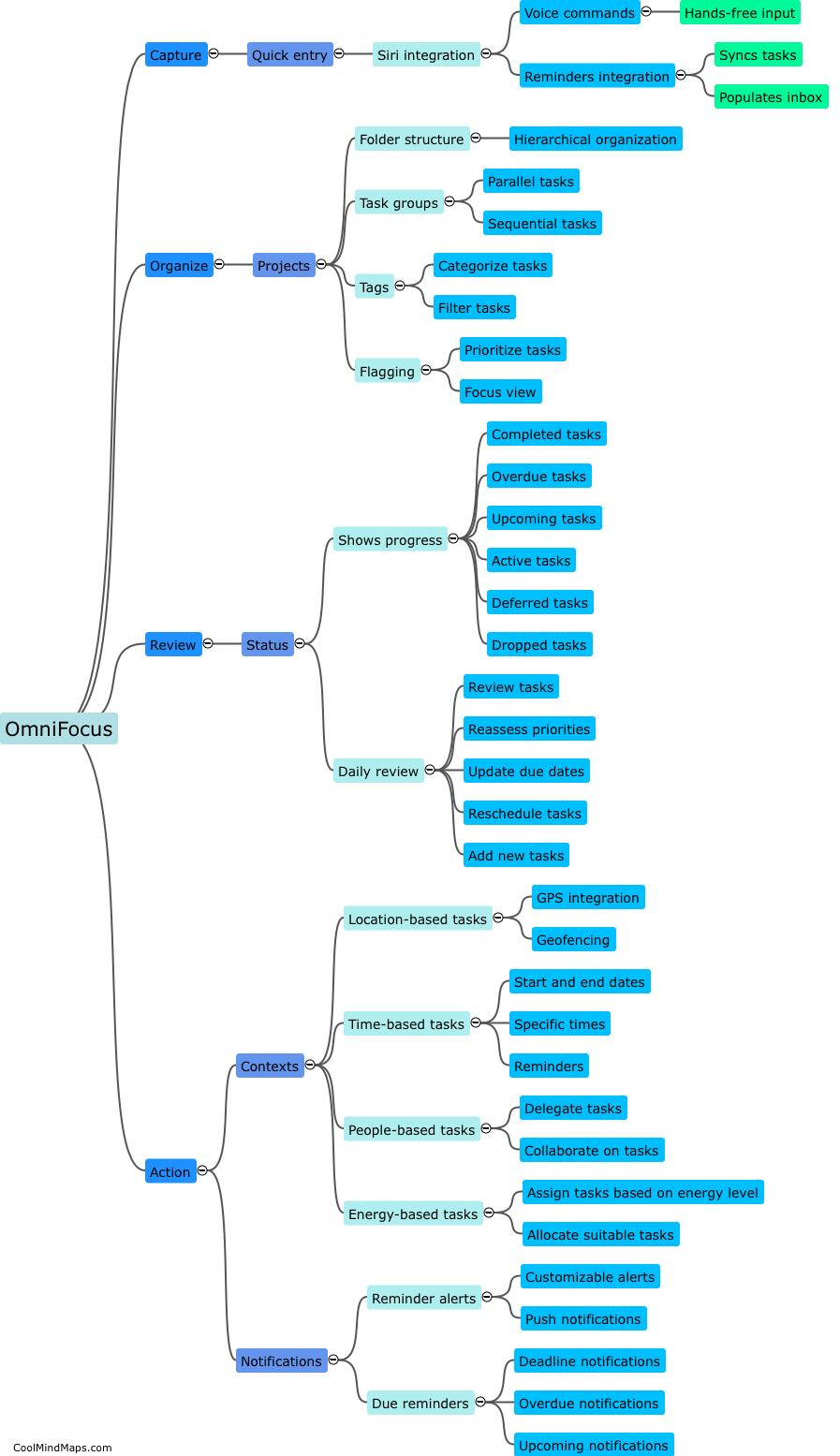
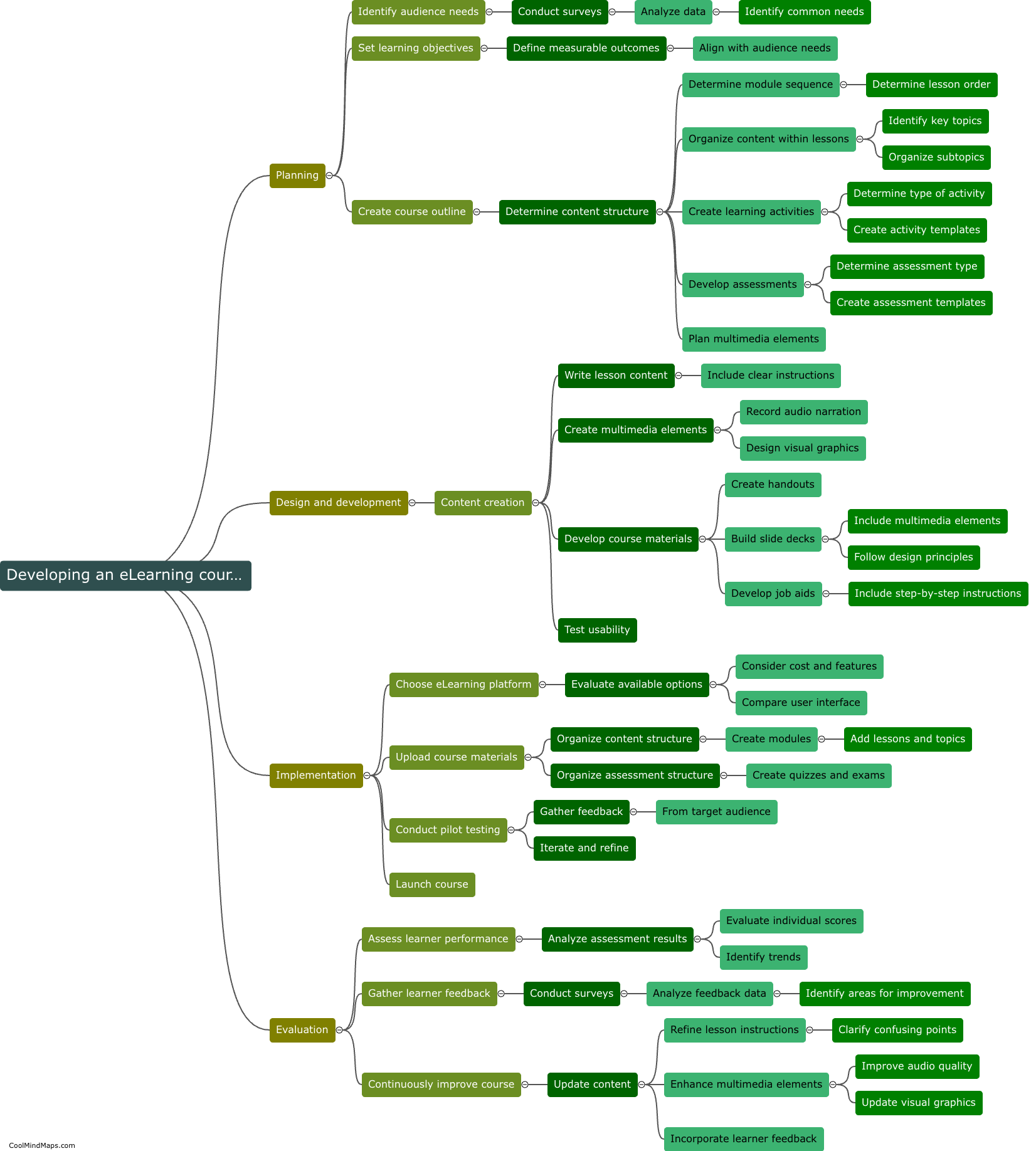
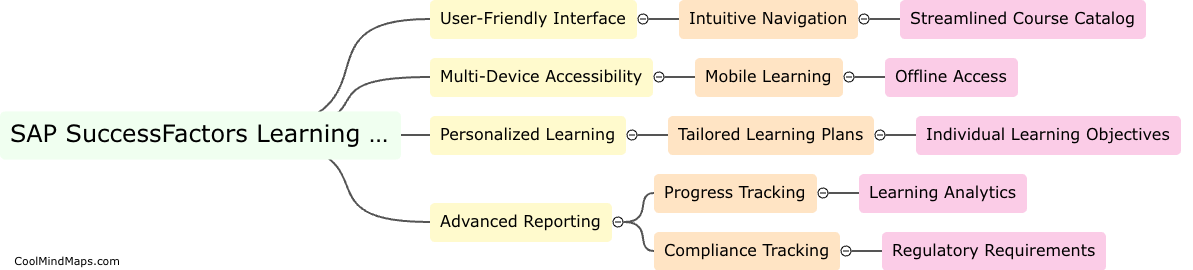
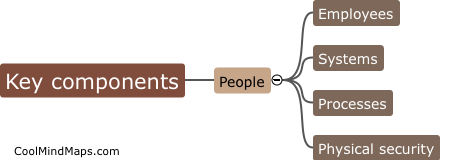
What are the key components of an information security program?
The key components of an information security program include policies and procedures, risk assessment and management, access controls, training and awareness, incident response and recovery, and ongoing monitoring and evaluation. Policies and procedures outline the rules and guidelines that govern how information is protected. A thorough risk assessment helps identify potential vulnerabilities and threats, enabling effective risk management strategies to be implemented. Access controls involve restricting access to sensitive information to authorized individuals only. Training and awareness programs educate employees about their roles and responsibilities in safeguarding information. Incident response and recovery plans ensure a timely and effective response to security incidents. Ongoing monitoring and evaluation help identify any weaknesses in the security program and provide continual improvement. Overall, a strong information security program comprises a combination of technical, administrative, and physical safeguards to protect against threats and vulnerabilities.
This mind map was published on 10 January 2024 and has been viewed 93 times.