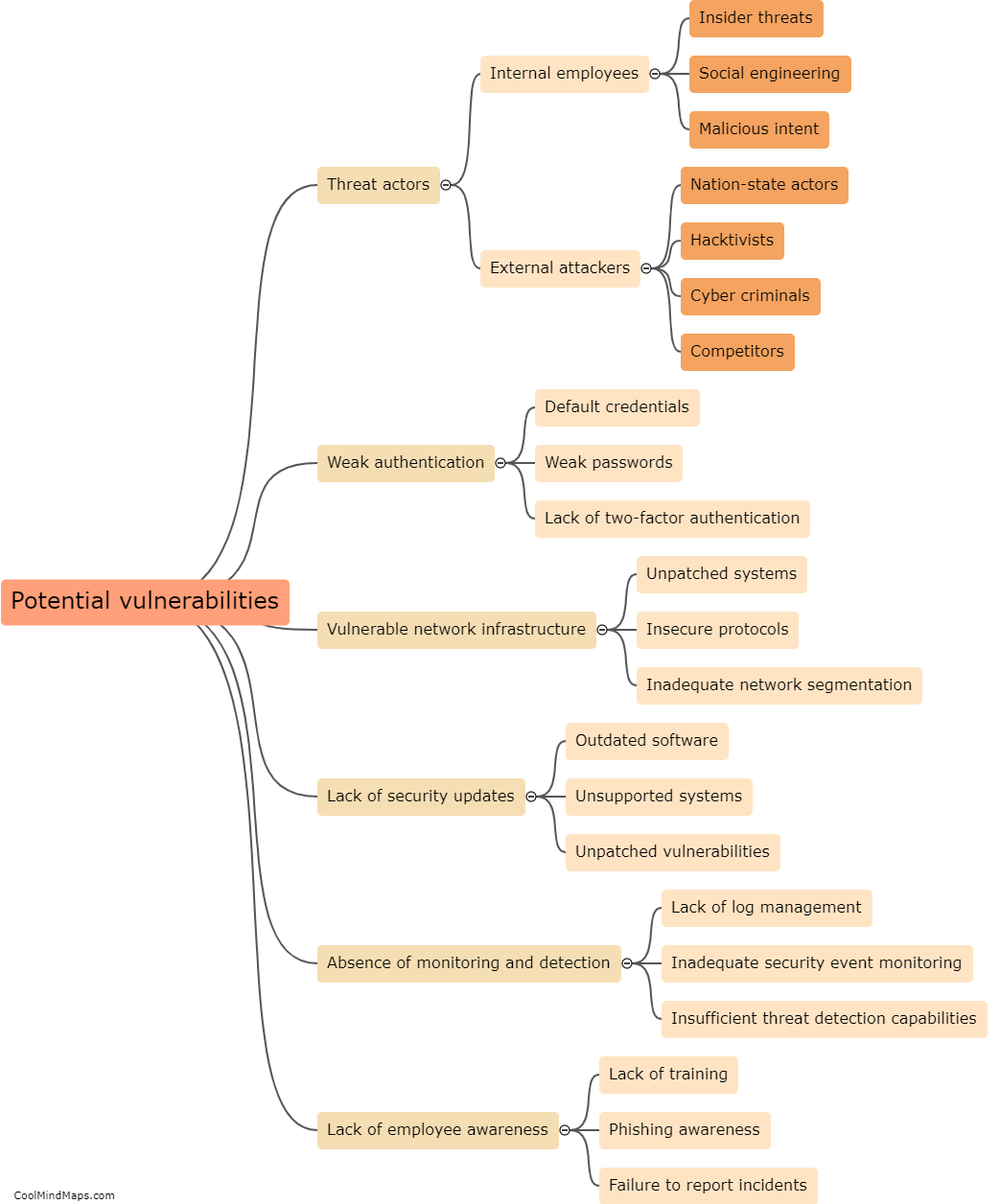
What are the potential vulnerabilities in existing ICS security measures?
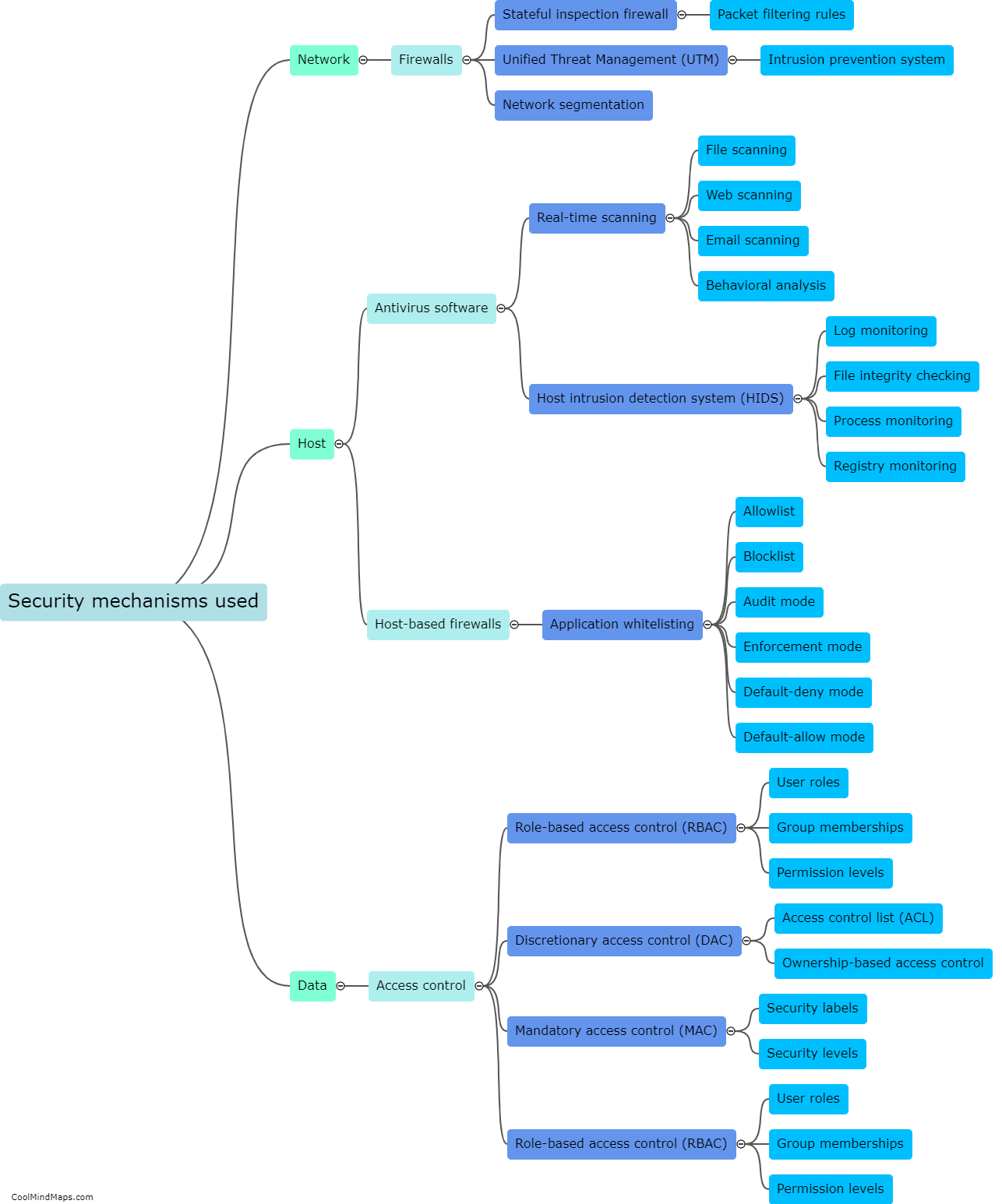
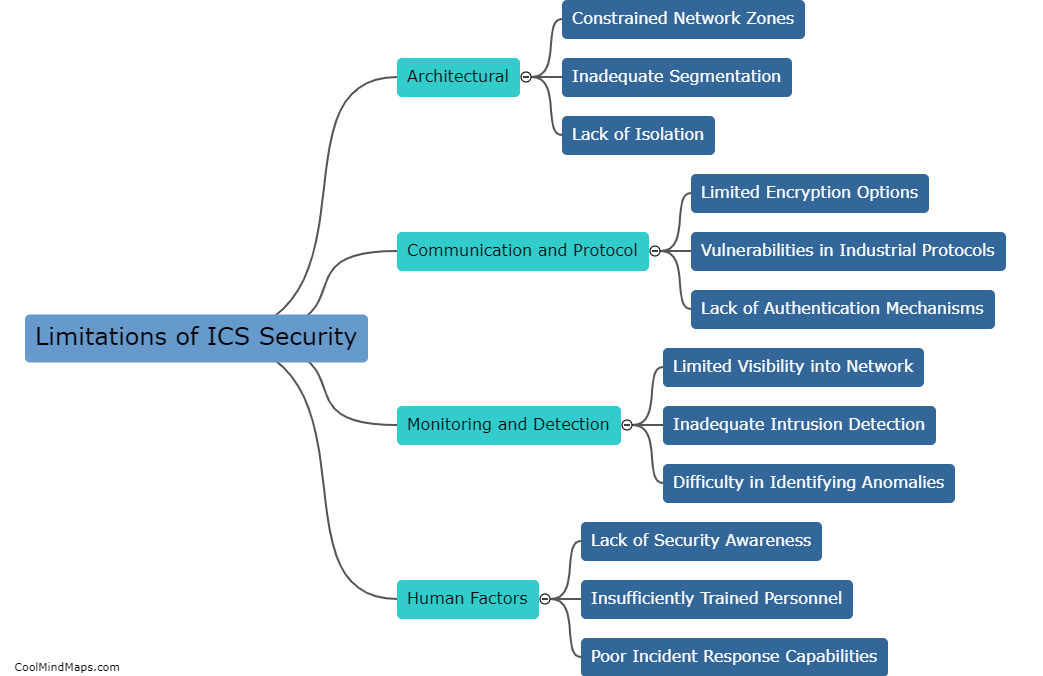
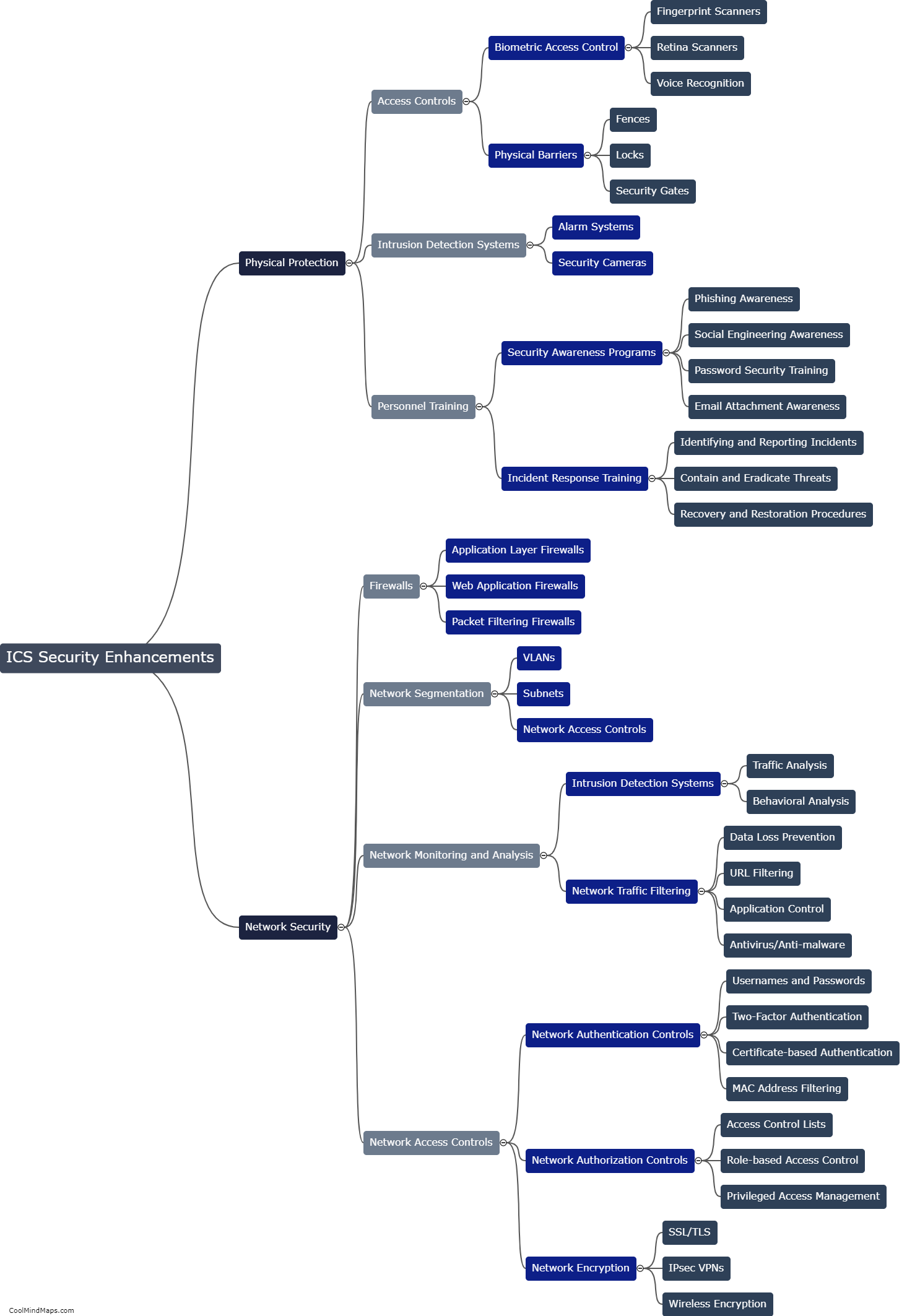
Existing ICS (Industrial Control Systems) security measures are designed to protect critical infrastructure such as power plants, water treatment facilities, and manufacturing plants from cyber threats. However, these security measures are not without vulnerabilities. One potential vulnerability is outdated or unpatched software and hardware, which can be exploited by attackers to gain access to the system. Additionally, weak or easily guessable passwords are often employed, leaving the system open to brute force attacks. Lack of proper network segmentation and access controls also pose a vulnerability, as an attacker who gains access to one part of the system may be able to move laterally and gain control over other critical components. Furthermore, the threat of insider attacks cannot be ignored, as disgruntled employees or contractors with privileged access can potentially misuse their privileges to disrupt or damage the system. Overall, addressing these vulnerabilities is crucial to strengthen the security of existing ICS systems.
This mind map was published on 28 January 2024 and has been viewed 96 times.