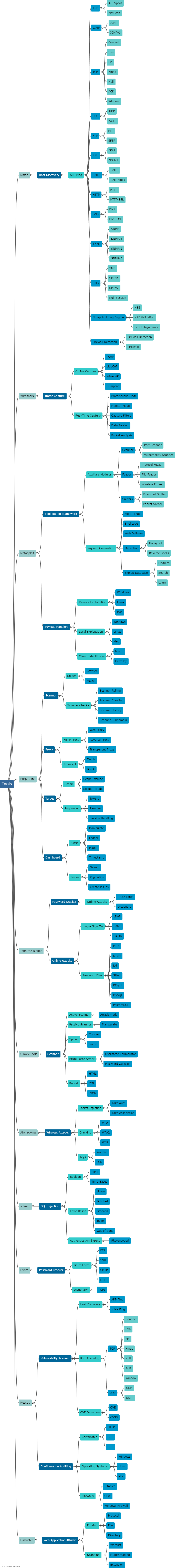
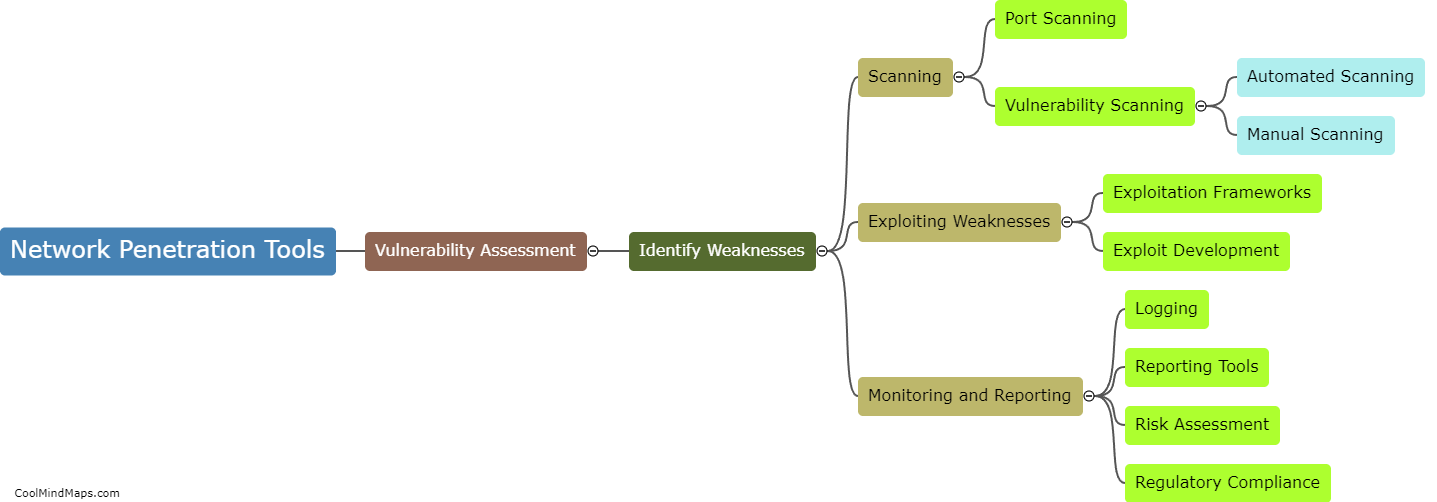
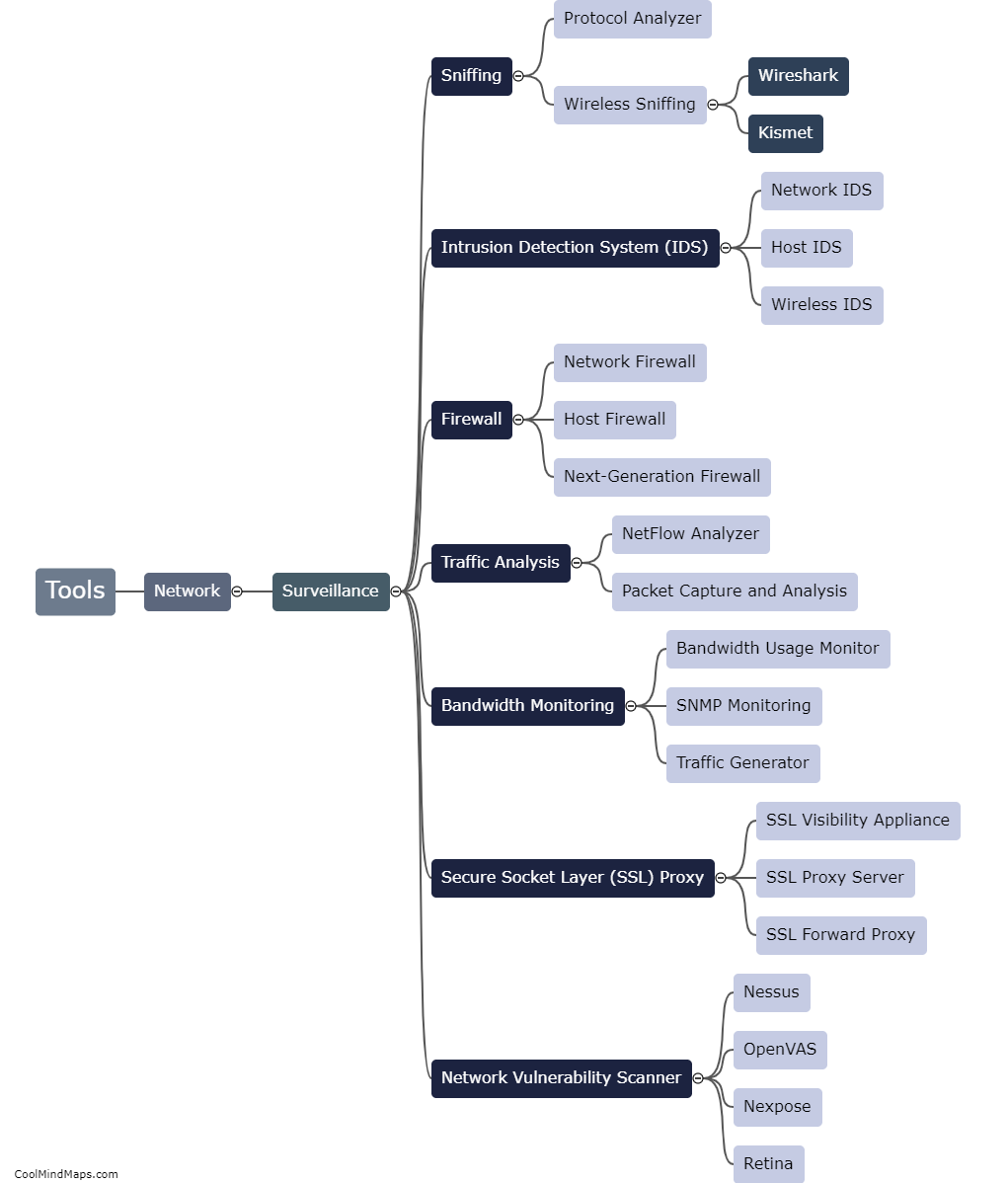
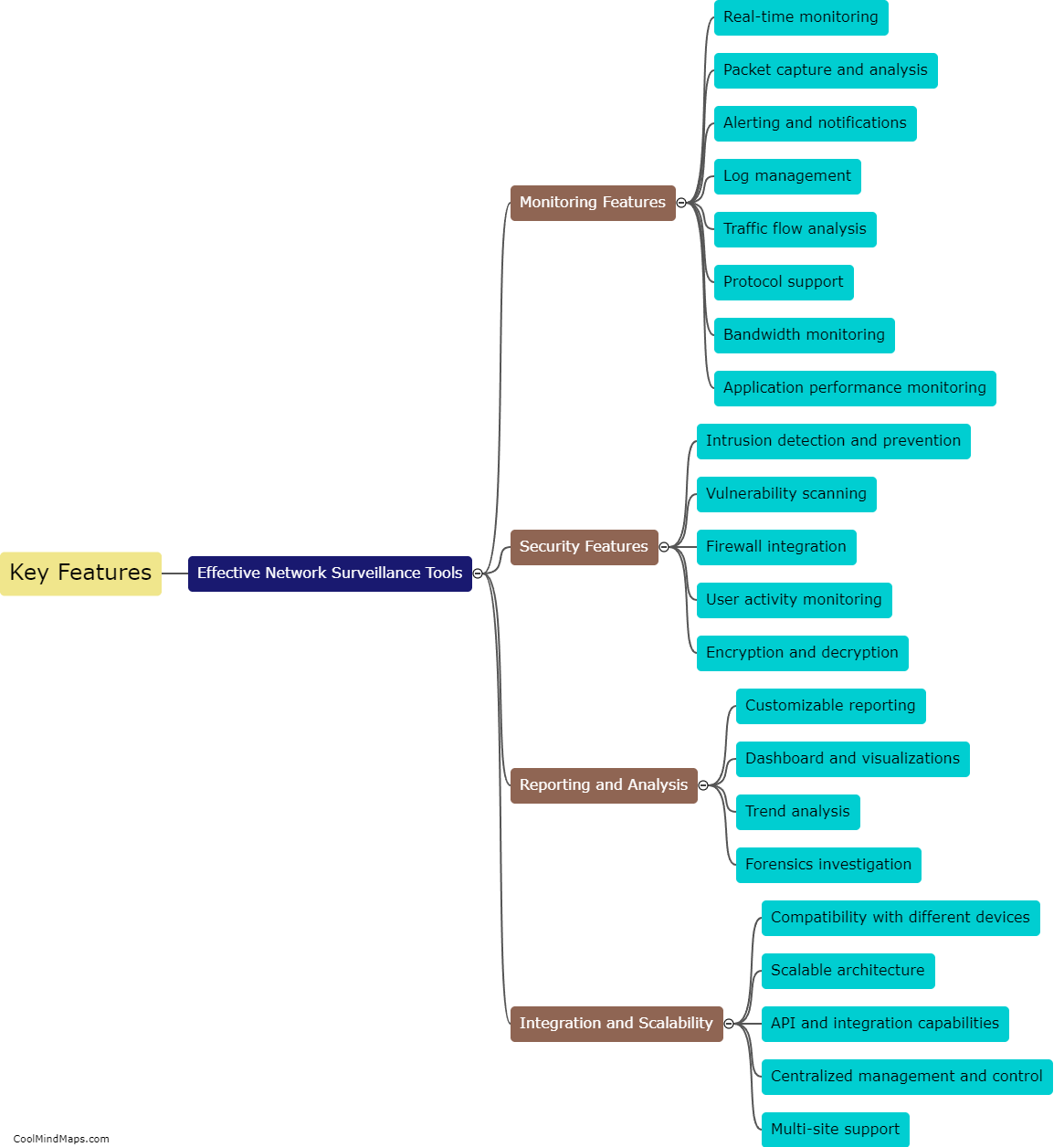
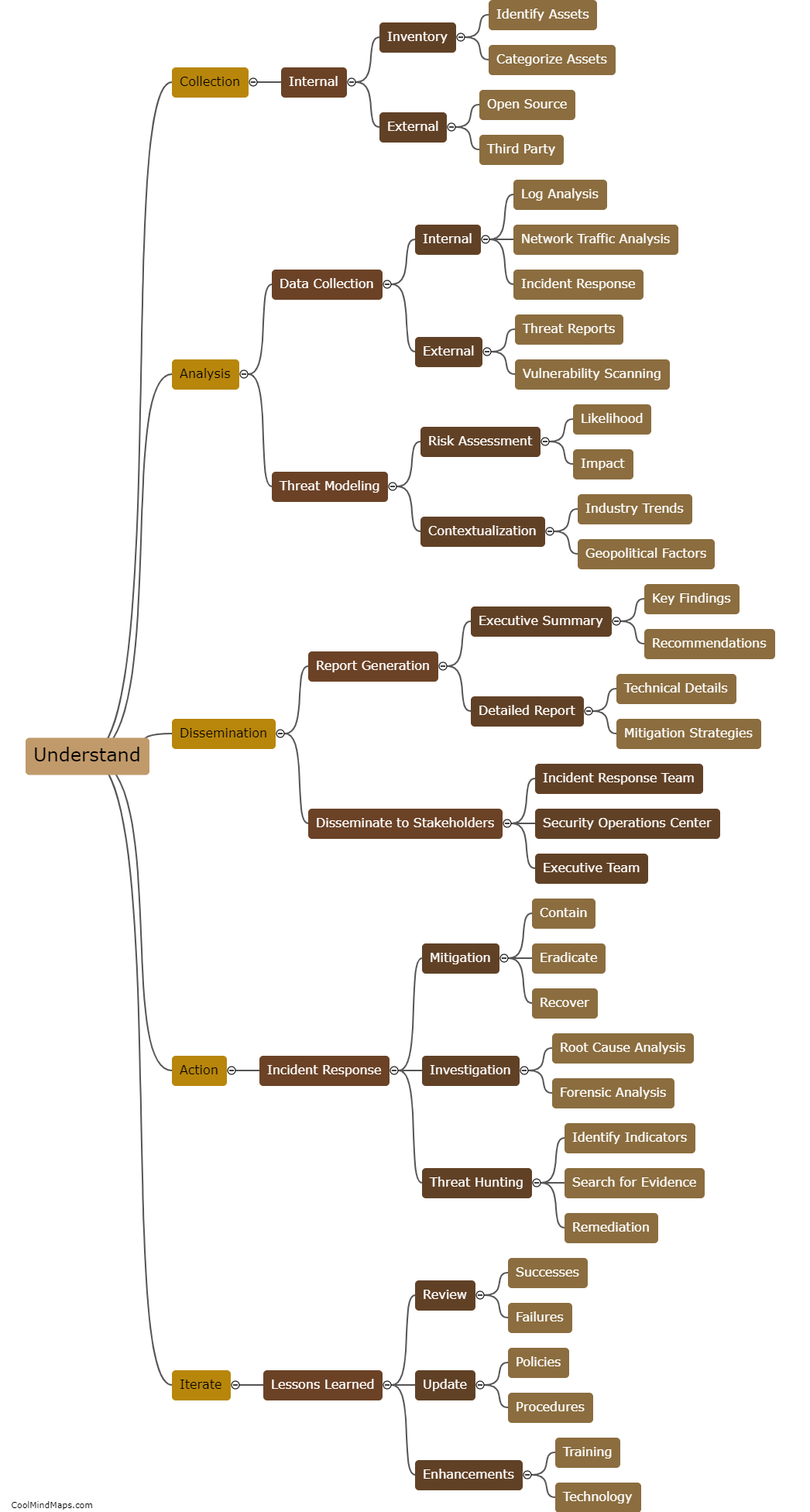
What are the steps in the threat intelligence lifecycle?
The threat intelligence lifecycle consists of several crucial steps that organizations need to follow in order to effectively manage and mitigate potential cybersecurity threats. The first step is data collection, wherein information is gathered from various sources such as network logs, sensors, and external feeds. Next is the processing and analysis phase, which involves organizing and making sense of the collected data, identifying potential threats and their characteristics. Once threats are identified, the next step is to prioritize them based on their severity and potential impact. After prioritization, the information is disseminated to relevant stakeholders for action and response. The final step in the lifecycle is feedback and improvement, where organizations evaluate their response strategies, update their defenses, and continuously improve their threat intelligence programs to stay ahead of evolving threats. Overall, these steps form a continuous and iterative process that helps organizations stay proactive in their cybersecurity efforts.
This mind map was published on 21 September 2023 and has been viewed 97 times.