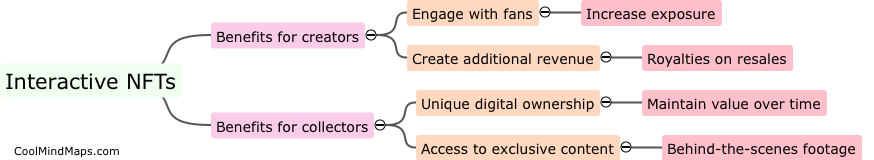
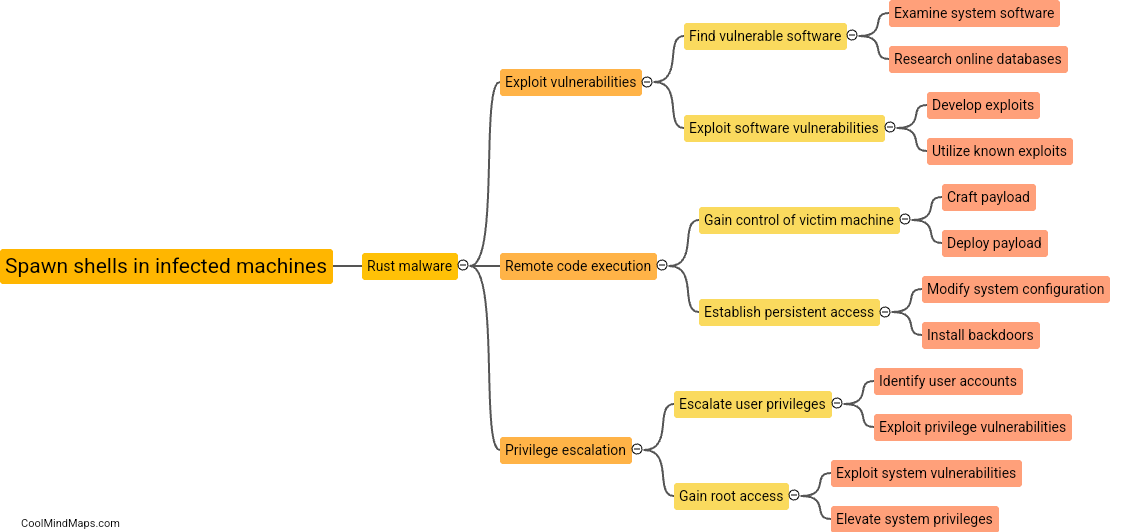
How can a rust malware spawn shells in infected machines?
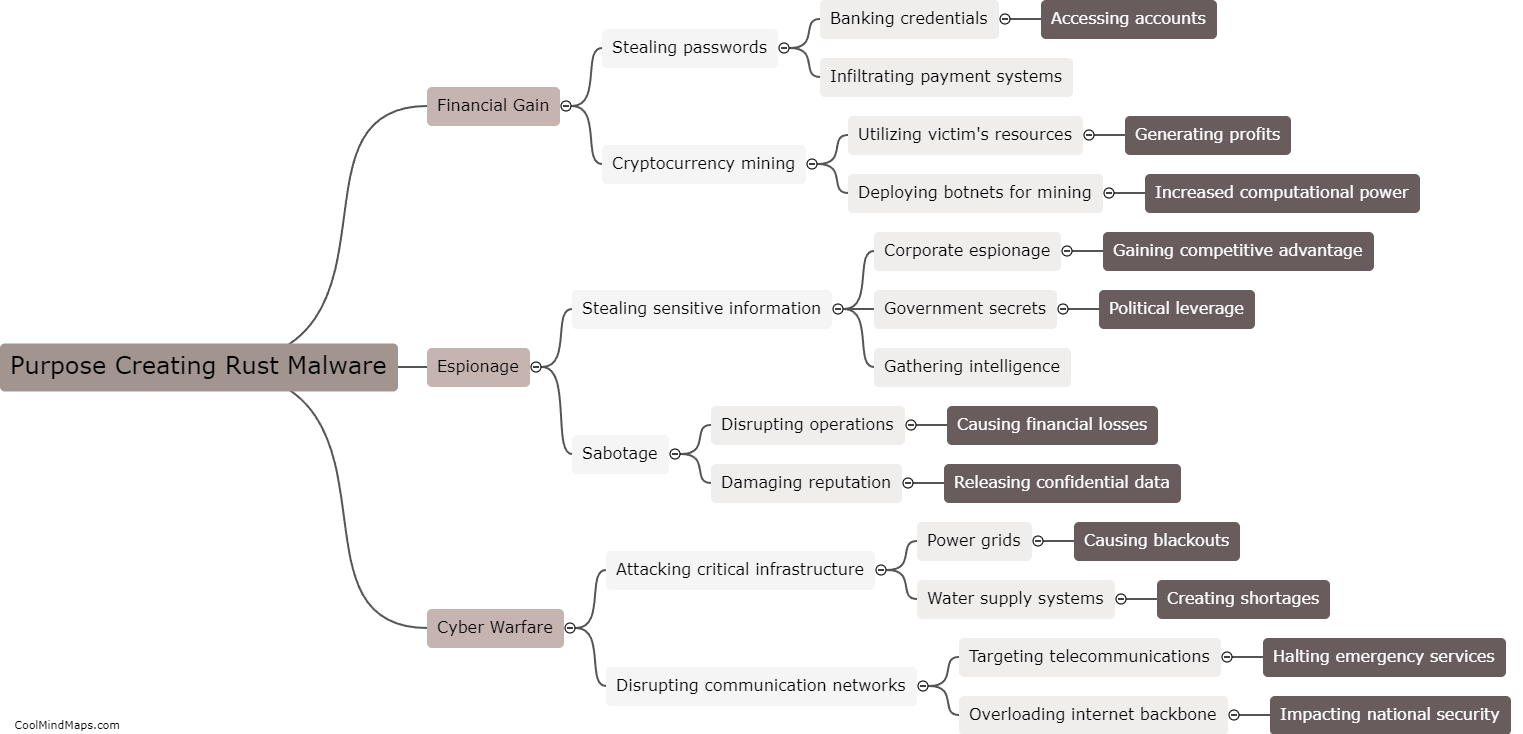
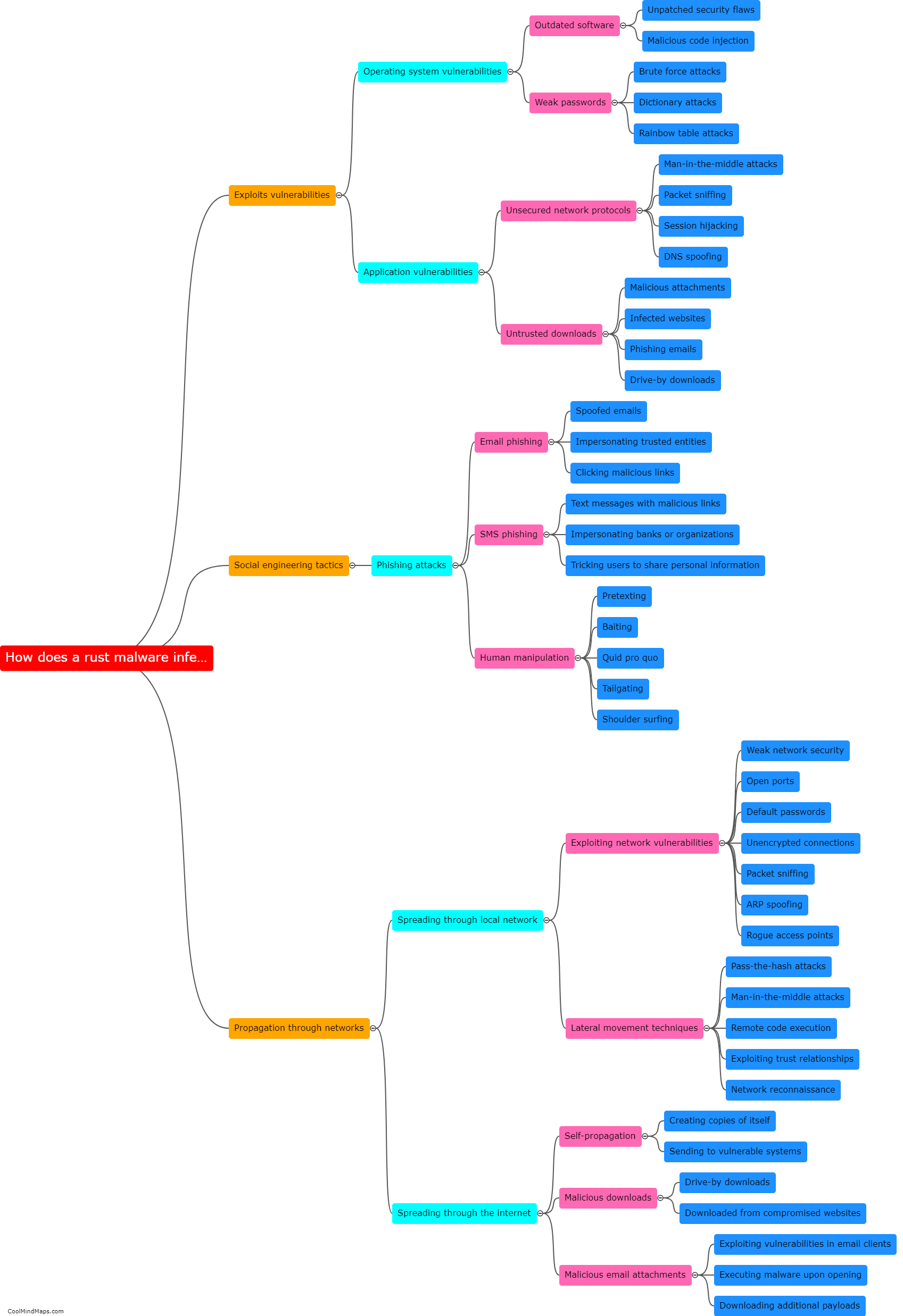
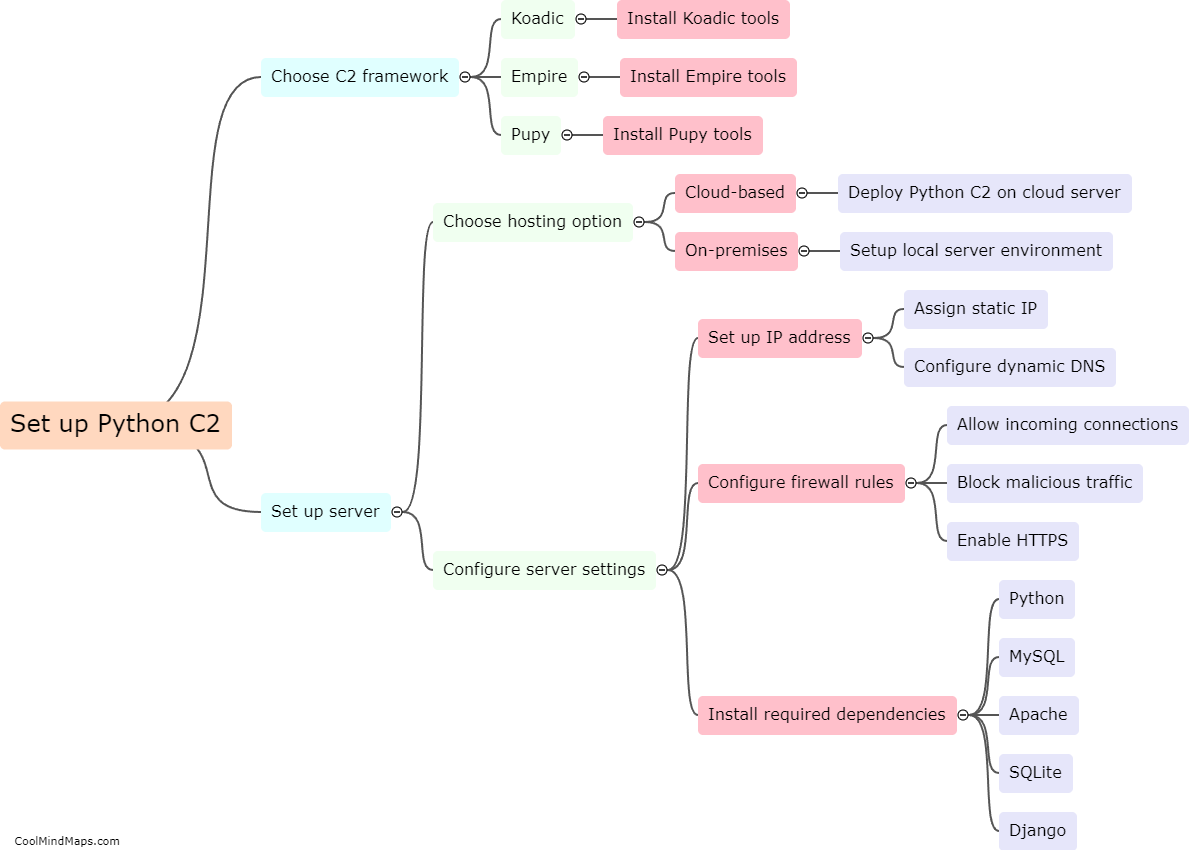
Rust malware can spawn shells in infected machines by exploiting vulnerabilities or weaknesses in the system. This can be achieved through various techniques such as code injection, privilege escalation, or remote command execution. Once the malware gains access to the system, it uses the low-level system APIs provided by the Rust programming language to create new processes or threads, which effectively spawn a shell. By spawning shells, the malware gains control over the infected machine's command-line interface, allowing the attacker to execute arbitrary commands, manipulate files, or even launch further malicious activities, resulting in a greater level of control over the compromised system.
This mind map was published on 22 October 2023 and has been viewed 113 times.