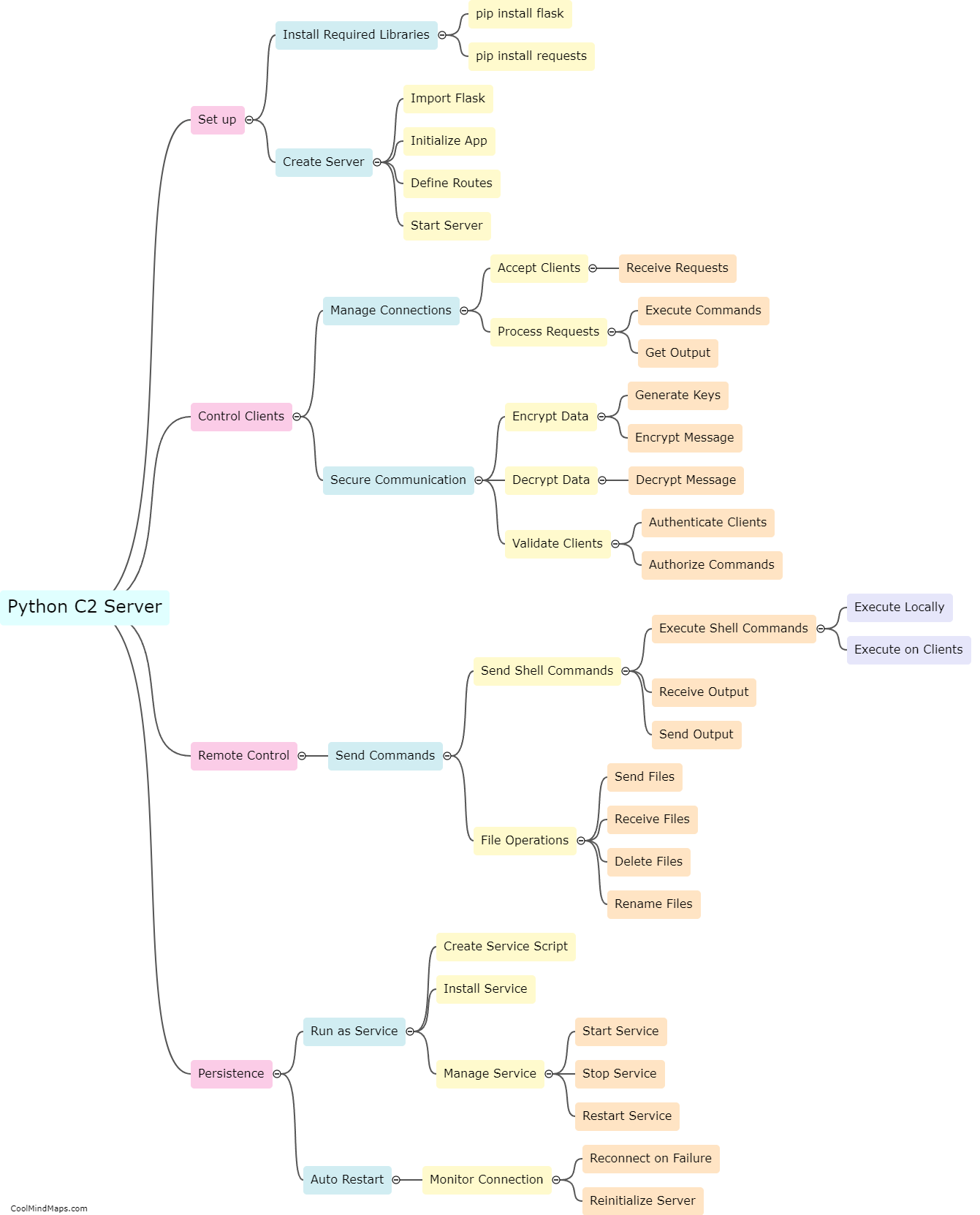
How does a C2 server work?
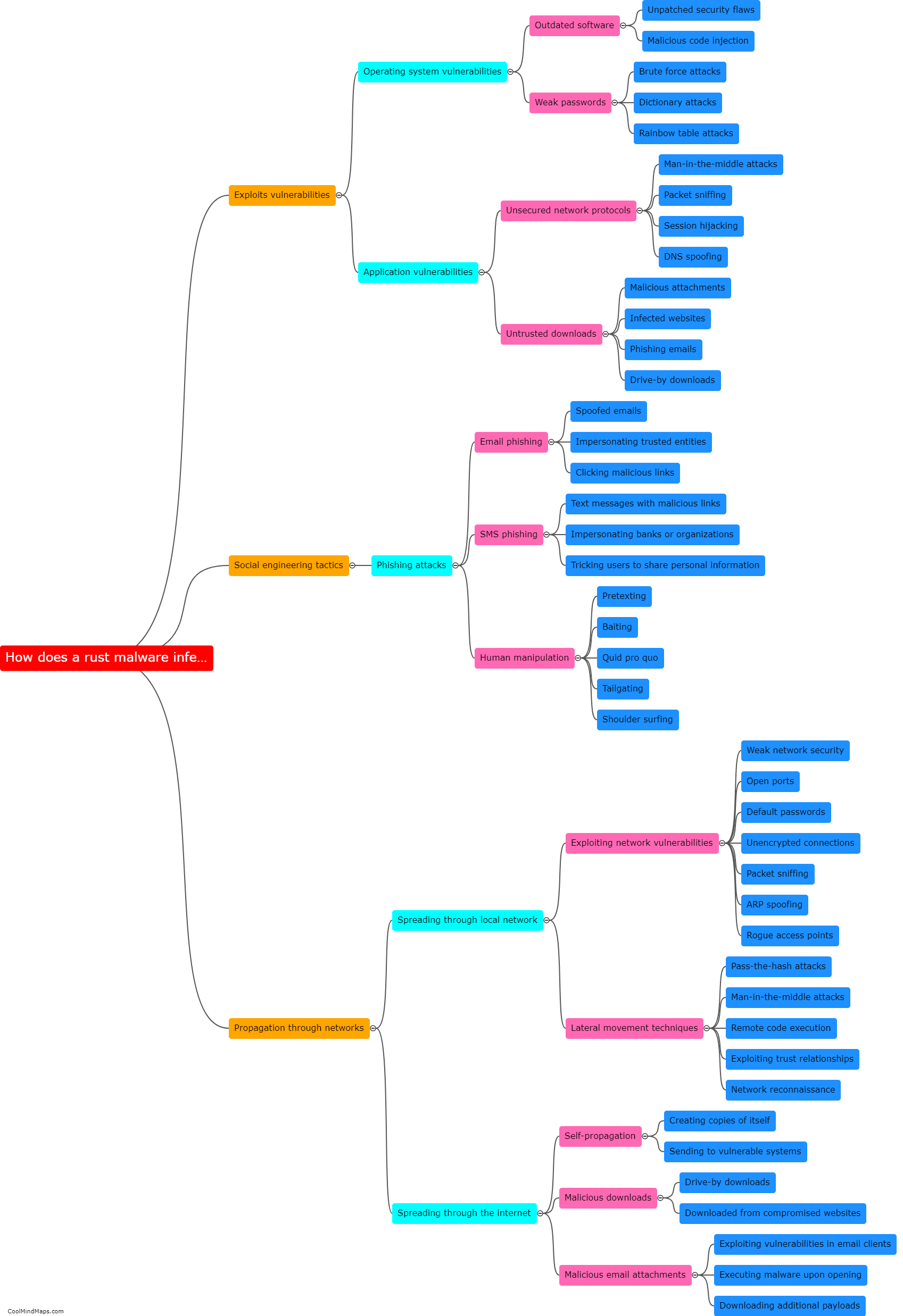
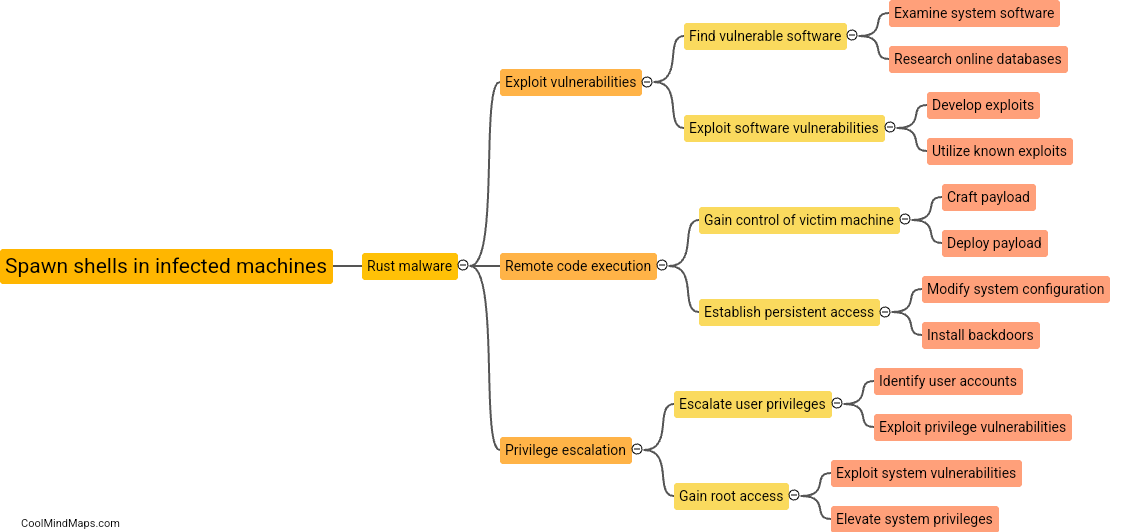
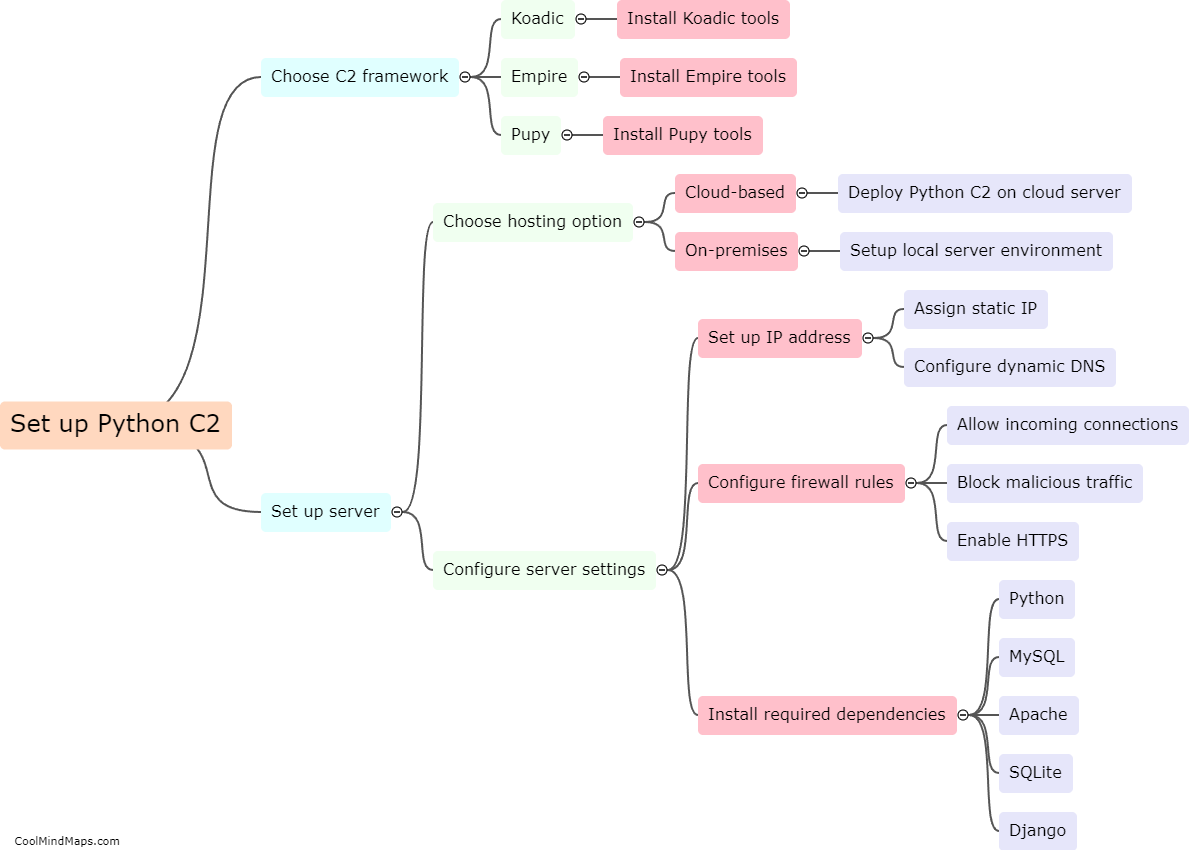
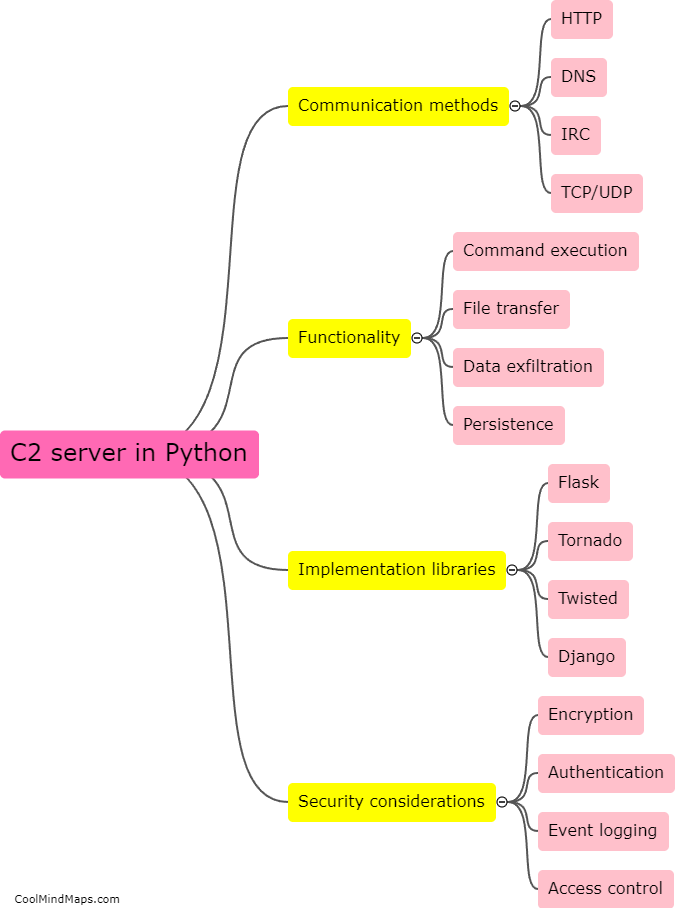
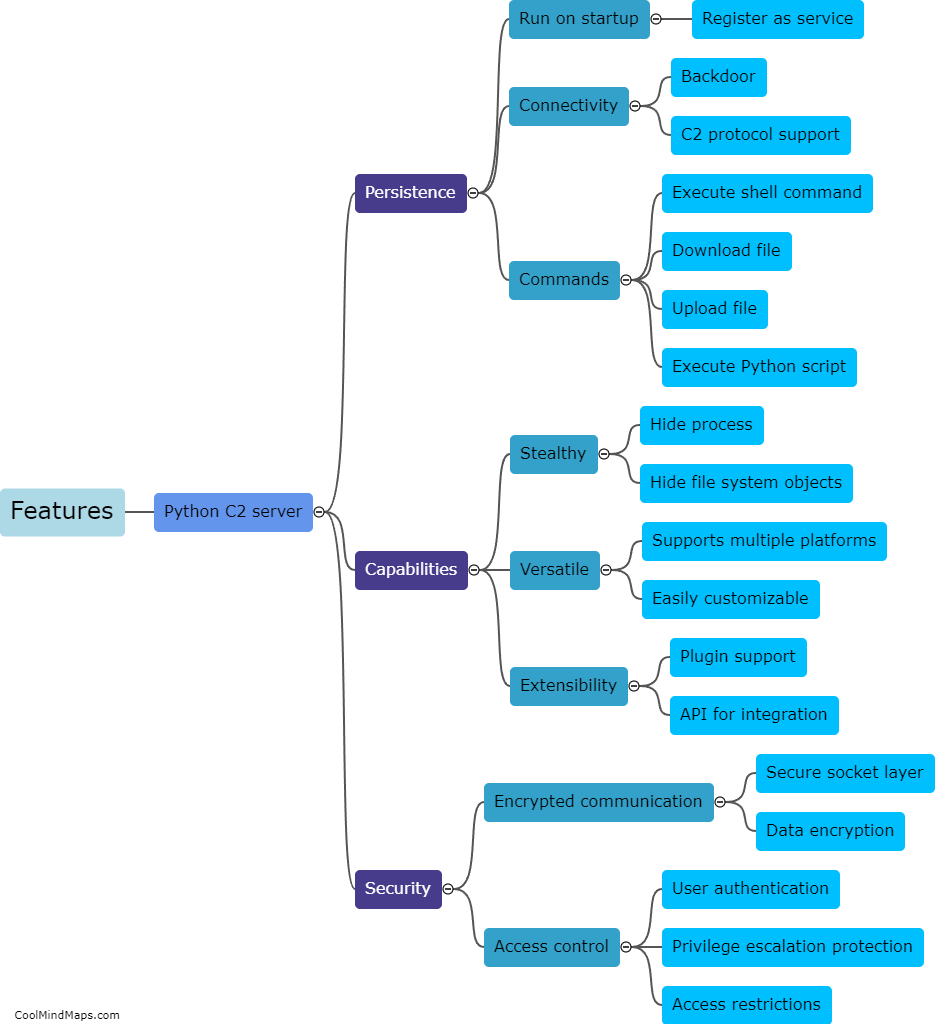
A Command-and-Control (C2) server is a vital component of a cyber attack or a botnet. It serves as the communication hub between the attacker or botnet operator and the compromised devices or bots. A C2 server works by establishing a connection with the compromised devices, often referred to as clients or zombies. It allows the attacker to send commands, updates, and instructions to the compromised devices, and in return, receive data, execute tasks, or coordinate actions. The communication between the C2 server and the clients is usually established through various protocols like HTTP, IRC, or even custom-built communication channels. To avoid detection, C2 servers may utilize sophisticated techniques such as domain generation algorithms (DGA) to dynamically generate domain names or encryption mechanisms to obfuscate the traffic. C2 servers enable attackers to control and coordinate the malicious activities of the compromised devices, making them a crucial element in cyber attacks.
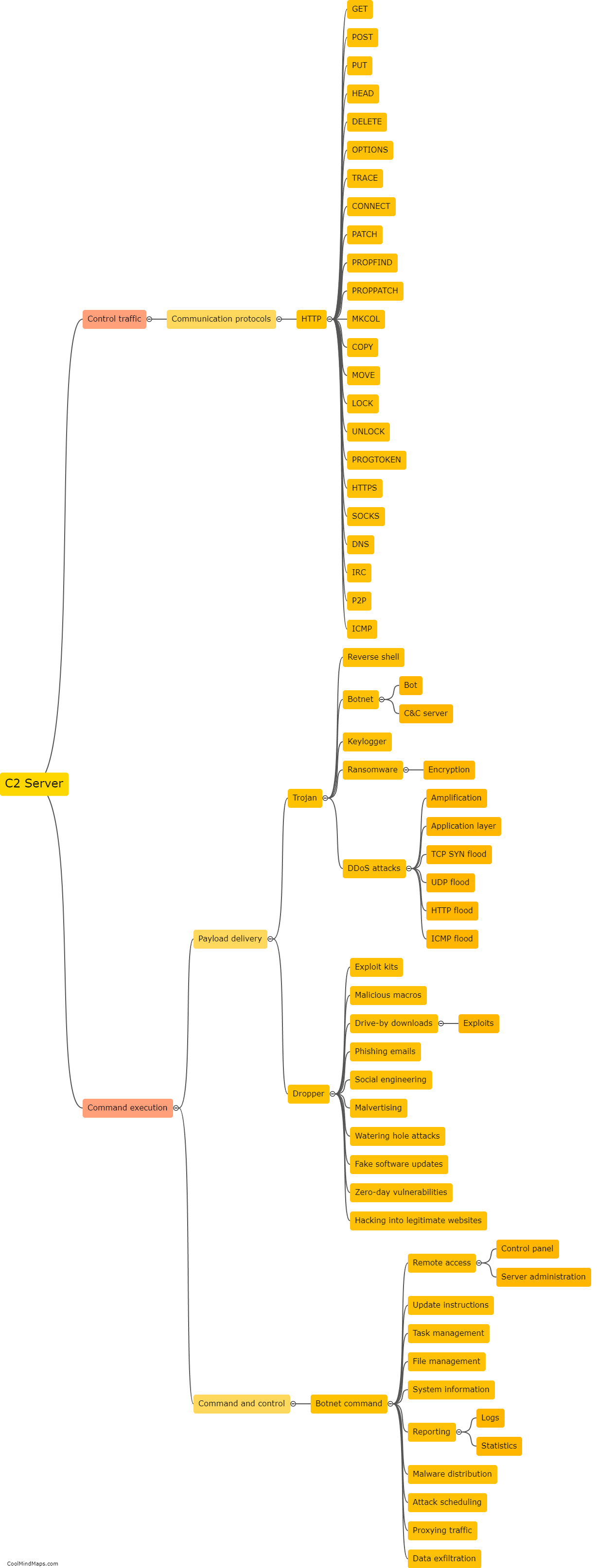
This mind map was published on 8 November 2023 and has been viewed 108 times.