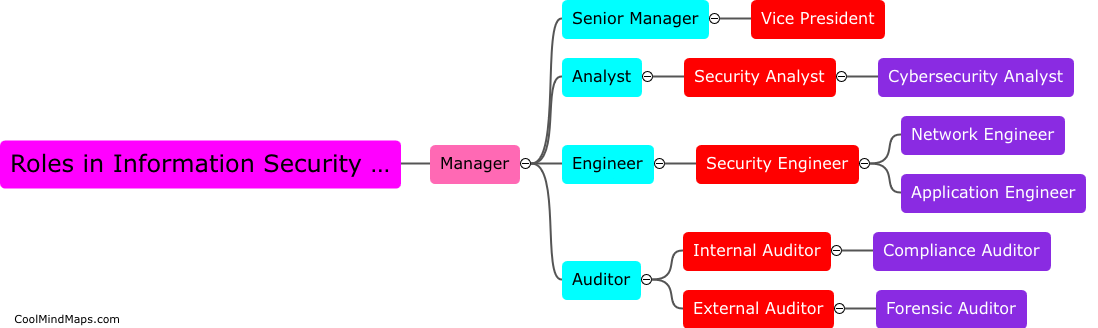
What are the components of an information security program?
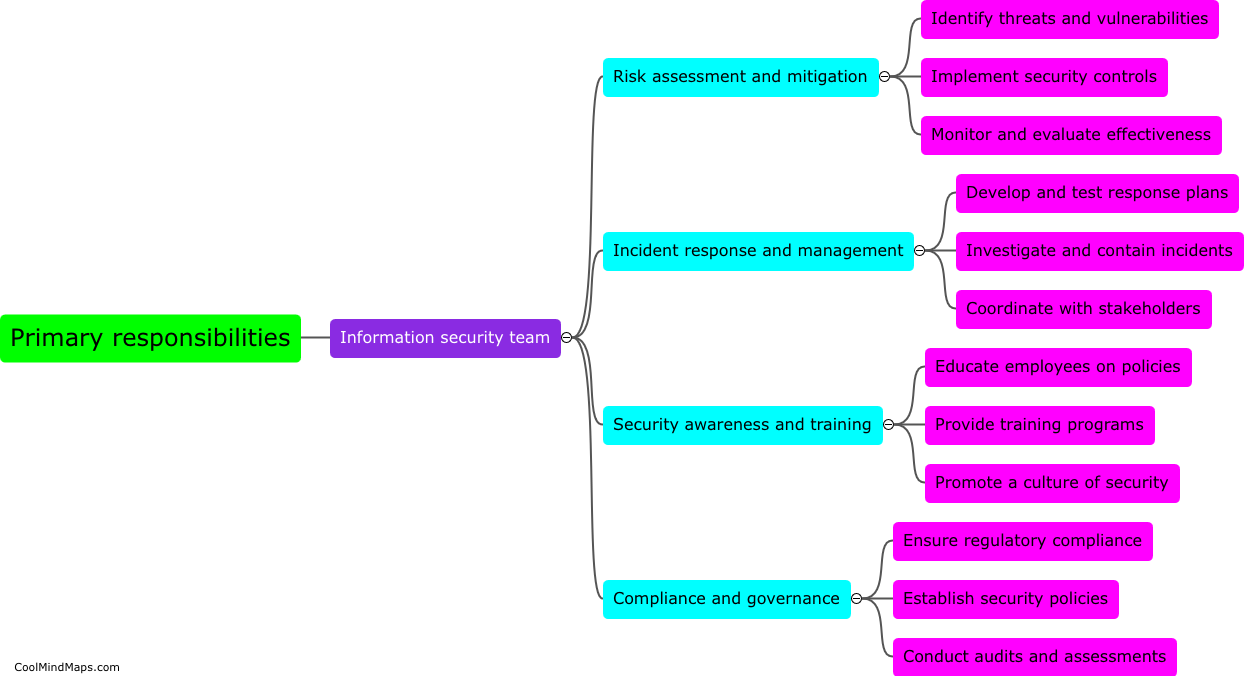
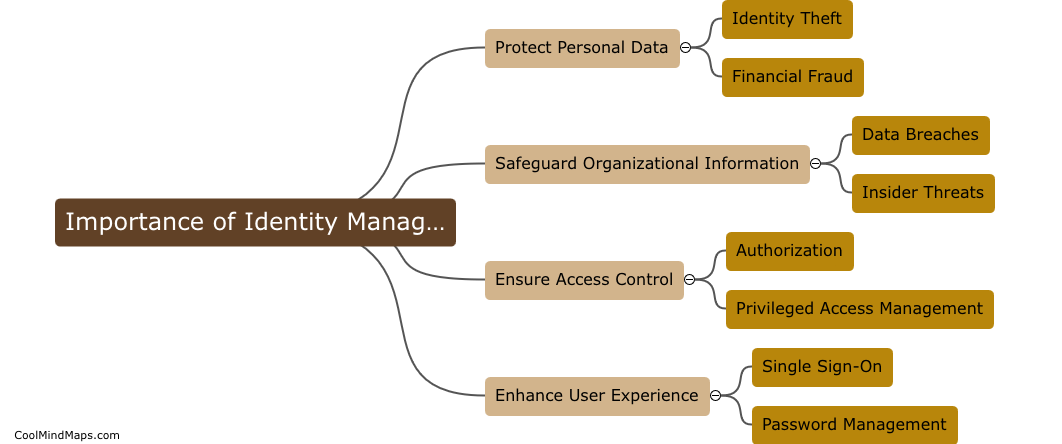
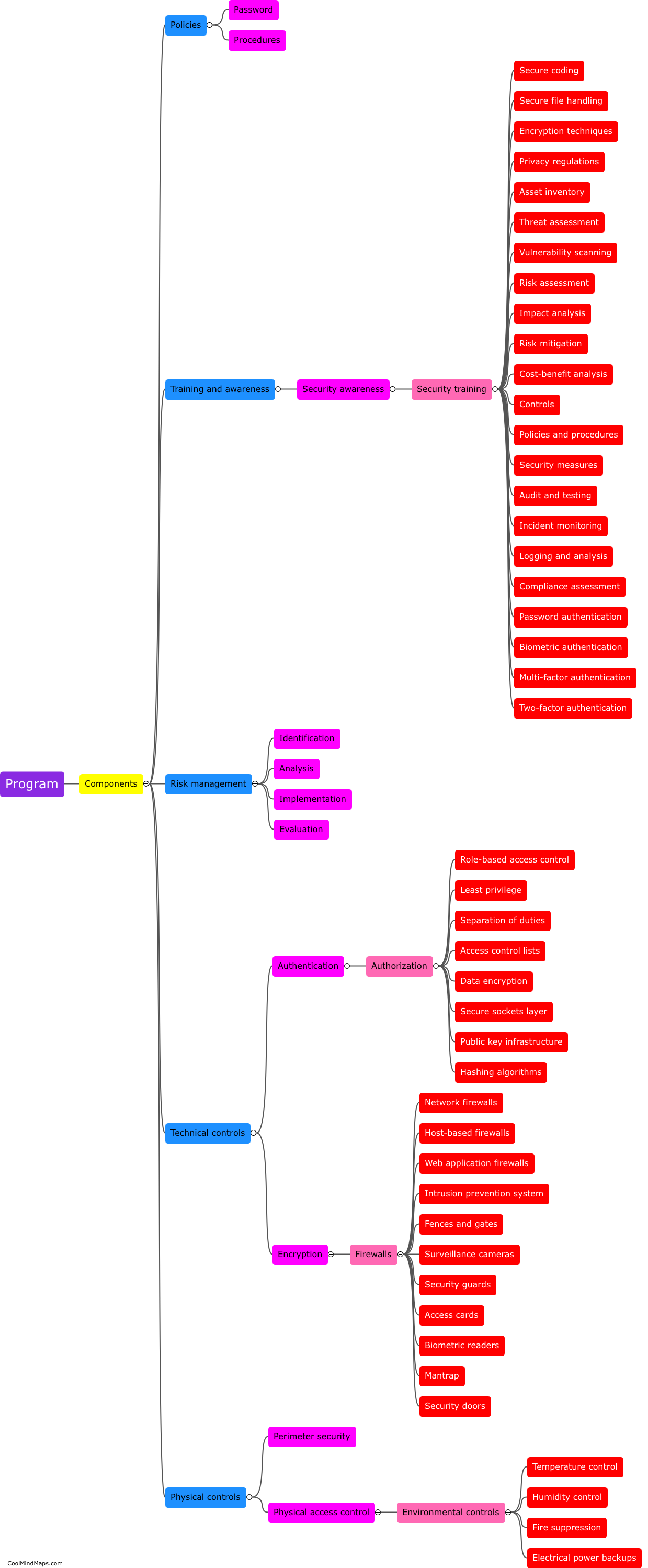
An information security program comprises various components that work together to safeguard sensitive information and protect an organization from potential threats. These components typically include policies and procedures, risk management, security awareness and training, access controls, incident response, and ongoing monitoring and auditing. Policies and procedures establish guidelines for employees to follow, outlining how information should be handled and protected. Risk management involves identifying and assessing potential risks to information and implementing measures to mitigate these risks. Security awareness and training programs educate employees on cybersecurity best practices and potential threats. Access controls determine who can access specific information and systems and establish measures such as passwords and user authentication. Incident response plans outline steps to be taken in the event of a security breach or incident. Ongoing monitoring and auditing involve regular assessments and evaluations of the information security program to ensure its effectiveness and identify areas for improvement. By implementing these components, organizations can establish a robust information security program that safeguards critical data and maintains the trust of customers and stakeholders.
This mind map was published on 5 February 2024 and has been viewed 104 times.