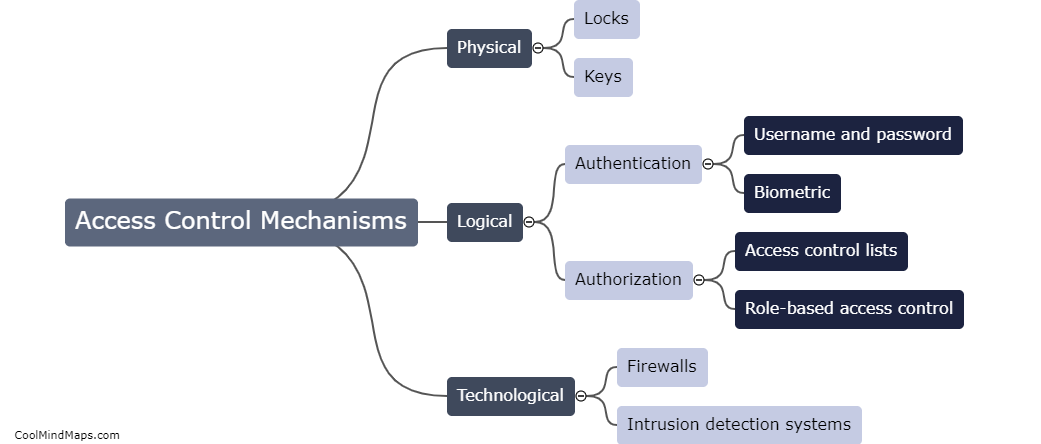
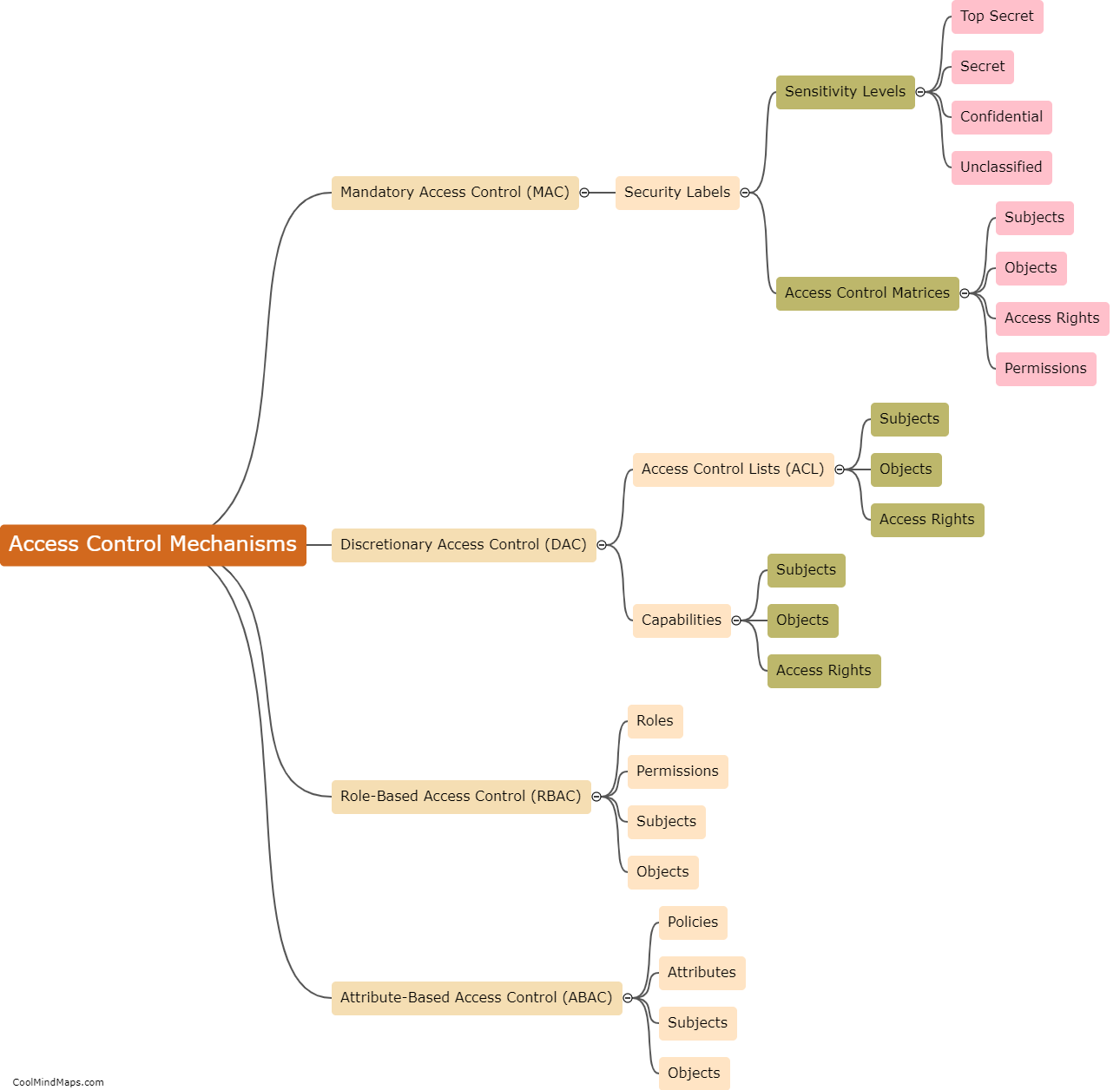
How are access control mechanisms implemented?
Access control mechanisms are implemented through a systematic set of protocols, policies, and technologies to manage user access to resources within a system or organization. Typically, access control begins with the creation of user accounts that define privileges and permissions. These accounts are then authenticated through a combination of passwords, biometrics, or multi-factor authentication. Access control lists (ACL) and role-based access control (RBAC) are commonly employed to assign specific permissions to users or groups, allowing or denying access to certain resources. Furthermore, firewalls, intrusion detection systems, and encryption techniques are used to enforce access control policies. Regular reviews and audits are conducted to ensure the effectiveness and adherence to access control mechanisms.
This mind map was published on 11 September 2023 and has been viewed 139 times.