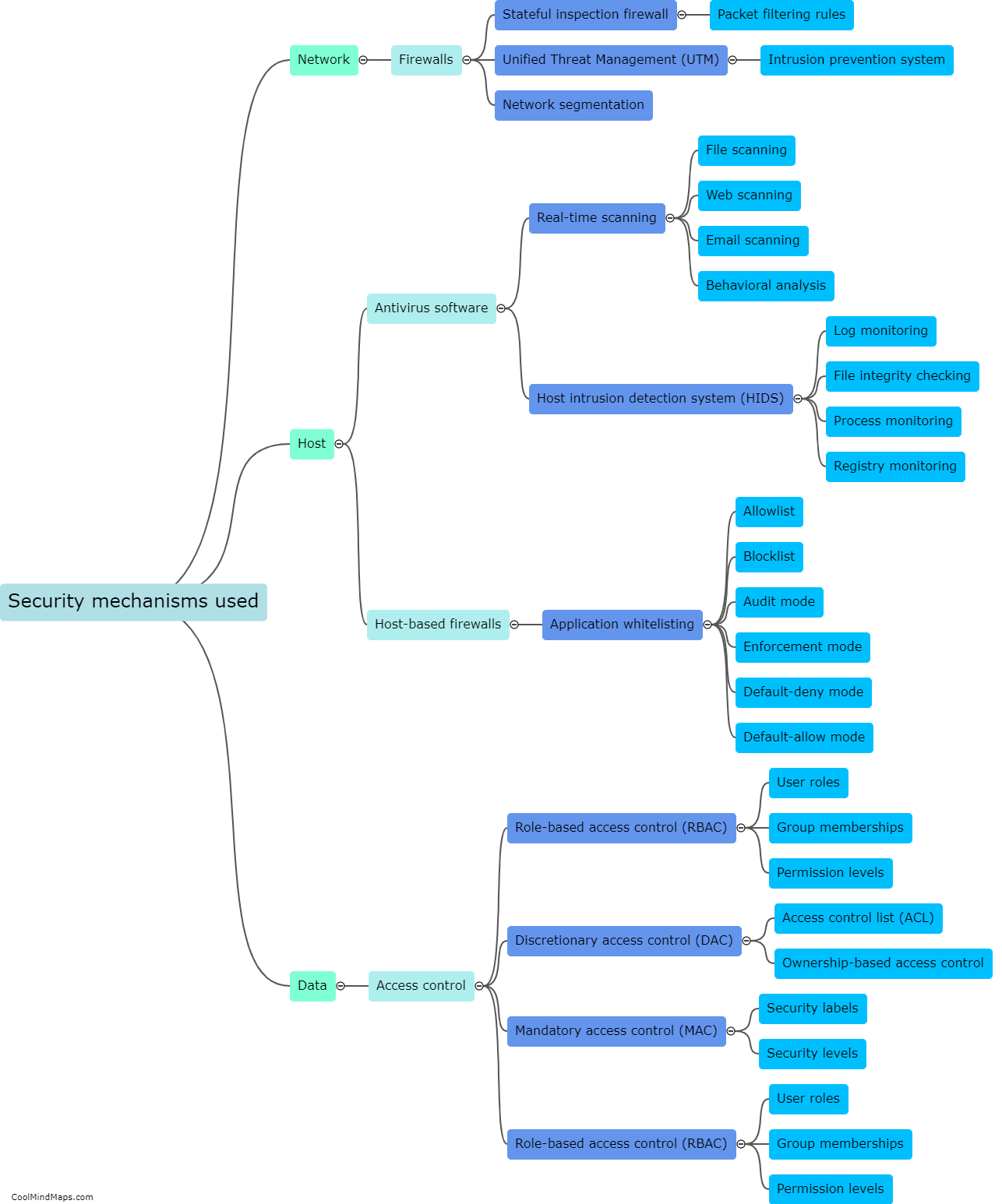
How effective are existing ICS security methods?
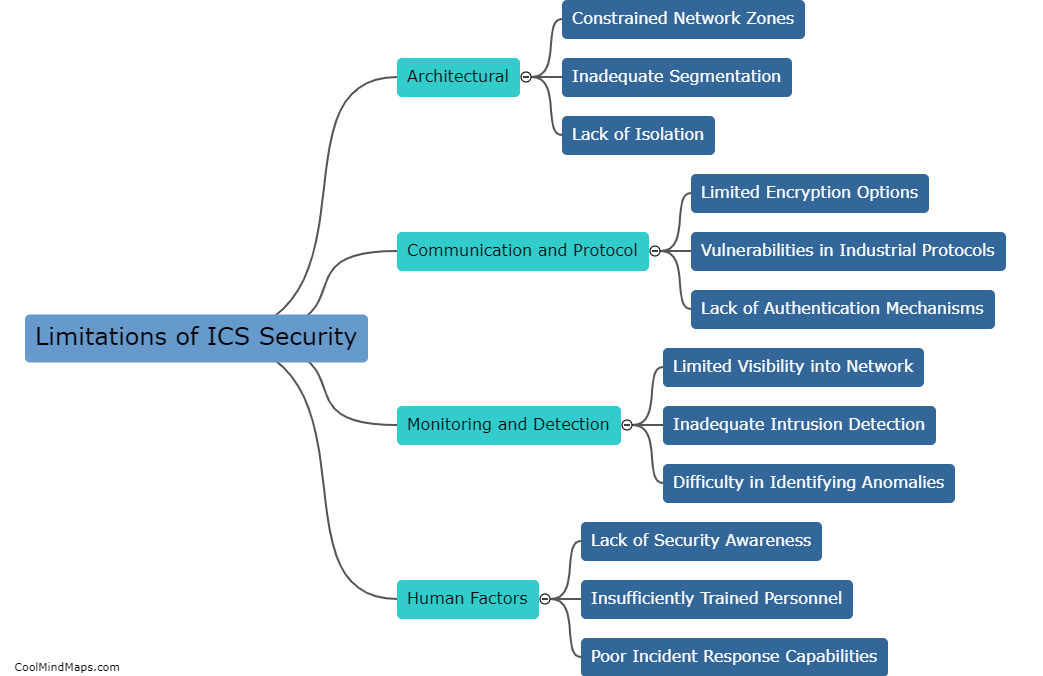
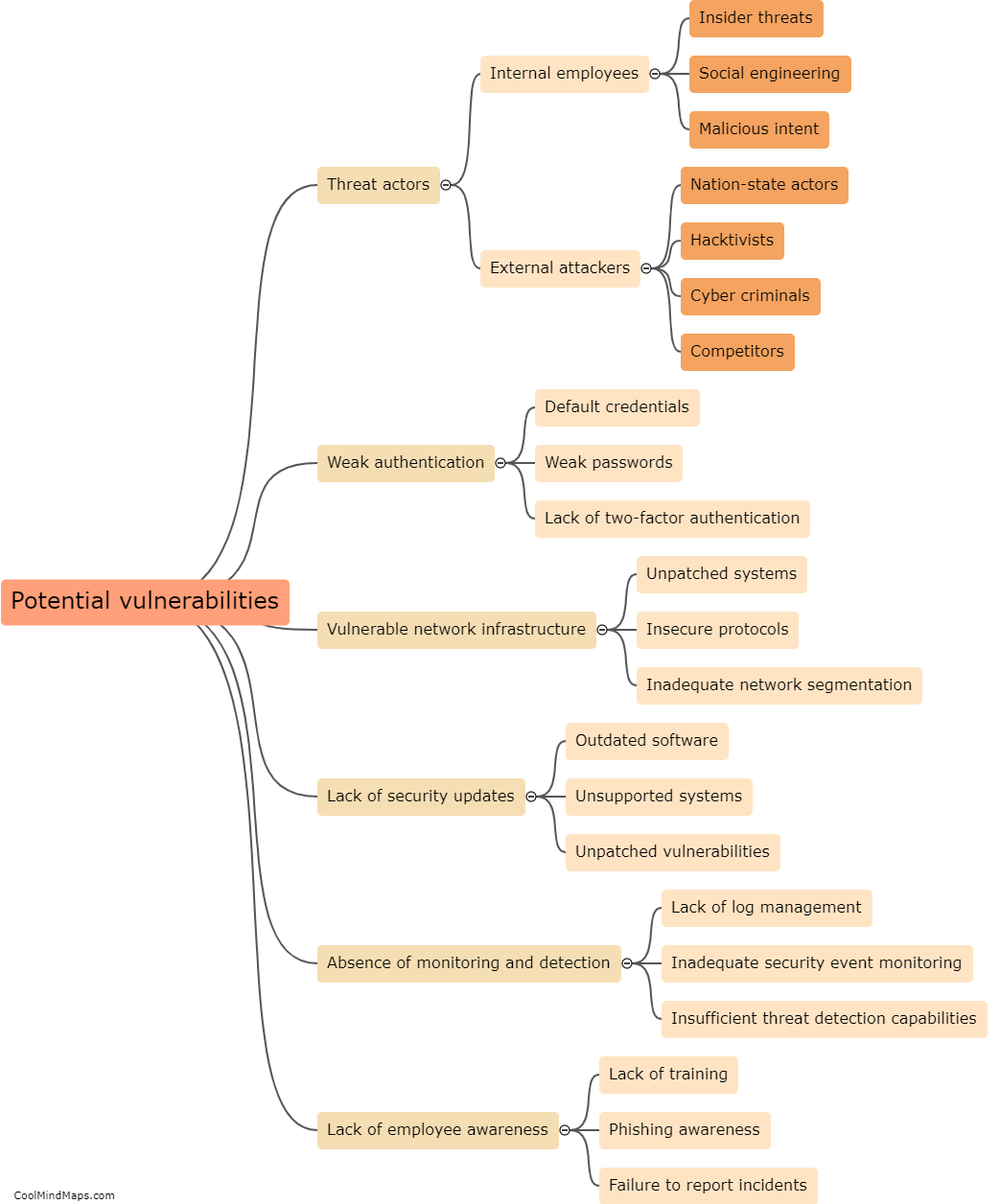
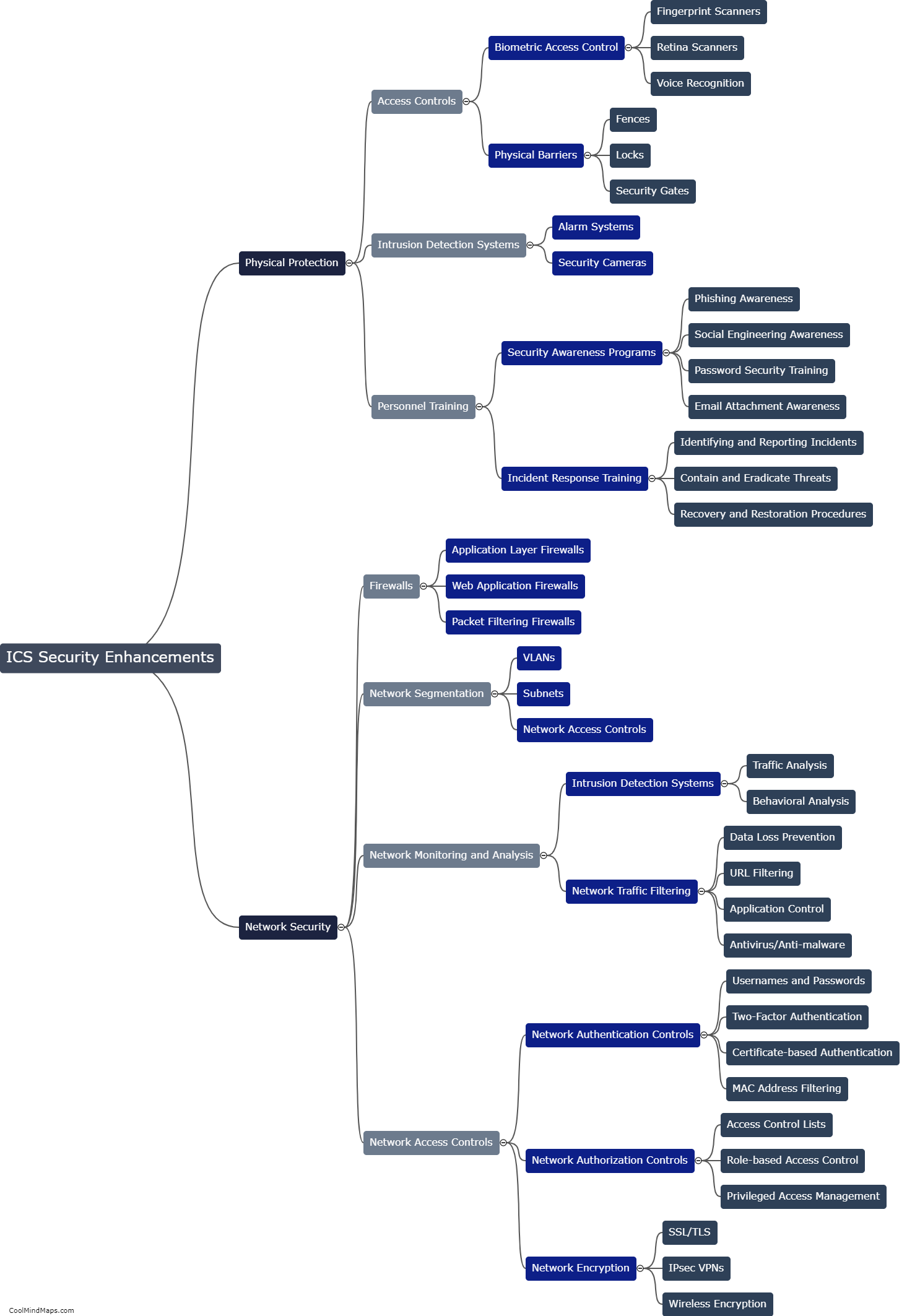
Existing ICS (Industrial Control Systems) security methods have generally proven to be effective, but there are still several challenges that need to be addressed. These methods often focus on implementing strong firewalls, intrusion detection systems, and access controls to safeguard critical infrastructure from cyber threats. While these measures have undoubtedly increased security, the rapidly evolving nature of cyber attacks and the increasing sophistication of hackers pose ongoing challenges. Moreover, the legacy systems in many industrial environments were not originally designed with robust security features, making them vulnerable. Therefore, efforts are being made to enhance ICS security by investing in more advanced technologies, such as intrusion prevention systems, anomaly detection, and secure remote access, to improve overall effectiveness and protect critical infrastructure from emerging threats.

This mind map was published on 28 January 2024 and has been viewed 100 times.