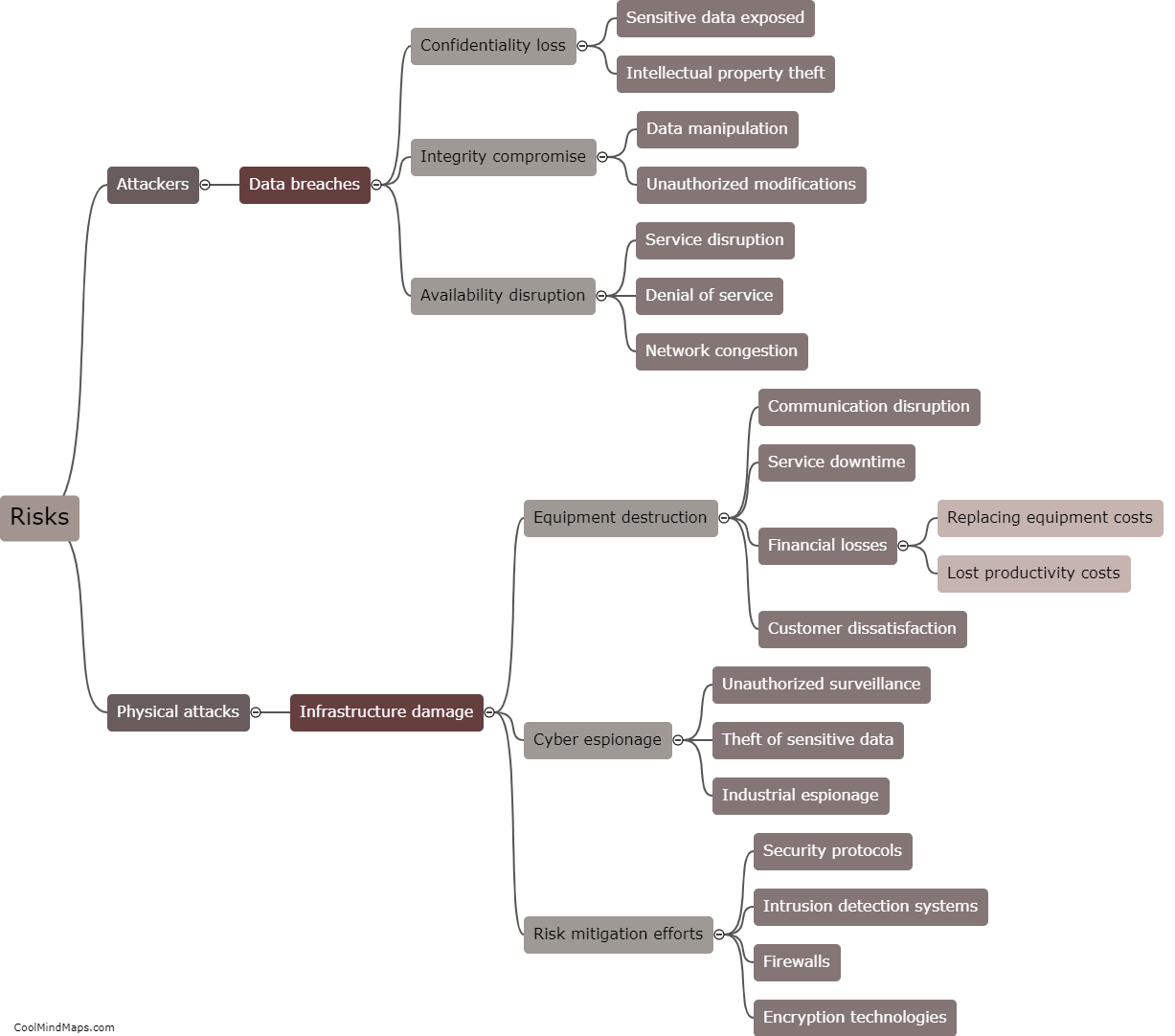
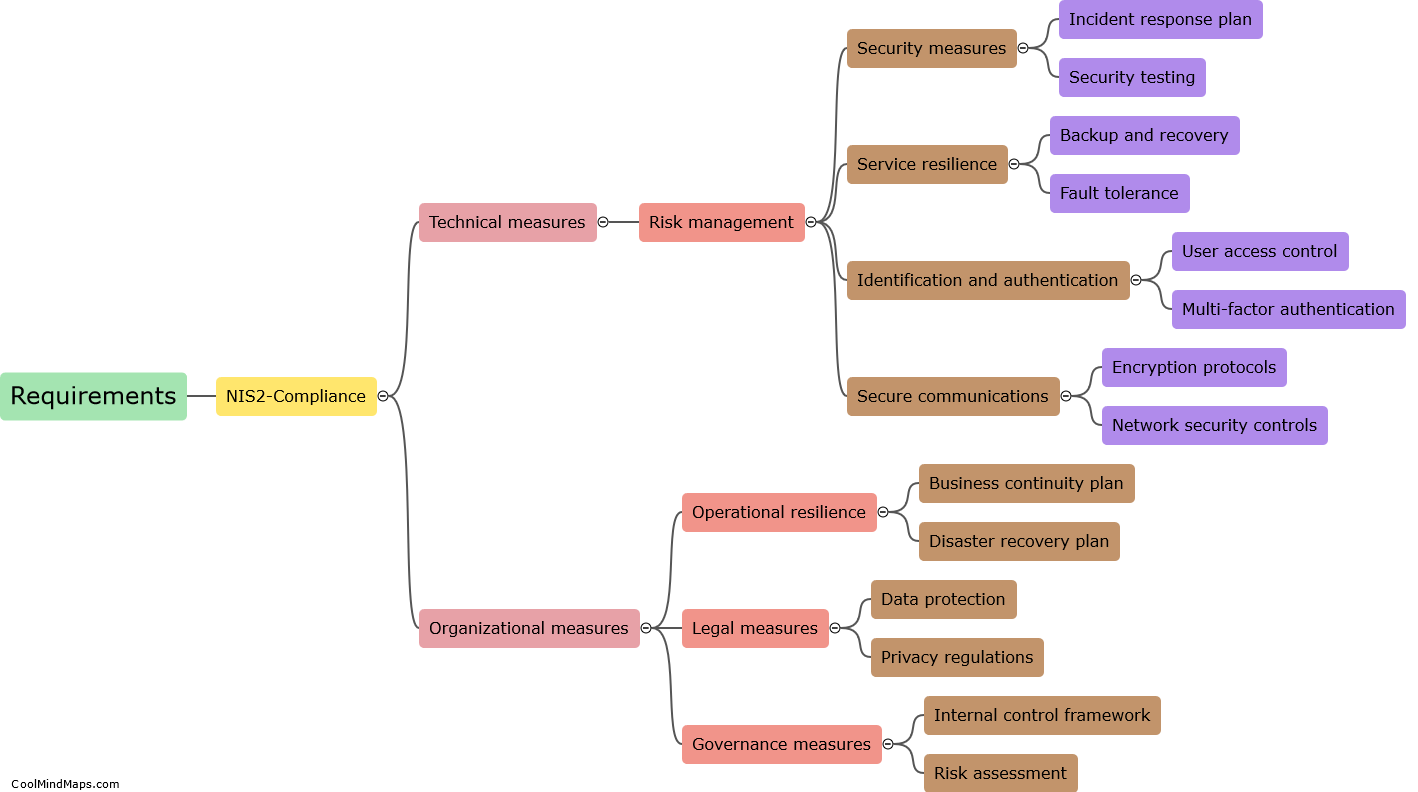
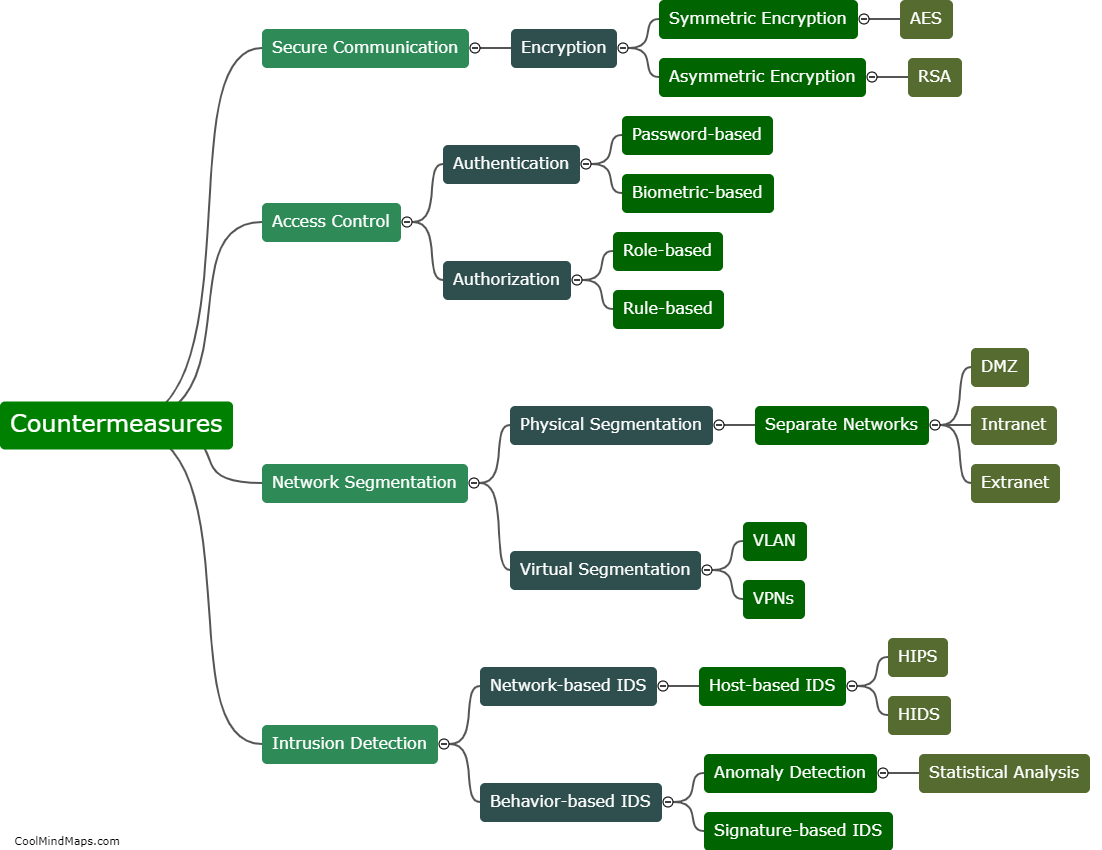
What are the countermeasures to protect 5G ICS core networks?
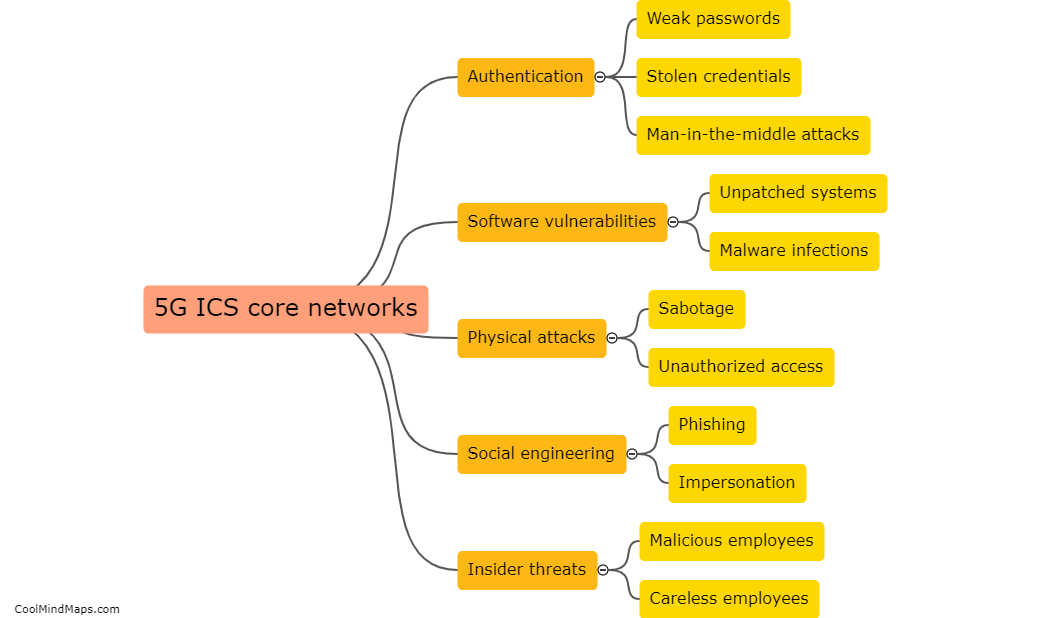
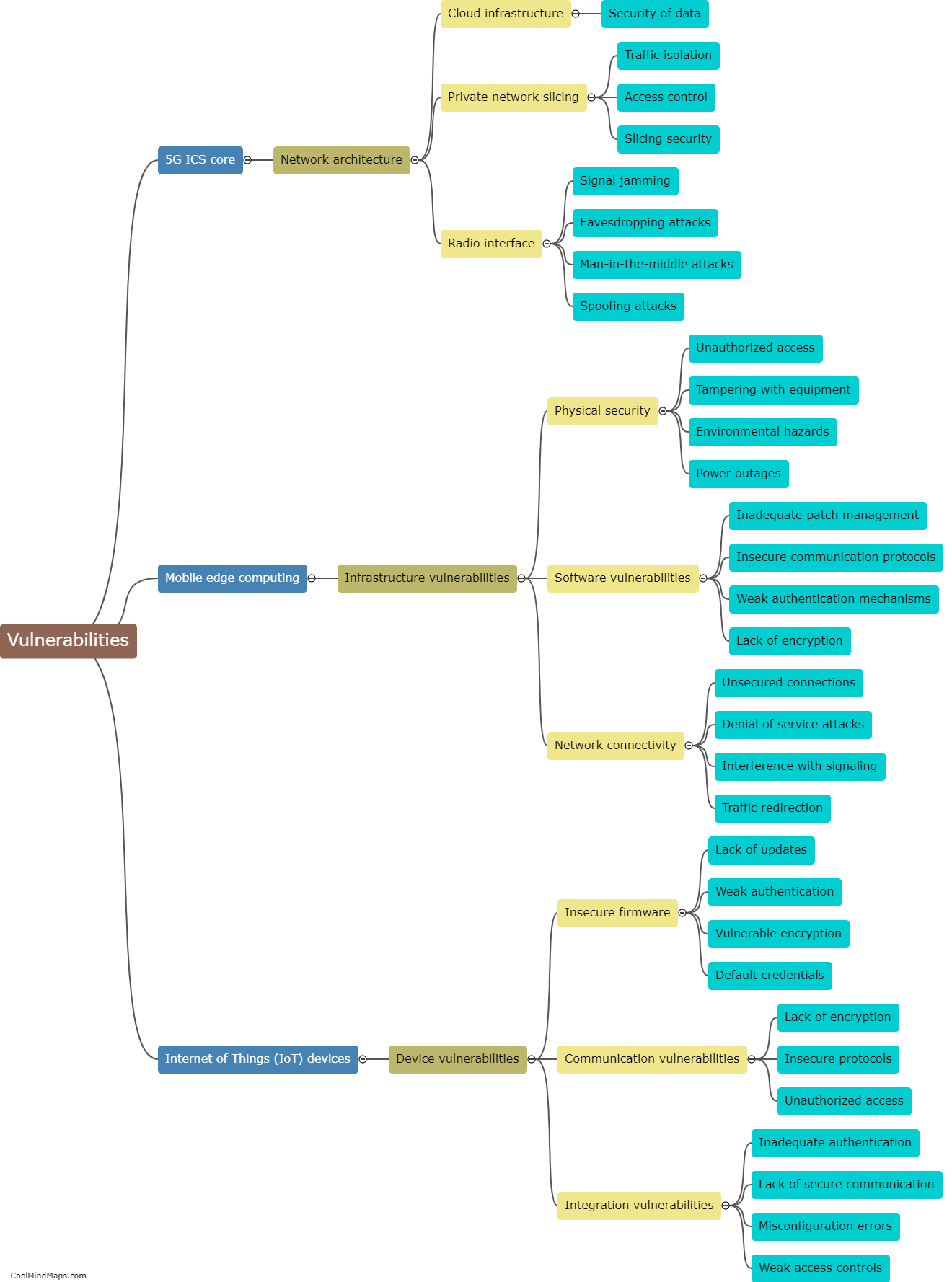
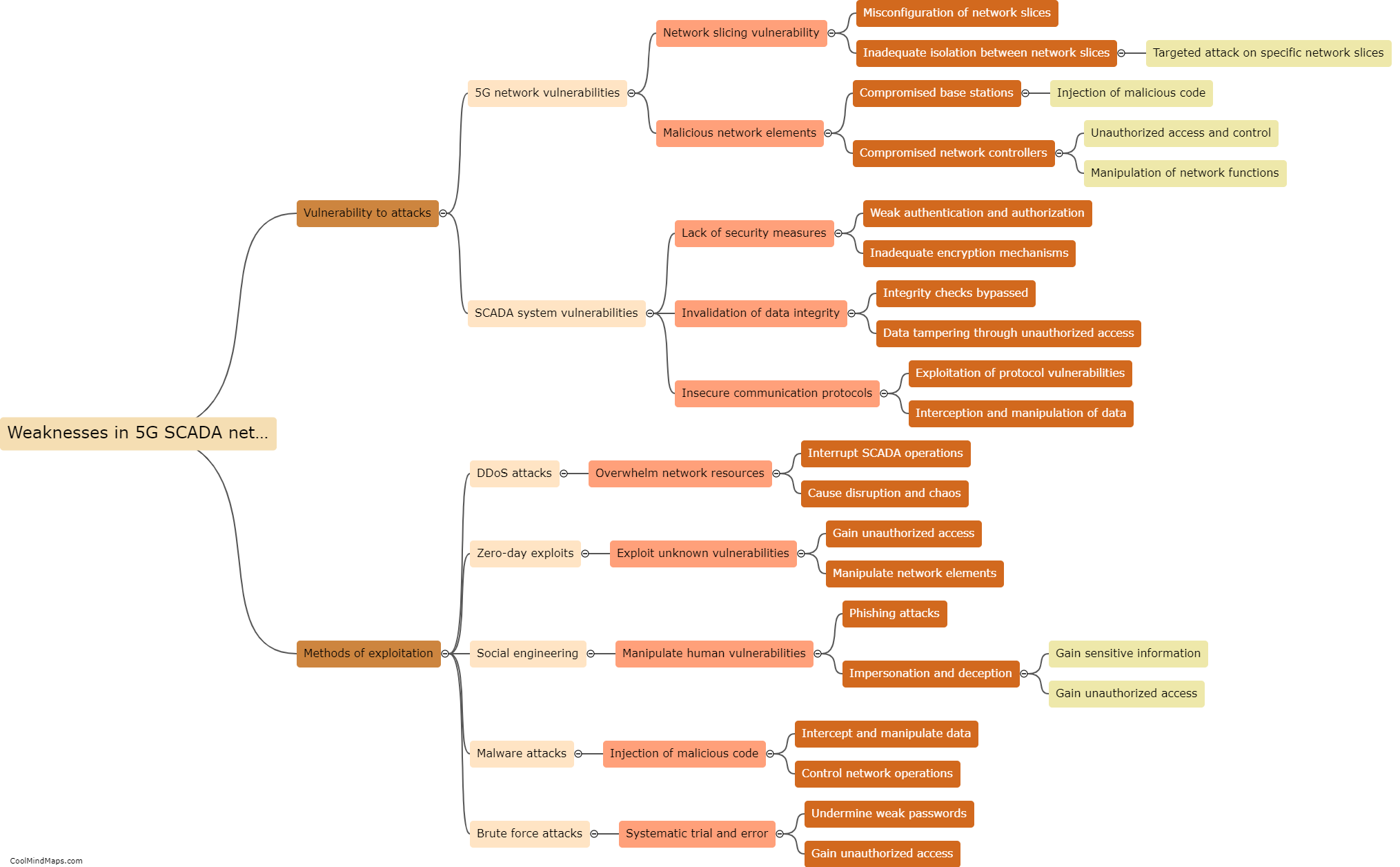
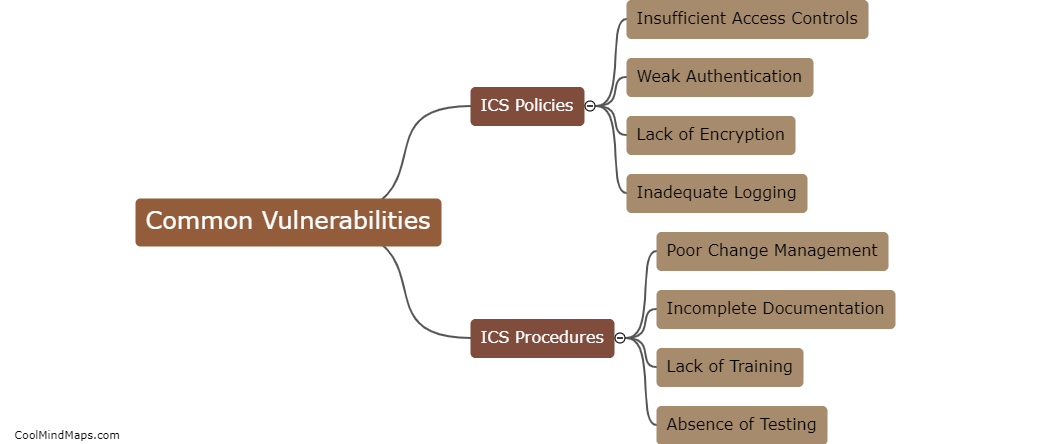
To protect 5G ICS (Industrial Control Systems) core networks, several countermeasures can be implemented. First and foremost, network segmentation is crucial. By dividing the network into separate segments or zones with controlled access, it becomes easier to monitor and manage potential threats. Additionally, implementing robust access controls with strong authentication mechanisms and role-based access privileges ensures that only authorized personnel can access the core network. Employing advanced encryption techniques and secure communication protocols further enhances the security of data transmission within the network. Regular security assessment and vulnerability testing help identify and address any weaknesses, ensuring continuous protection. Intrusion detection and prevention systems can also be deployed to actively monitor and prevent unauthorized access or malicious activities. Finally, staff training and awareness programs play a significant role, as educated personnel can identify and respond to potential threats in a timely manner, strengthening the overall security posture of the 5G ICS core networks.
This mind map was published on 27 January 2024 and has been viewed 115 times.