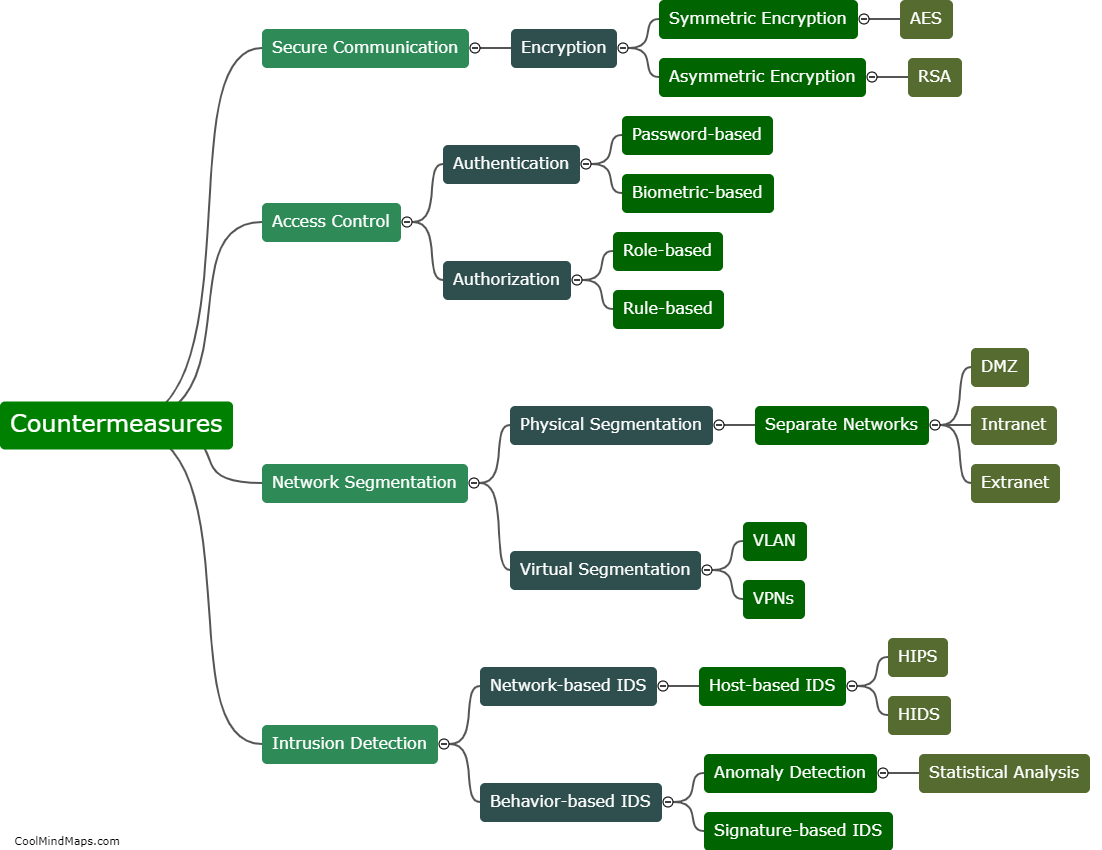
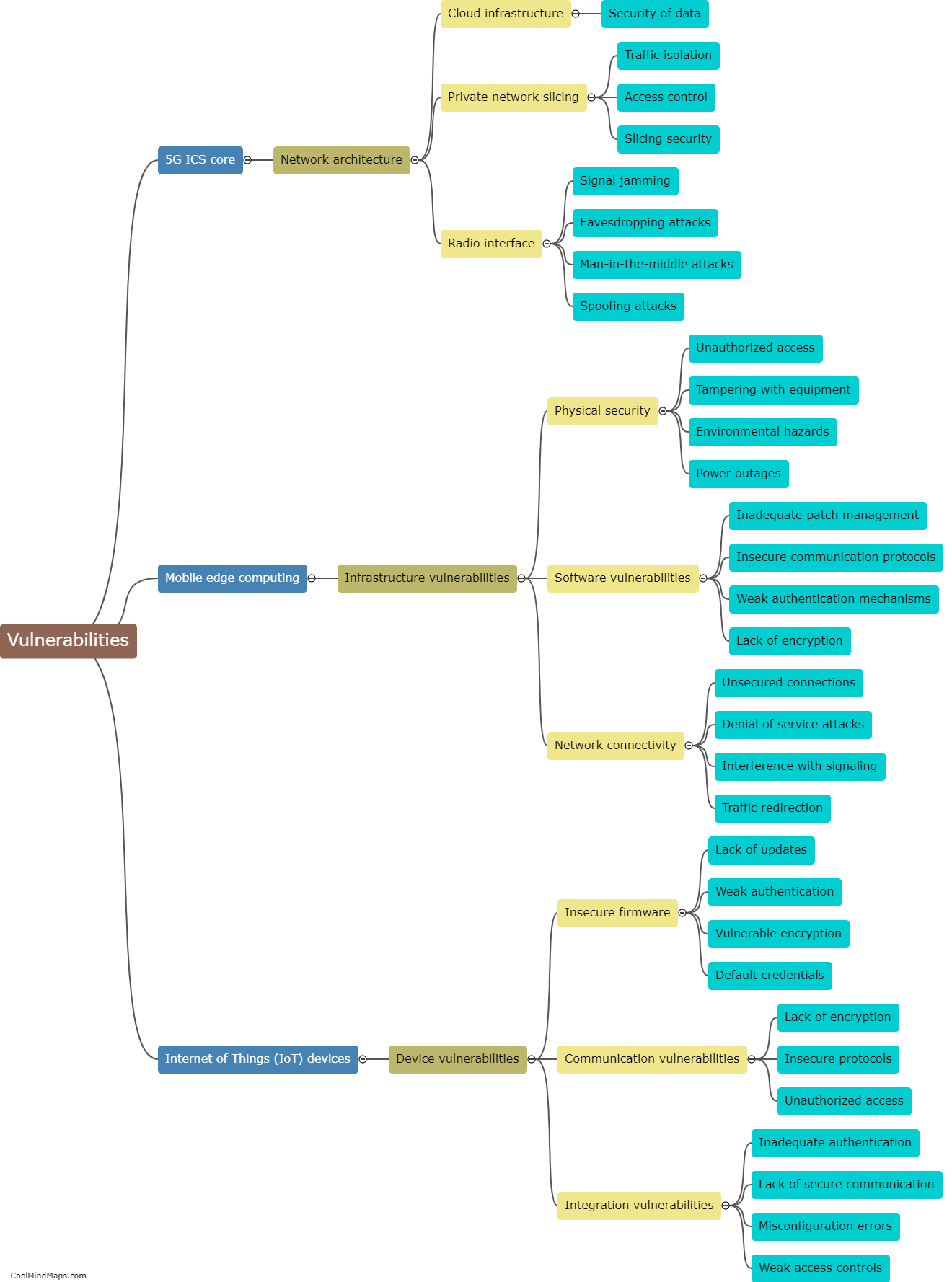
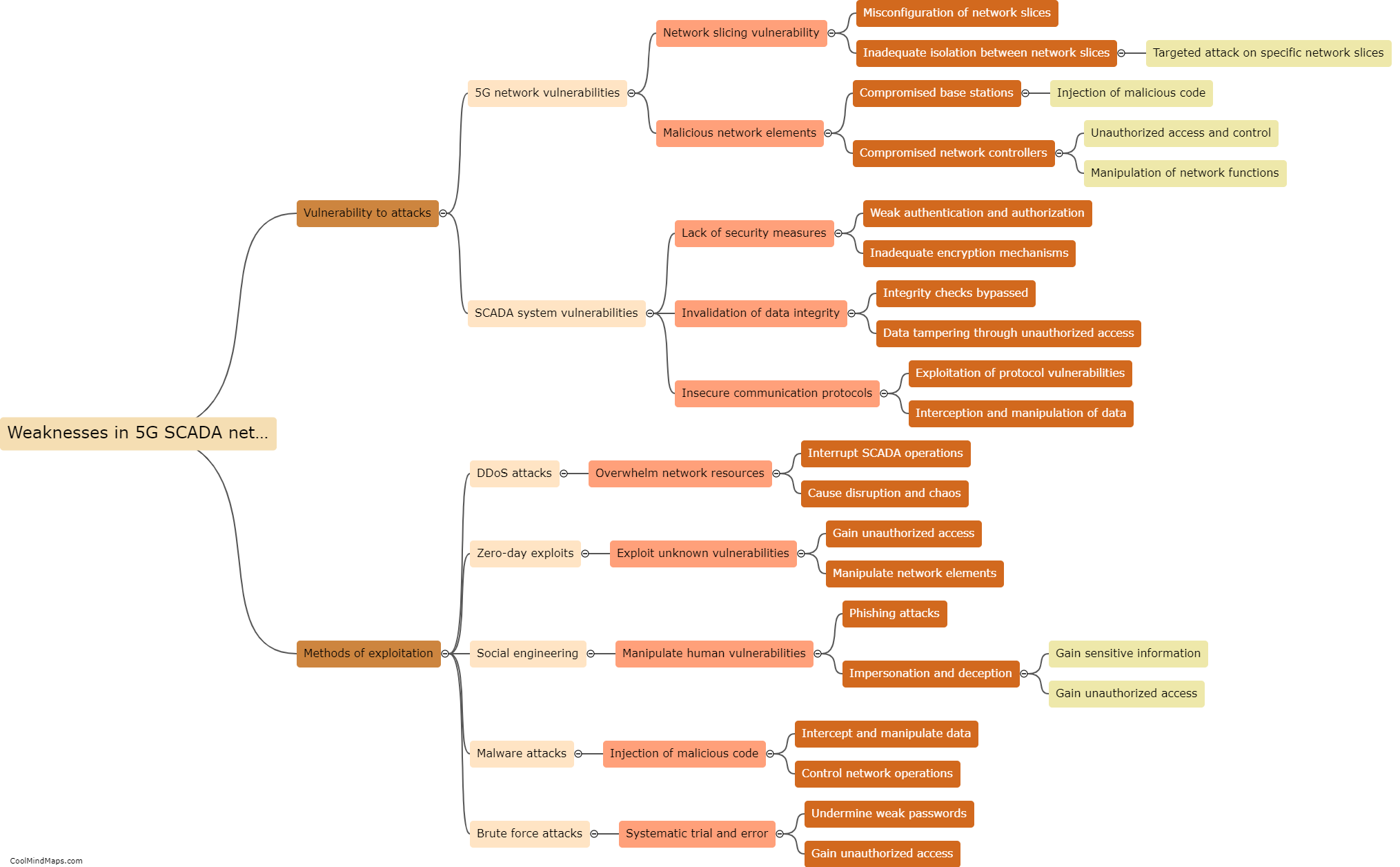
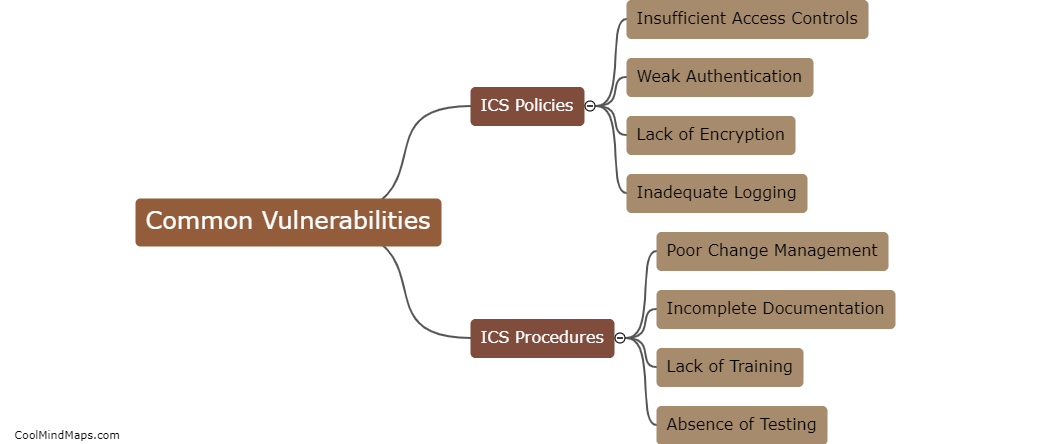
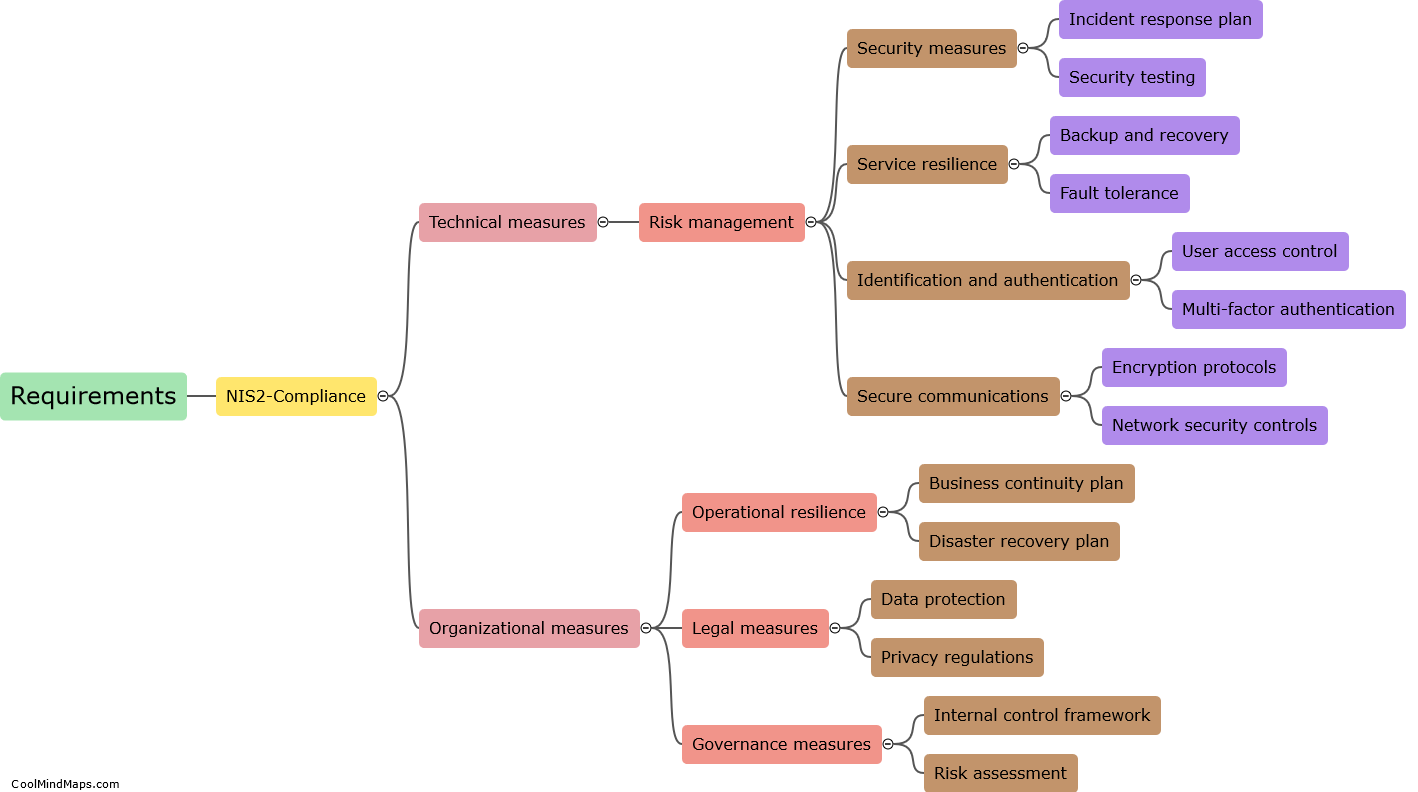
SCADA (Supervisory Control and Data Acquisition) systems play a crucial role in various industrial sectors, such as power generation, water treatment, and manufacturing, by monitoring and controlling critical infrastructure. As we move towards the era of 5G networks, the integration of SCADA systems with advanced wireless technologies becomes inevitable, offering increased efficiency and real-time data transfer. However, this also brings new security challenges. SCADA systems can be targeted in 5G networks through various means, such as exploiting vulnerabilities in the underlying communication protocols, launching denial-of-service attacks, intercepting or manipulating the wireless signals, or exploiting weaknesses in the hardware or software components of the system. Therefore, robust security measures, including encryption, authentication, and intrusion detection systems, must be employed to safeguard these critical systems against potential threats in 5G networks.

This mind map was published on 28 January 2024 and has been viewed 100 times.