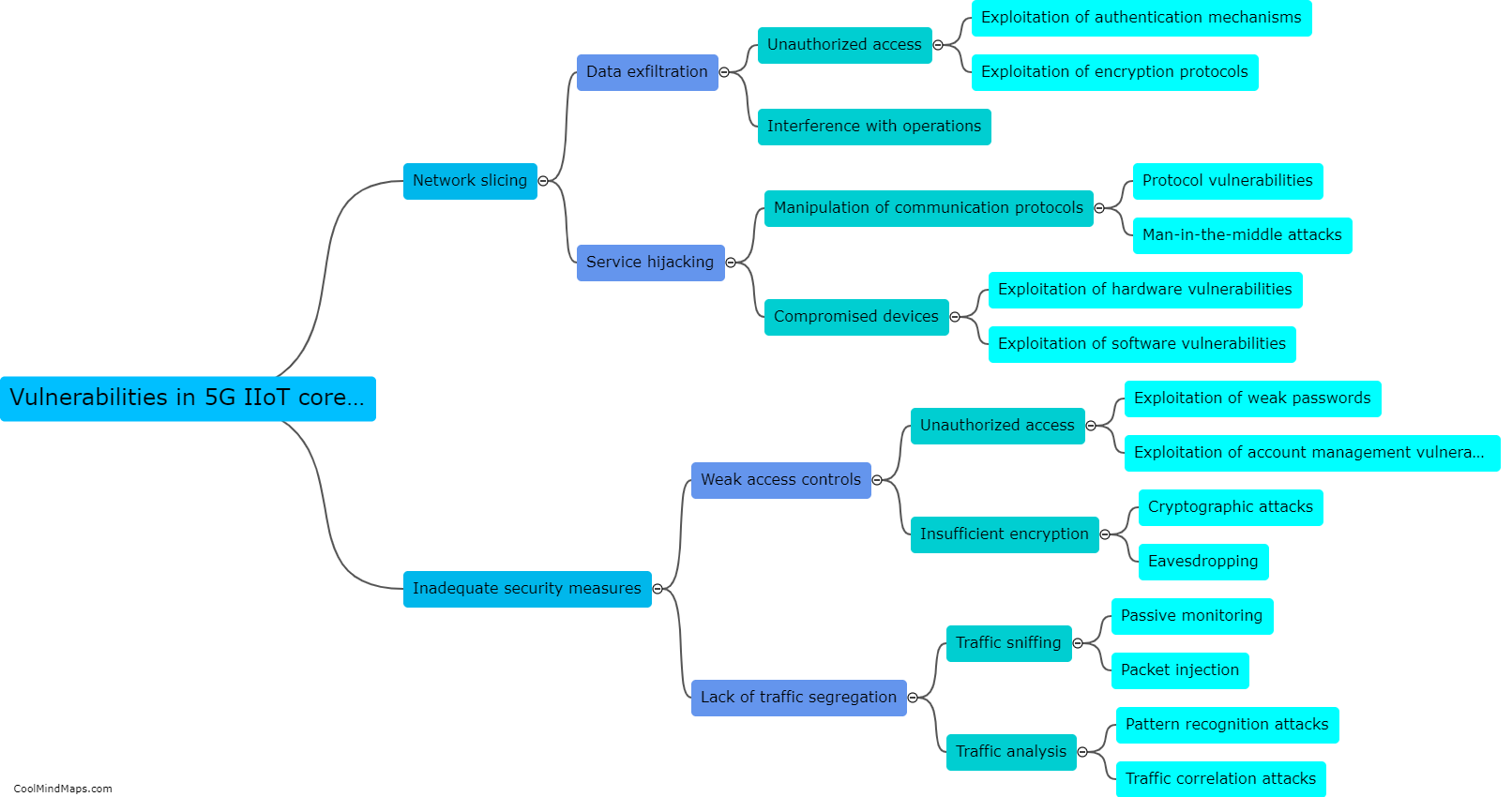
What are the potential attacks on 5G IIoT core networks?
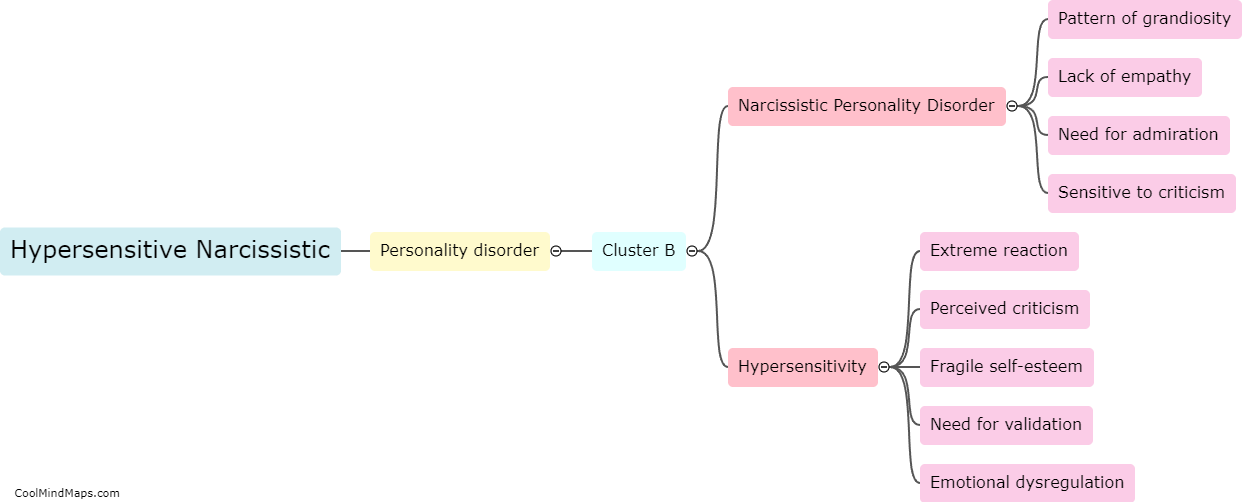
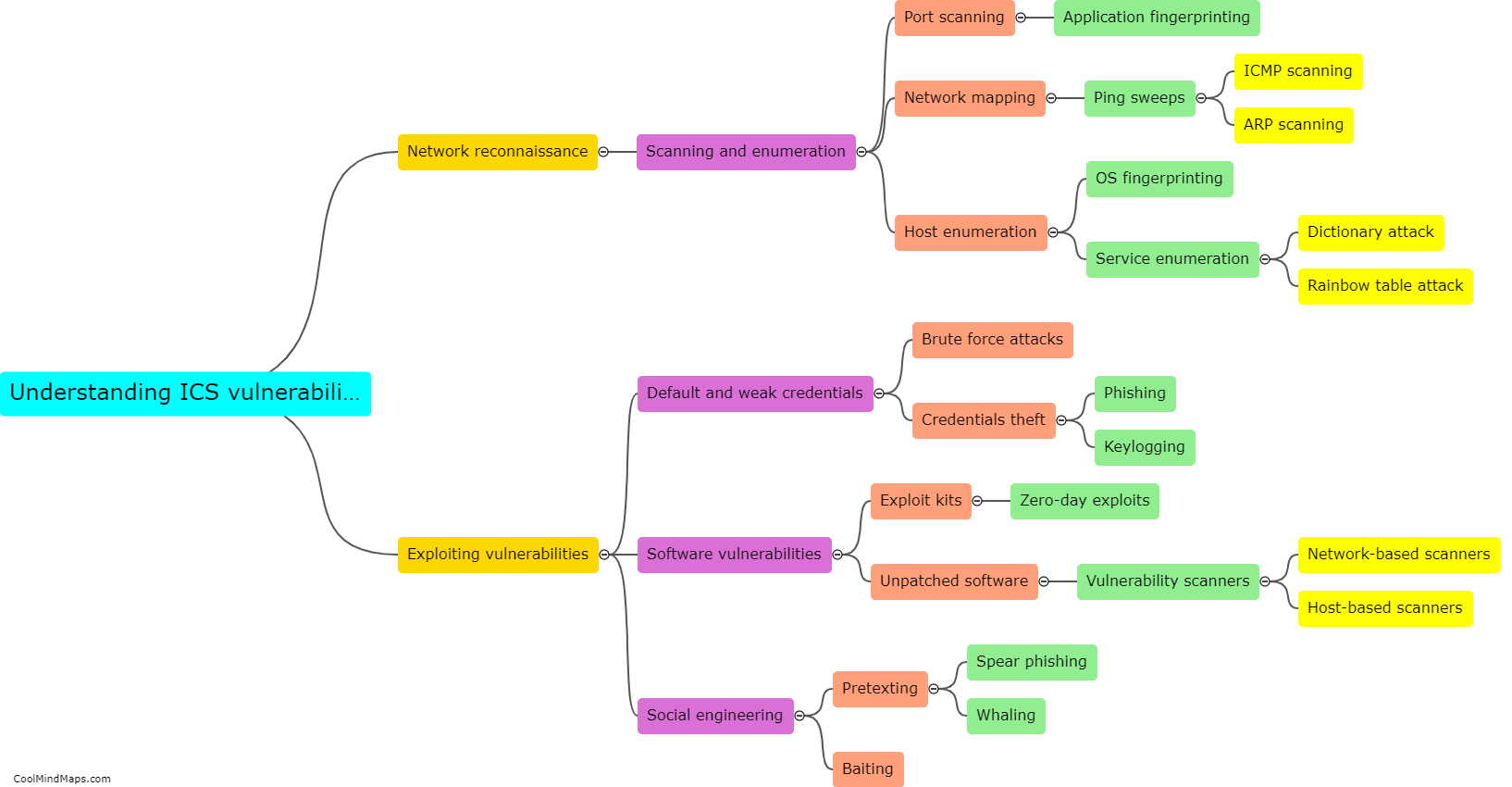
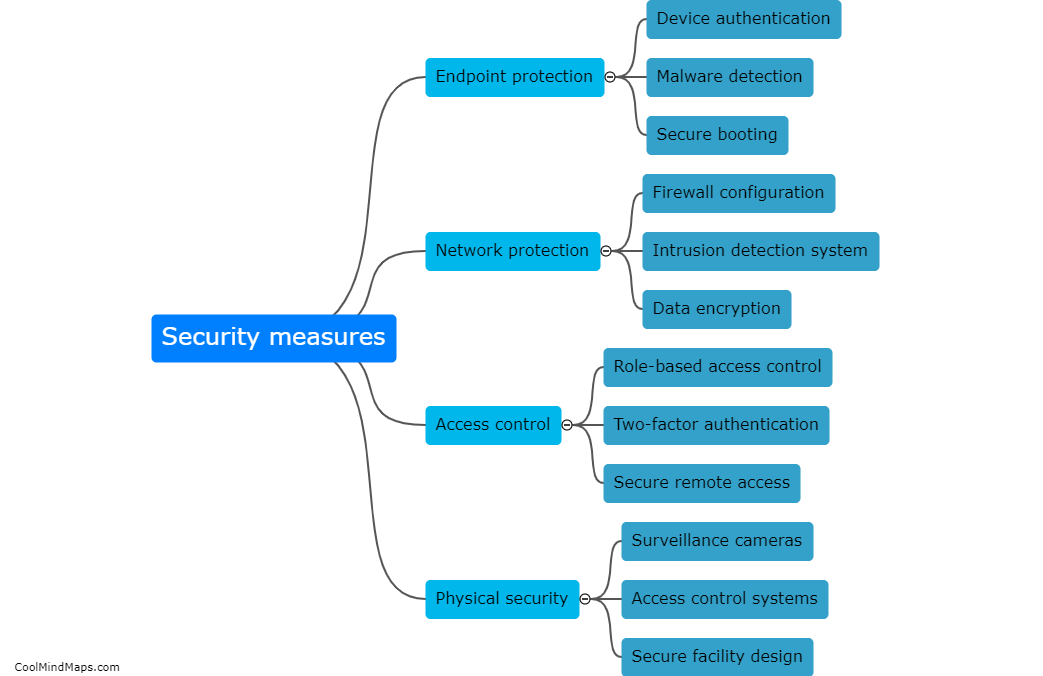
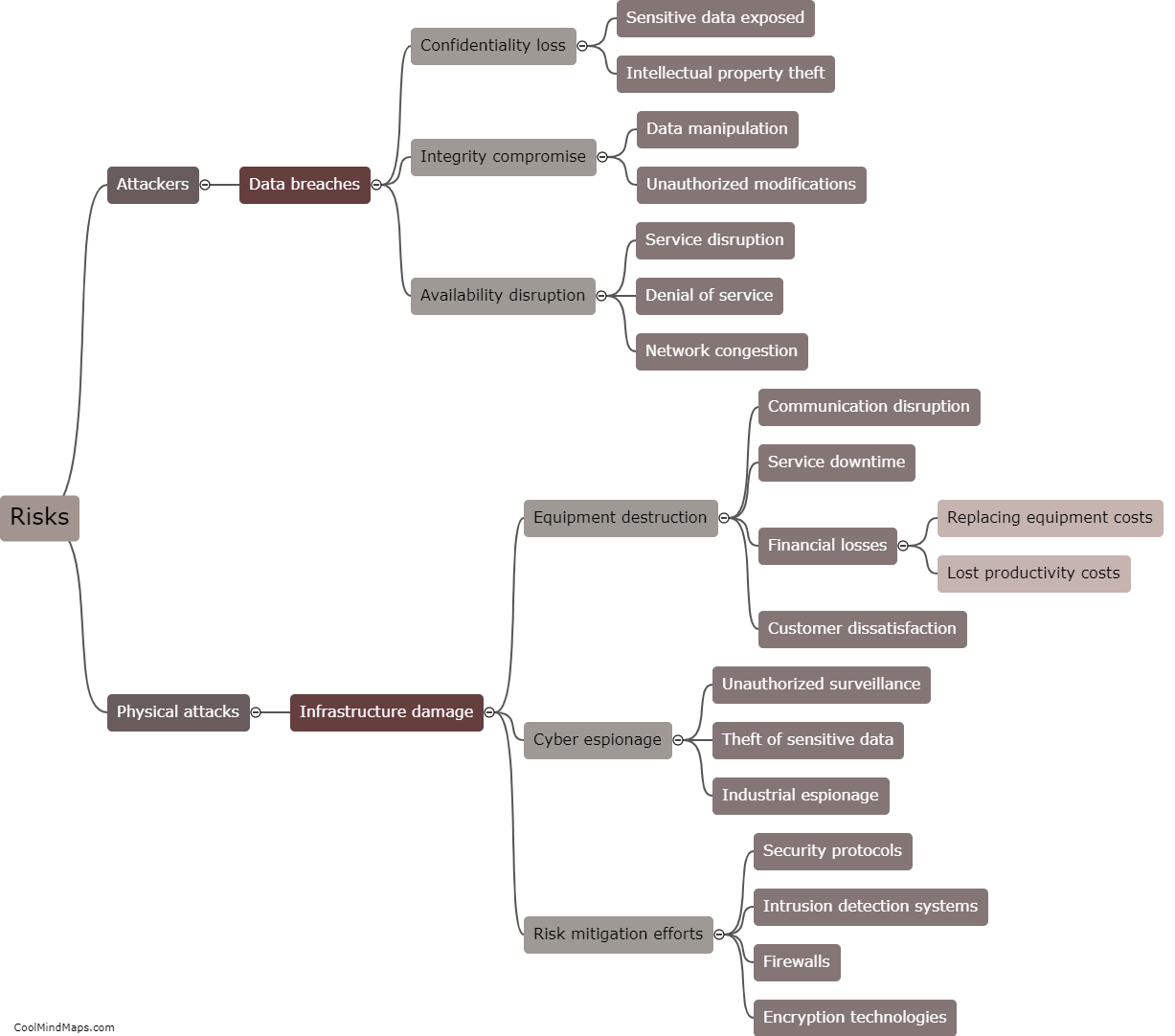
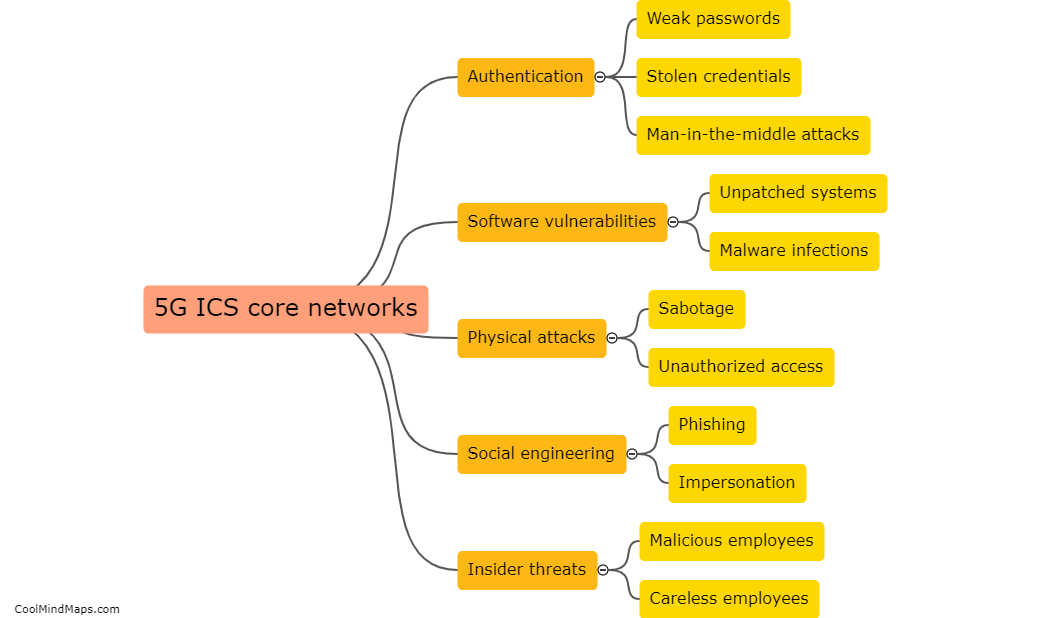
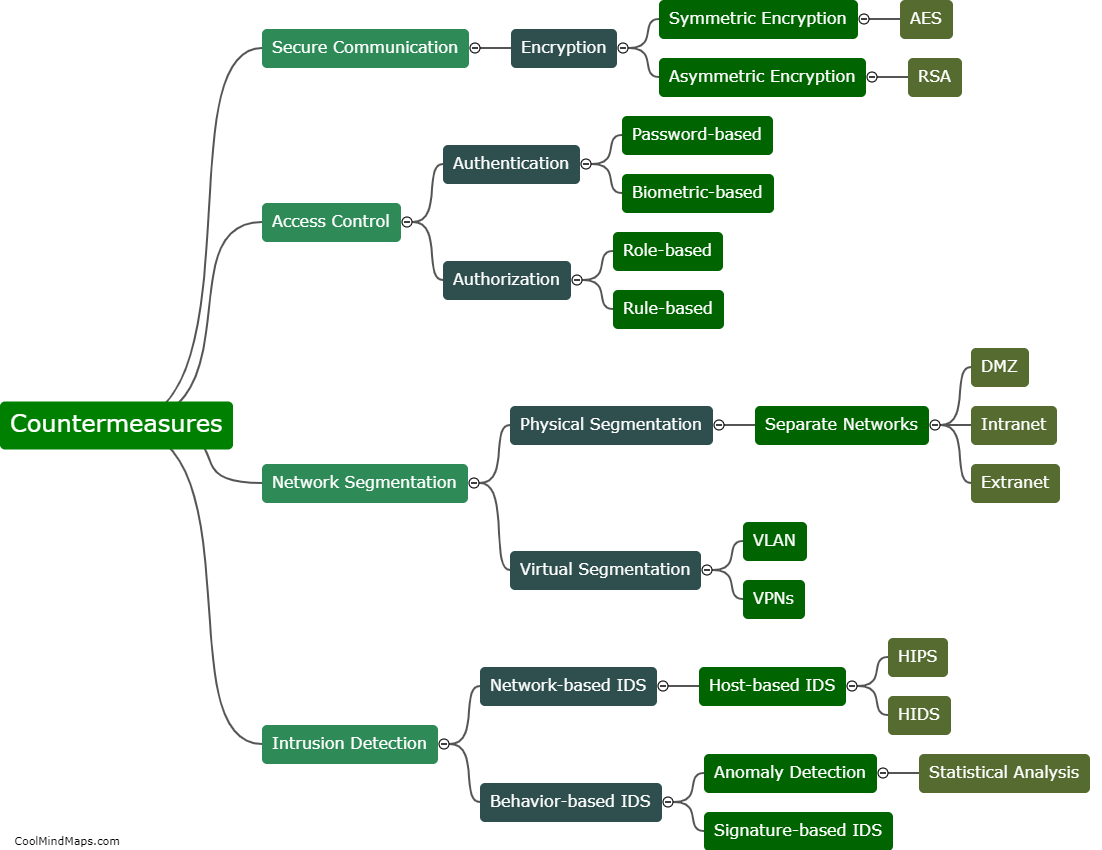
As 5G technology evolves and Industrial Internet of Things (IIoT) applications become more prevalent, there is a growing concern about potential attacks on the 5G IIoT core networks. These attacks can have severe consequences for critical infrastructure and industrial sectors. Some potential attacks on 5G IIoT core networks include distributed denial of service (DDoS) attacks, where a multitude of compromised devices overwhelm the network, causing disruption and downtime. Additionally, man-in-the-middle attacks can occur, where an attacker intercepts and alters communication between devices and the core network, allowing them to gain unauthorized access or manipulate data. Other threats include network slicing vulnerabilities, where an attacker can compromise the isolation between network slices, leading to unauthorized access to sensitive applications or even bringing down the entire network. As the adoption of 5G IIoT continues to grow, it is crucial to implement robust security measures to protect against these potential attacks and safeguard critical infrastructure and operations.

This mind map was published on 27 January 2024 and has been viewed 107 times.