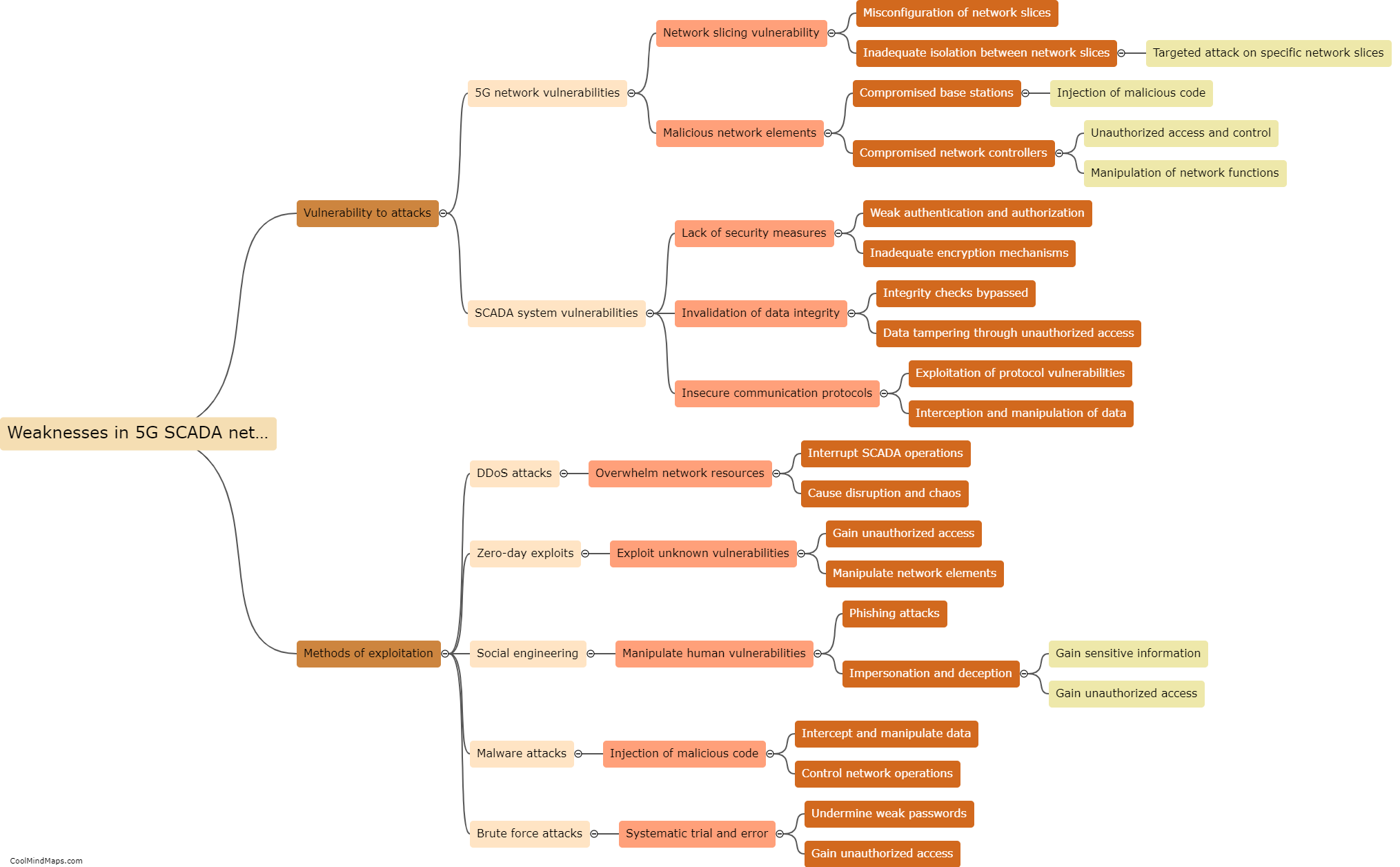
How can cybercriminals exploit the weaknesses in 5G SCADA networks?
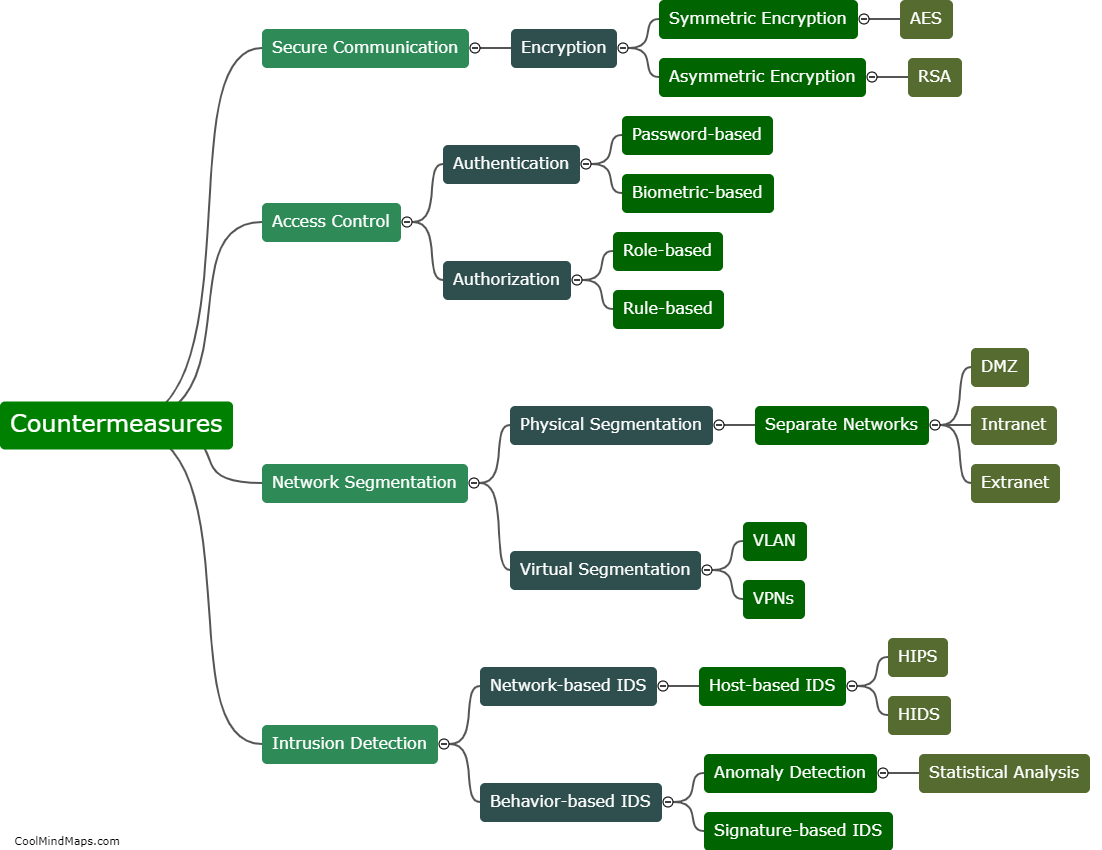
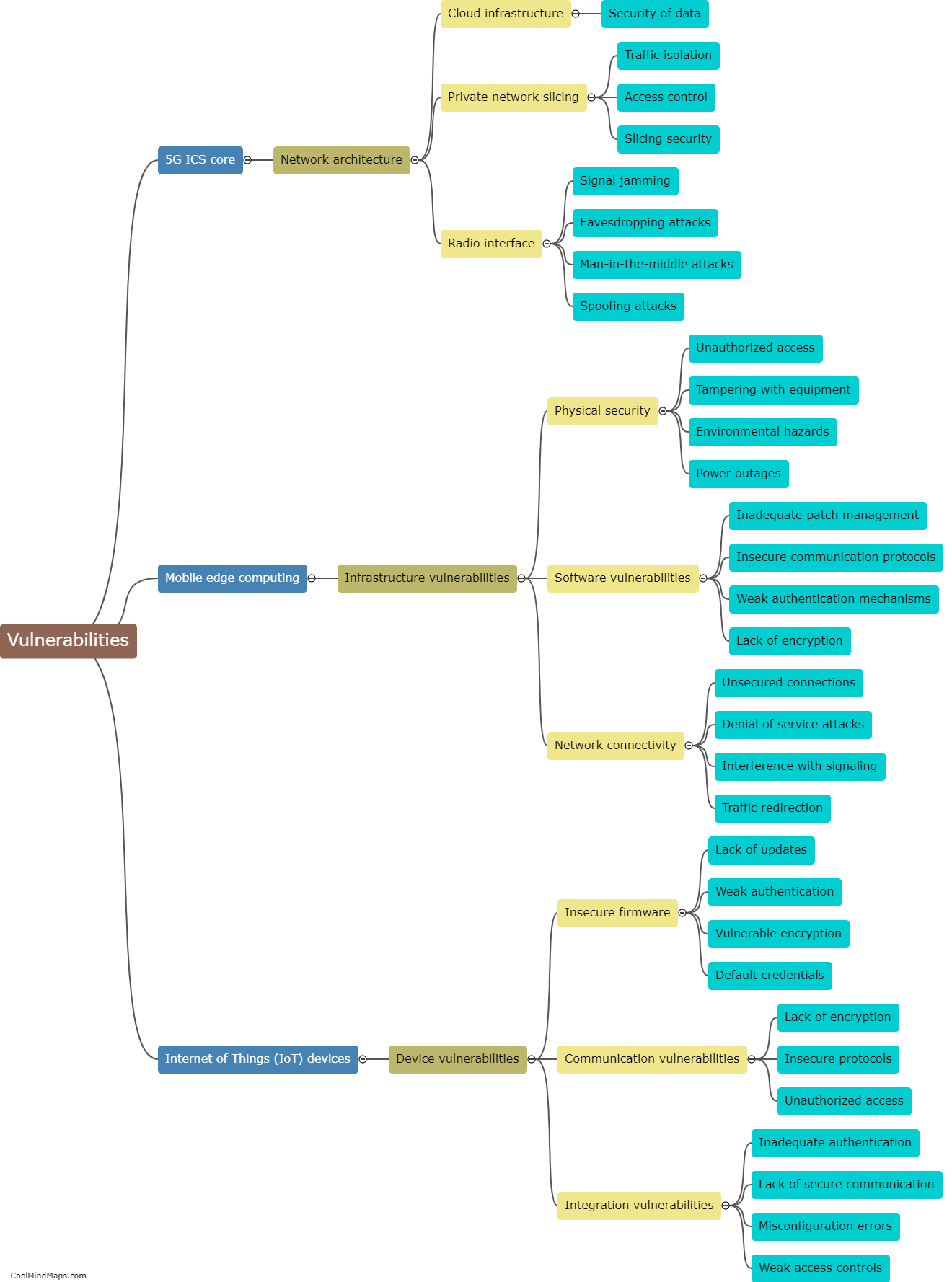
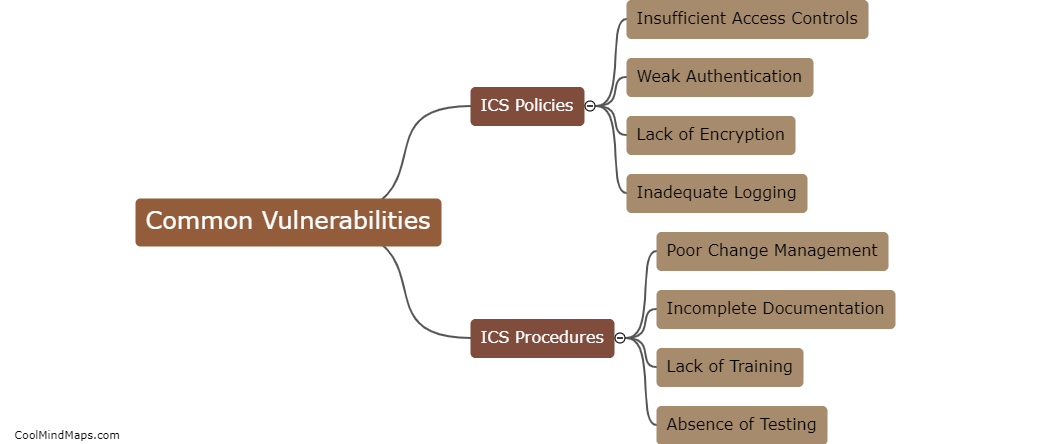
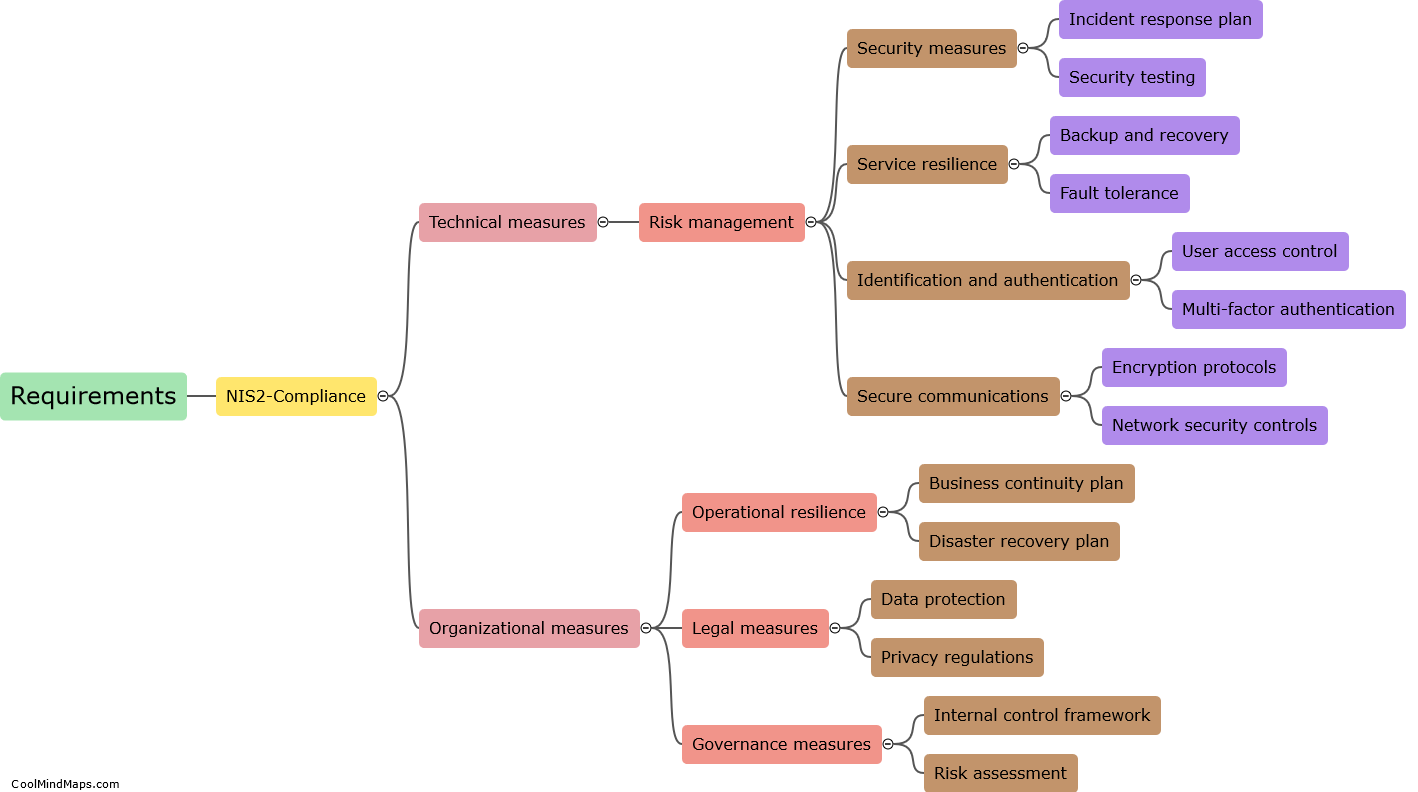
As 5G networks are being increasingly deployed in critical infrastructure sectors, such as SCADA (Supervisory Control and Data Acquisition) systems, there is growing concern about their vulnerabilities and potential exploitation by cybercriminals. Cybercriminals can exploit the weaknesses in 5G SCADA networks in various ways. Firstly, they can take advantage of the increased number of connected devices and endpoints to gain unauthorized access to the network or launch direct attacks on the SCADA systems. Additionally, the use of virtualization and software-defined networks in 5G opens up new attack vectors, where attackers can manipulate or hijack network functions and infiltrate the SCADA systems. Moreover, the low latency and high bandwidth capabilities of 5G networks can facilitate more sophisticated attacks, such as Distributed Denial of Service (DDoS) or data exfiltration attacks, disrupting or compromising the integrity of critical infrastructure operations. To defend against such exploits, robust security measures including encryption, authentication protocols, intrusion detection systems, and regular security audits must be implemented to safeguard 5G SCADA networks.
This mind map was published on 27 January 2024 and has been viewed 99 times.