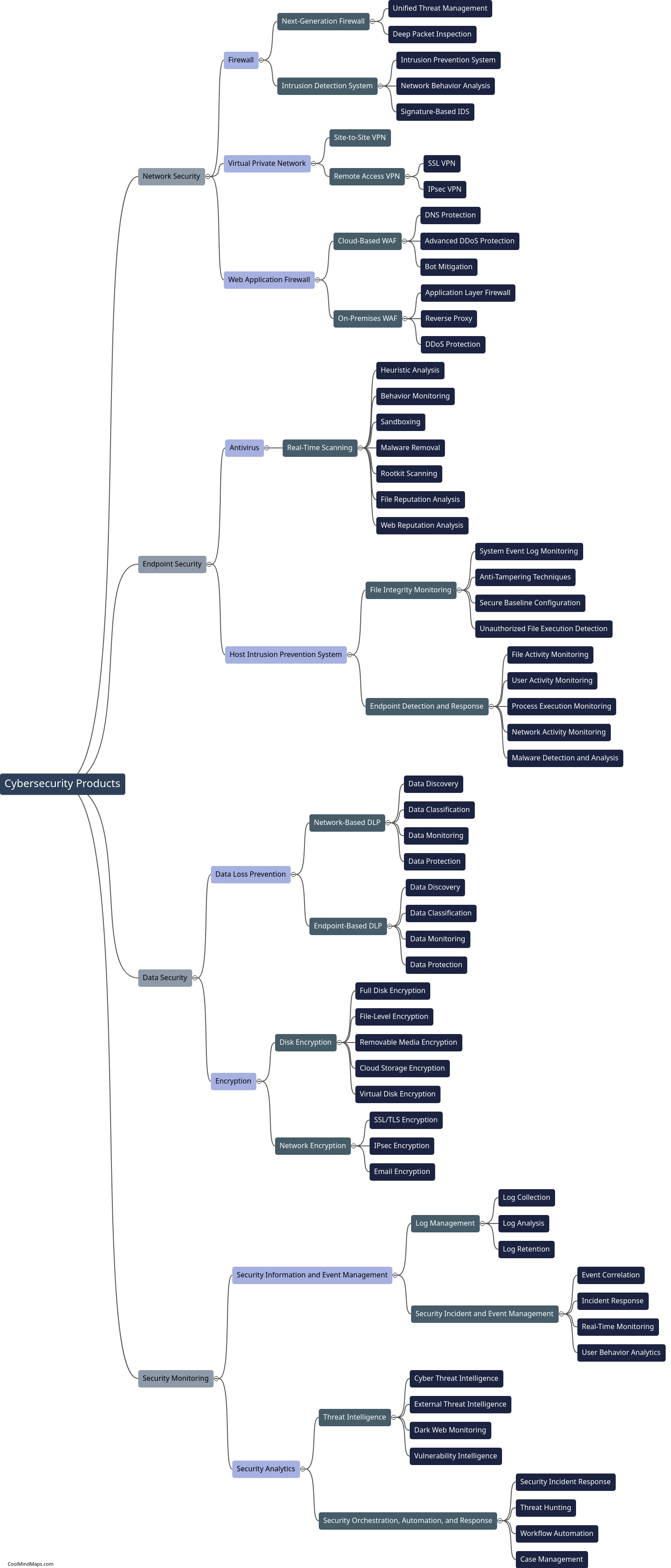
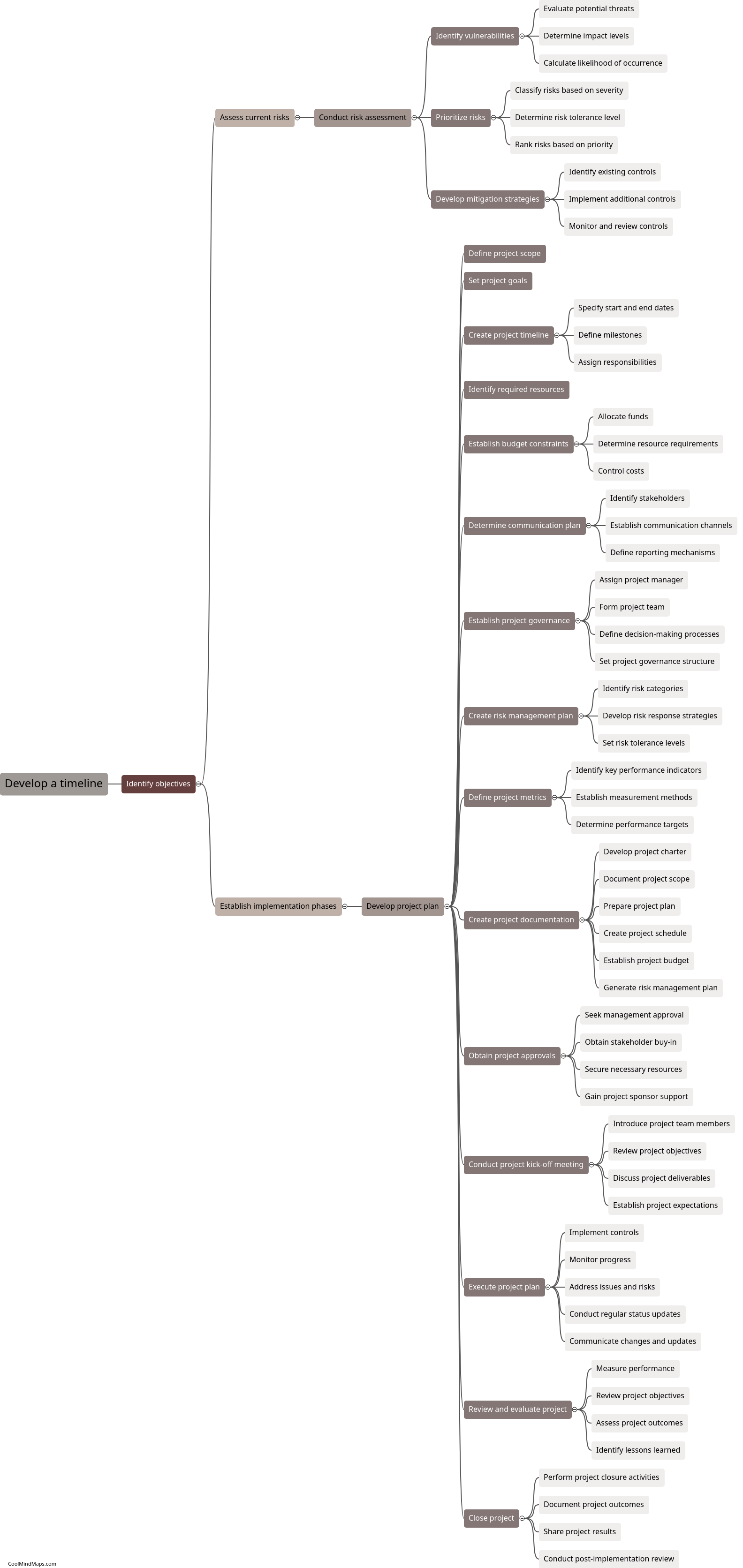
How do you develop a timeline for implementing cybersecurity measures?
Developing a timeline for implementing cybersecurity measures requires careful planning and consideration of various factors. Firstly, a thorough assessment of the current state of cybersecurity within an organization is essential. This will involve identifying existing vulnerabilities, evaluating potential threats, and understanding the impact of a cybersecurity breach. Once these risks are identified, prioritize them based on their potential impact and likelihood. Next, set specific goals and objectives for each cybersecurity measure, such as implementing firewalls, setting up regular security training, or conducting penetration testing. Estimate the time and resources required for each task and create a detailed timeline that outlines the implementation schedule. Regularly review and update the timeline to adapt to changing threats and prioritize emerging risks. Additionally, involve all key stakeholders, including IT teams, management, and employees, to ensure everyone is aware of their responsibilities and the timeline for cybersecurity implementation.
This mind map was published on 23 August 2023 and has been viewed 98 times.