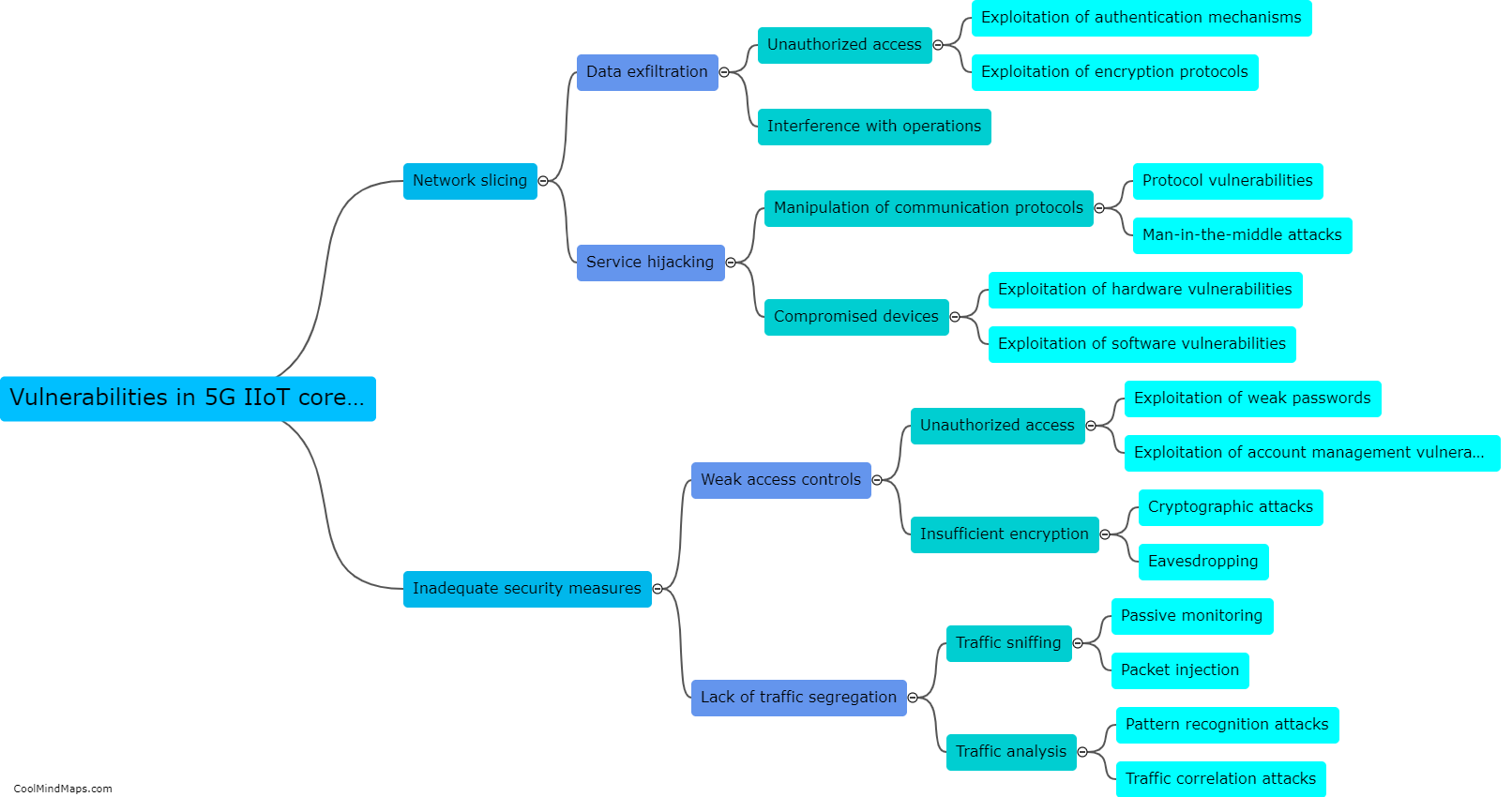
How can vulnerabilities in 5G IIoT core networks be exploited?
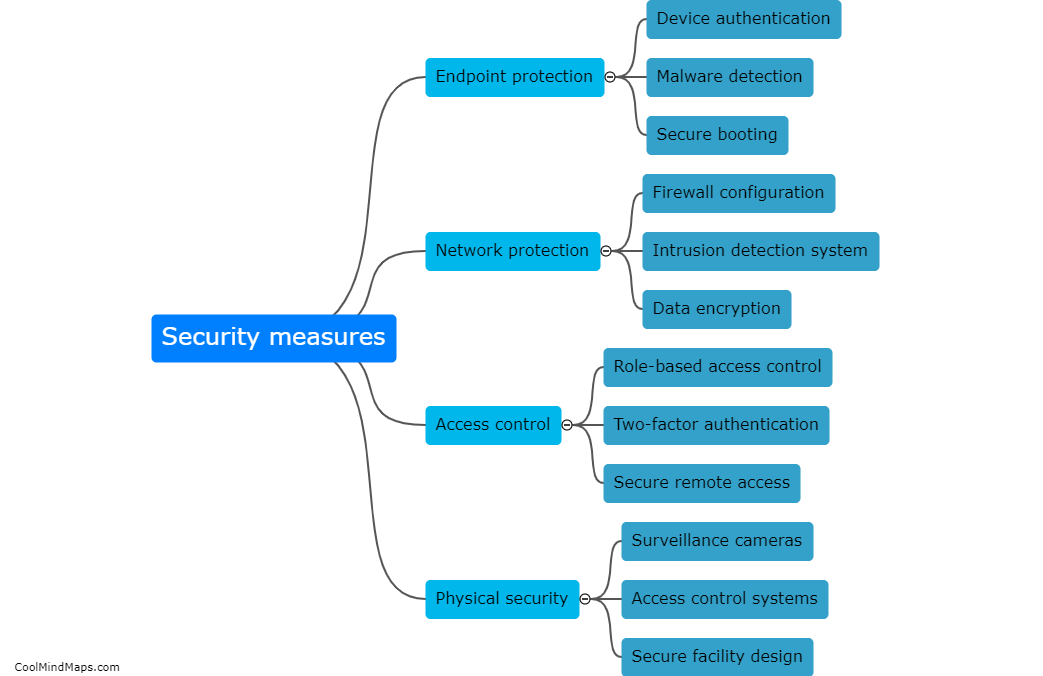
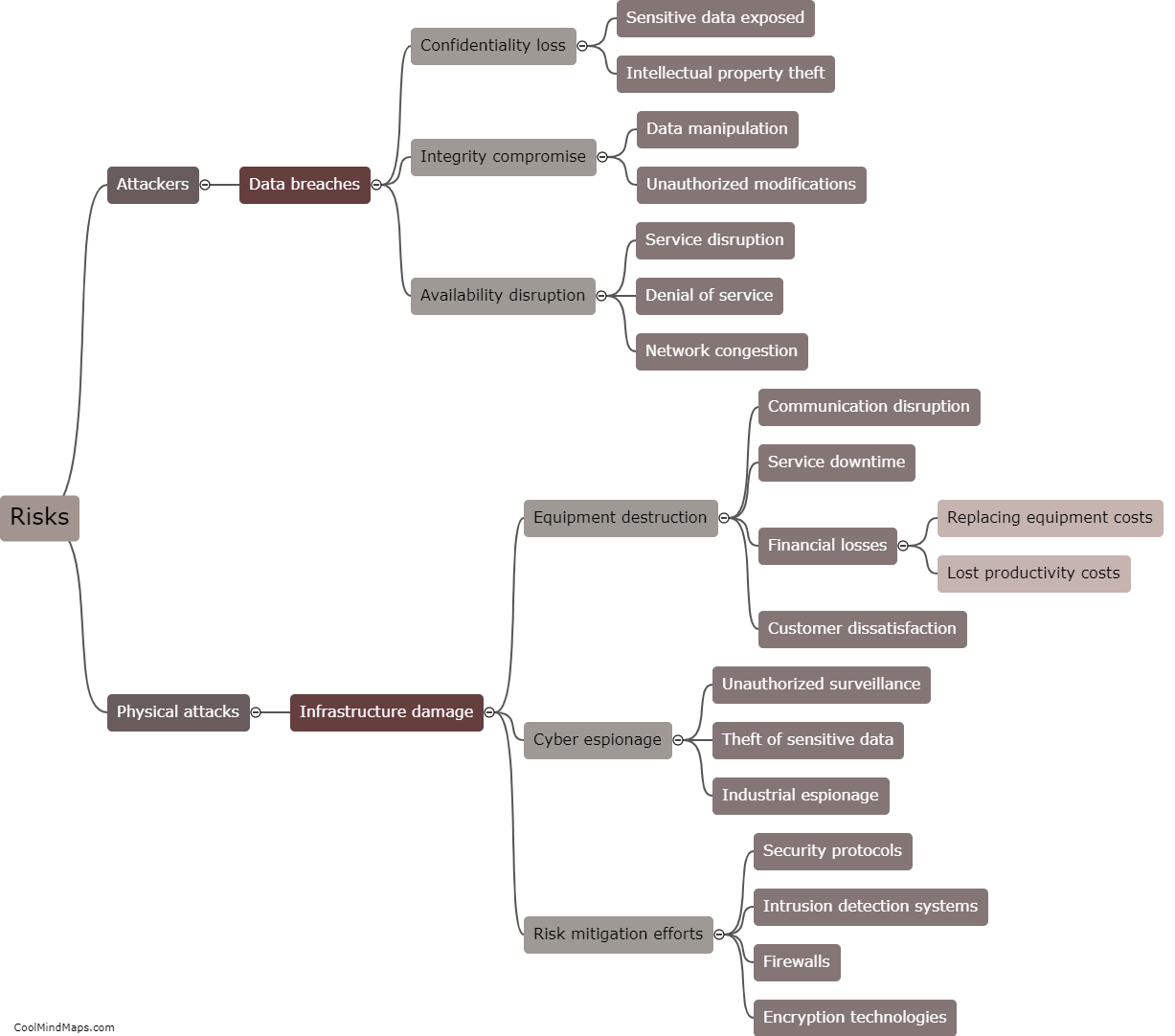
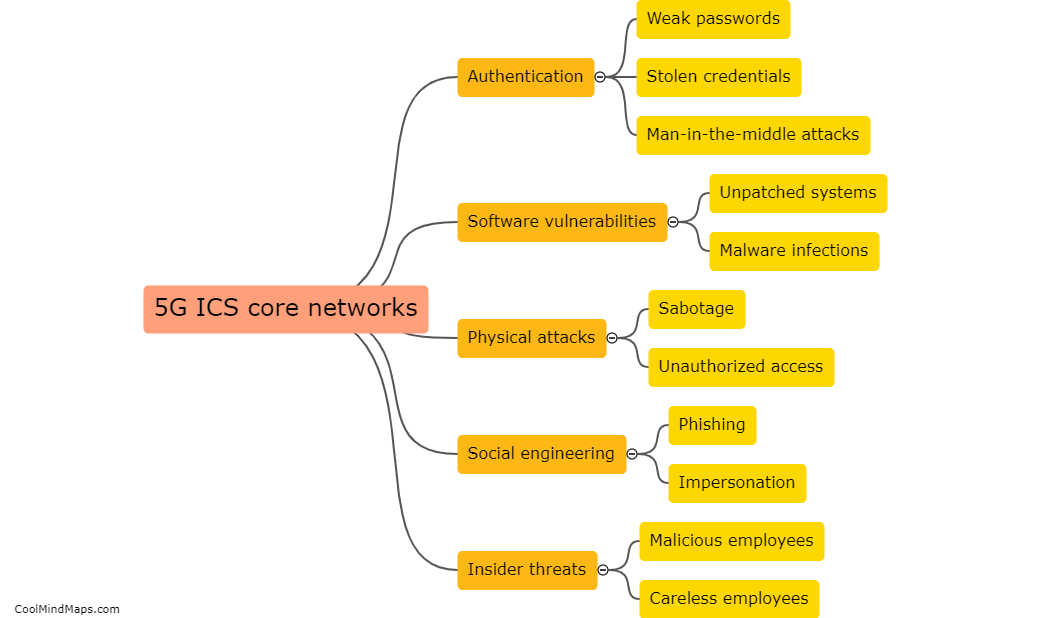
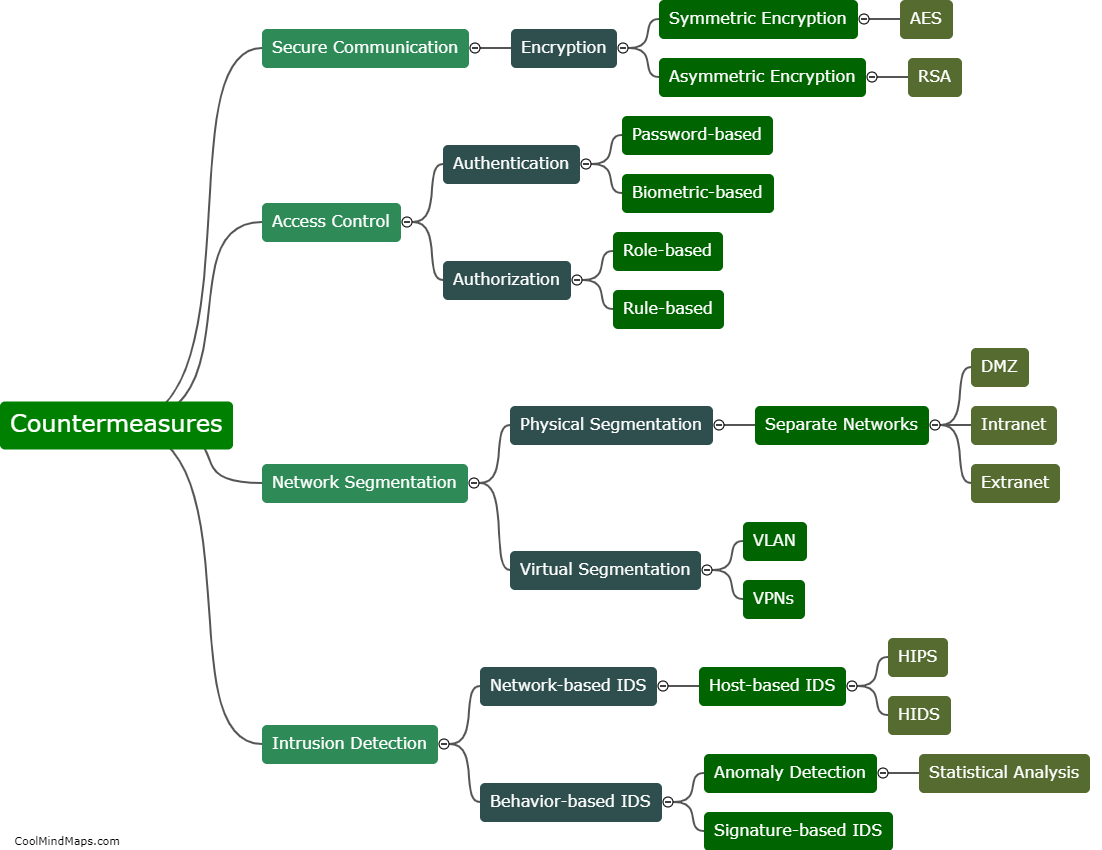
Vulnerabilities in 5G IIoT (Industrial Internet of Things) core networks can be exploited in several ways, posing significant risks to critical infrastructure and industrial operations. Cybercriminals can take advantage of vulnerabilities in network components, software, and protocols to gain unauthorized access to the core network. This can result in malicious activities such as data breaches, disruption of services, unauthorized control over connected devices, and even physical damage to industrial systems. Sophisticated cyber attacks, including malware, ransomware, and distributed denial-of-service (DDoS) attacks, can exploit vulnerabilities in the core network to disrupt operations or steal sensitive information. To mitigate these risks, it is crucial to implement robust network security measures, regular vulnerability assessments, and rigorous access controls to protect the integrity and reliability of 5G IIoT core networks.
This mind map was published on 27 January 2024 and has been viewed 97 times.