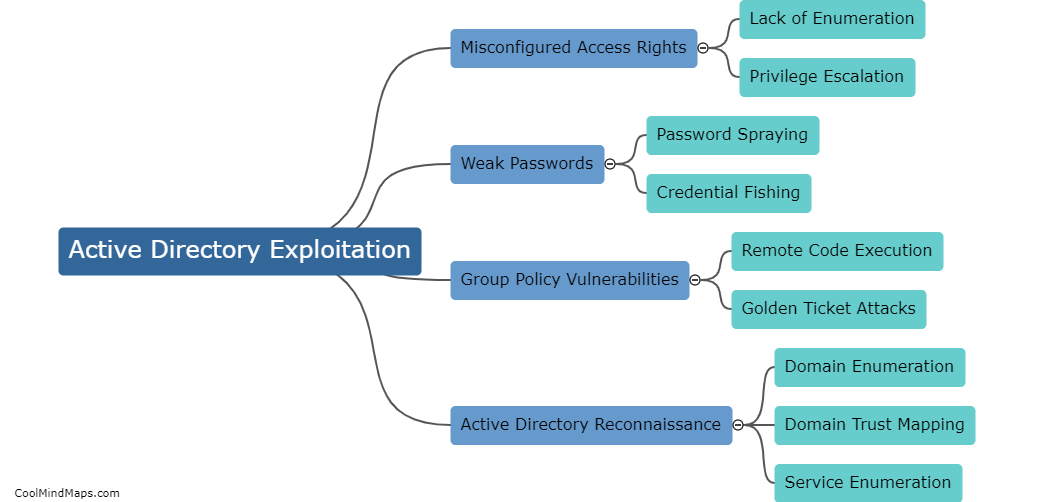
How can an attacker exploit Active Directory?
An attacker can exploit Active Directory to gain unauthorized access to sensitive data and systems by compromising authentication and authorization processes. They can initiate a brute force attack on user passwords or use phishing or social engineering tactics to obtain them. If an attacker can access an administrative account, they can create or modify user accounts and permissions to gain elevated privileges. They can also explore the Active Directory structure, locate vulnerable systems, and exploit security weaknesses in domain controllers, group policies, or trust relationships. Once they gain access, an attacker can easily move laterally across the network, potentially wreaking havoc on an organization's entire IT infrastructure.
This mind map was published on 23 June 2023 and has been viewed 105 times.