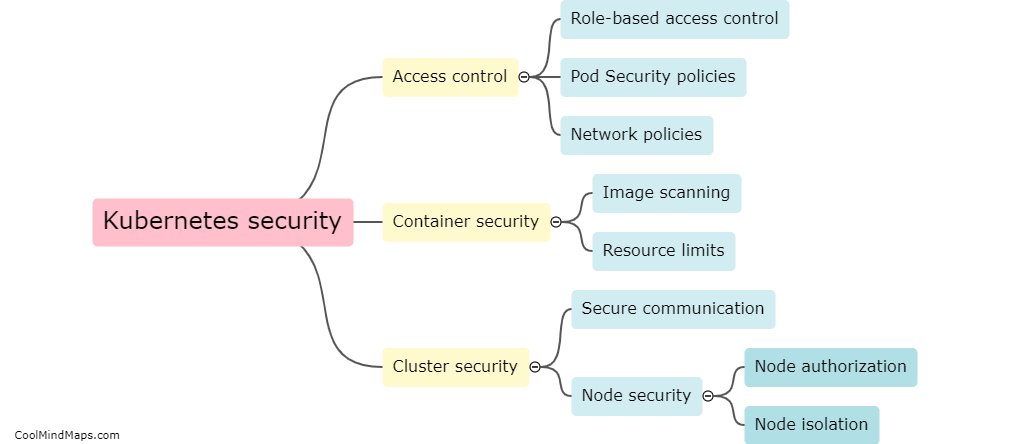
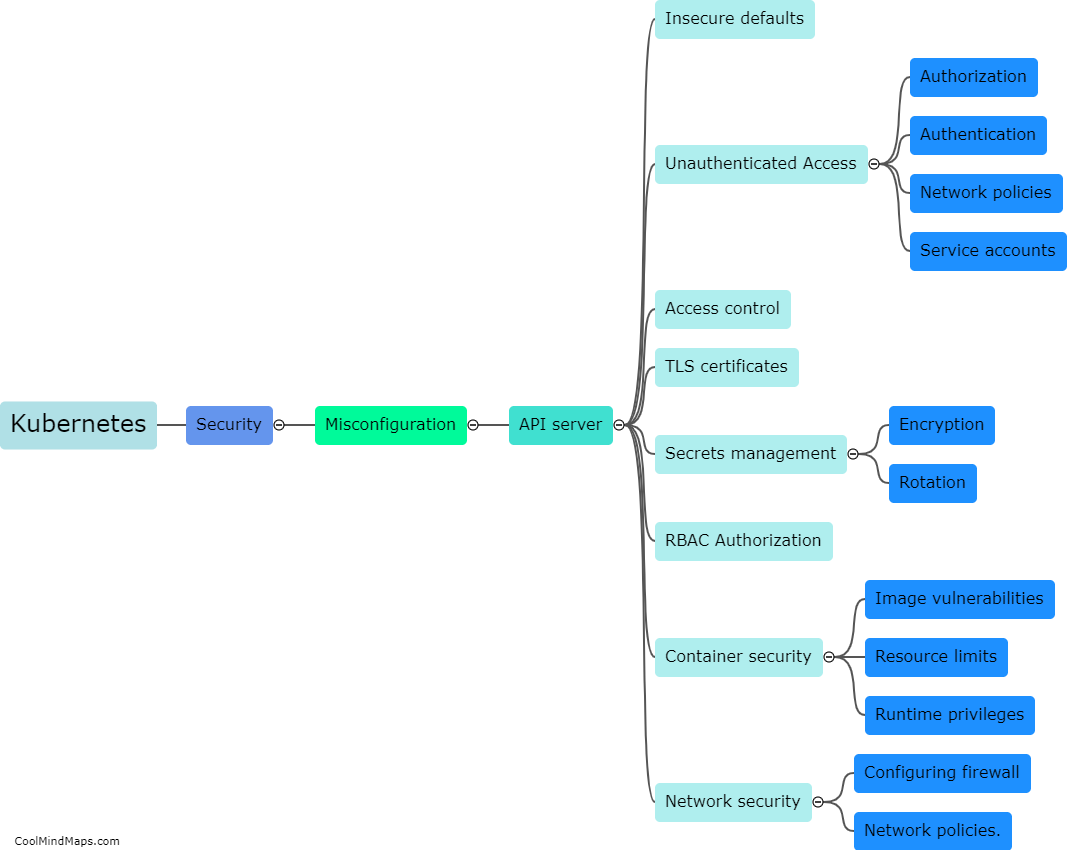
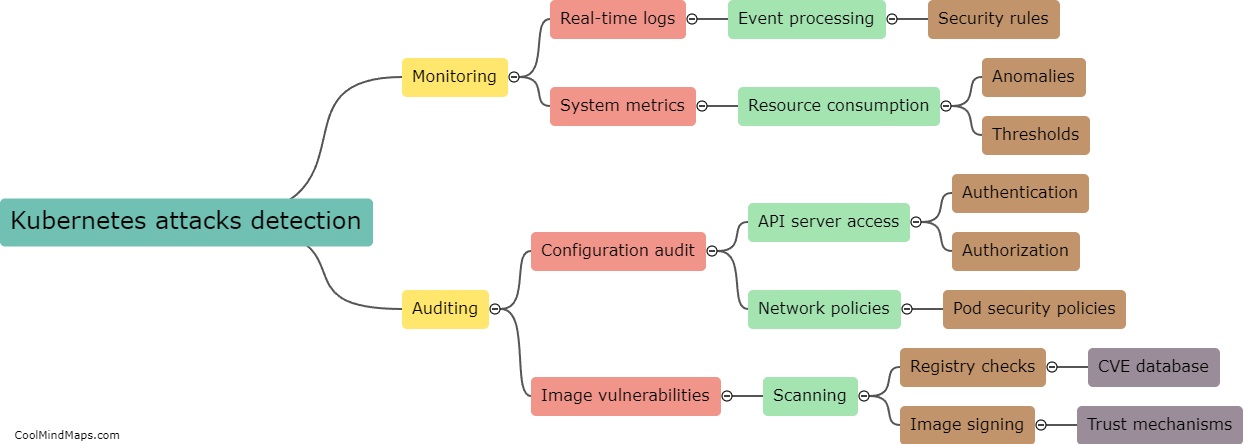
How can Kubernetes attacks be detected?
Kubernetes attacks can be detected through various ways such as monitoring network traffic, observing suspicious behavior in the system logs, or using external threat intelligence feeds. Additionally, setting up an intrusion detection system can help in identifying anomalies in Kubernetes clusters. Alerting mechanisms such as notifications and alarms can also be set up to inform IT security personnel in real-time when an attack is detected, enabling a quick response to mitigate the damage caused by the attack. Regular assessments of Kubernetes environments can also help detect vulnerabilities before attackers can exploit them. It is important to have a robust security strategy in place to safeguard against Kubernetes attacks.
This mind map was published on 27 June 2023 and has been viewed 105 times.