How is ISO 9001:2015 structured?
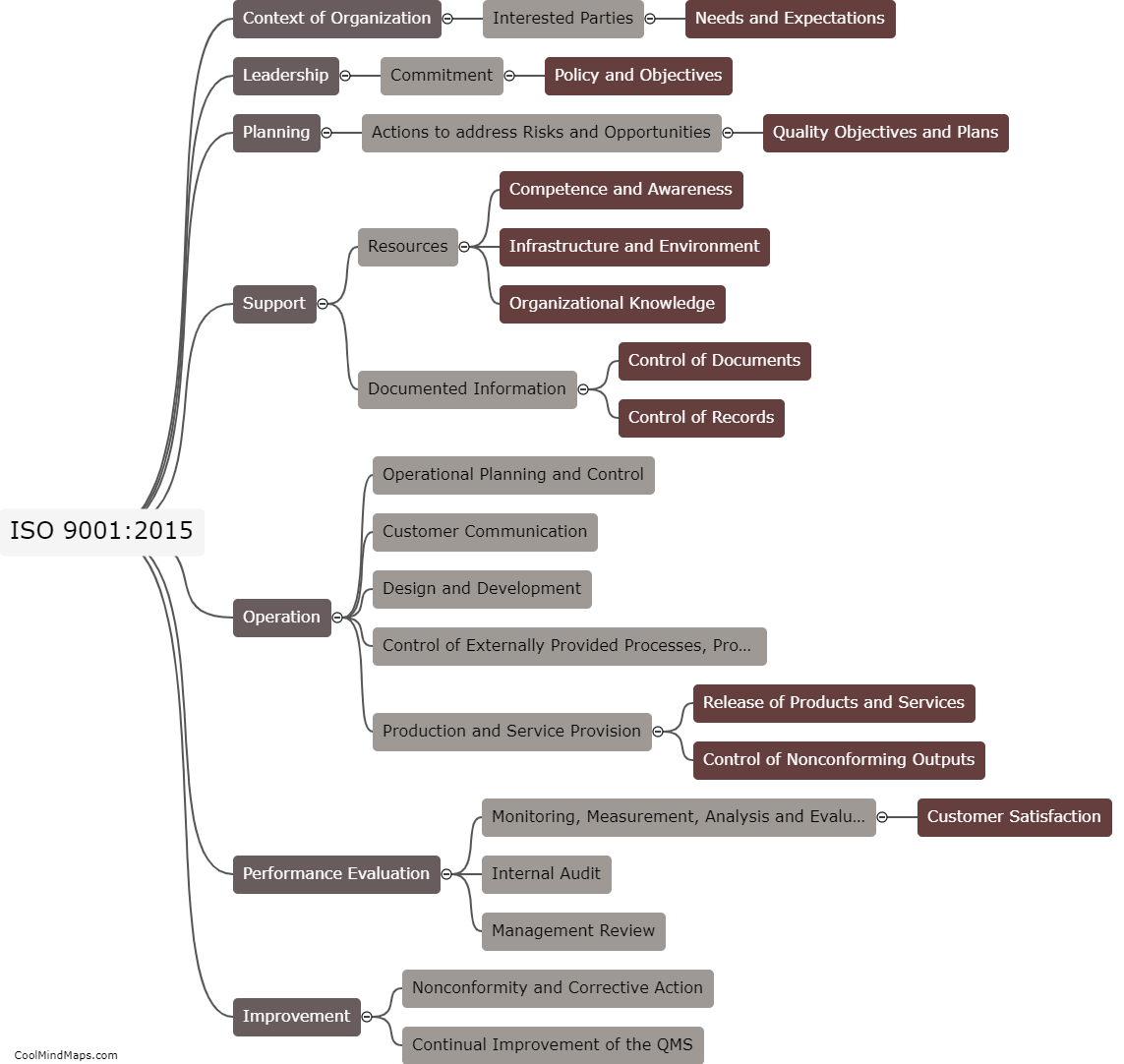
ISO 9001:2015 is structured based on a comprehensive framework that guides organizations in implementing a Quality Management System (QMS). The standard consists of ten clauses, starting with the Scope, Normative References, and Terms & Definitions. Clause 4 focuses on the Context of the organization, requiring thorough understanding of internal and external factors that affect the QMS. Clause 5 emphasizes Leadership, where top management takes responsibility for the QMS, setting quality goals and ensuring their achievement. The next two clauses, 6 and 7, address Planning and Support respectively, including actions like risk assessment, resource management, and competency development. Clause 8 entails Operation, emphasizing process management and controlling quality in production or service delivery. Clause 9 covers Performance Evaluation, necessitating the monitoring, measuring, analysis, and improvement of the QMS. Finally, Clause 10 outlines the requirements for Continuous Improvement, encouraging organizations to constantly enhance their processes, products, and customer satisfaction. ISO 9001:2015 aims to provide a flexible structure that can be tailored to any organization, promoting consistency, efficiency, and continual improvement.
This mind map was published on 27 January 2024 and has been viewed 91 times.