What are the risks associated with attacks on 5G IIoT core networks?
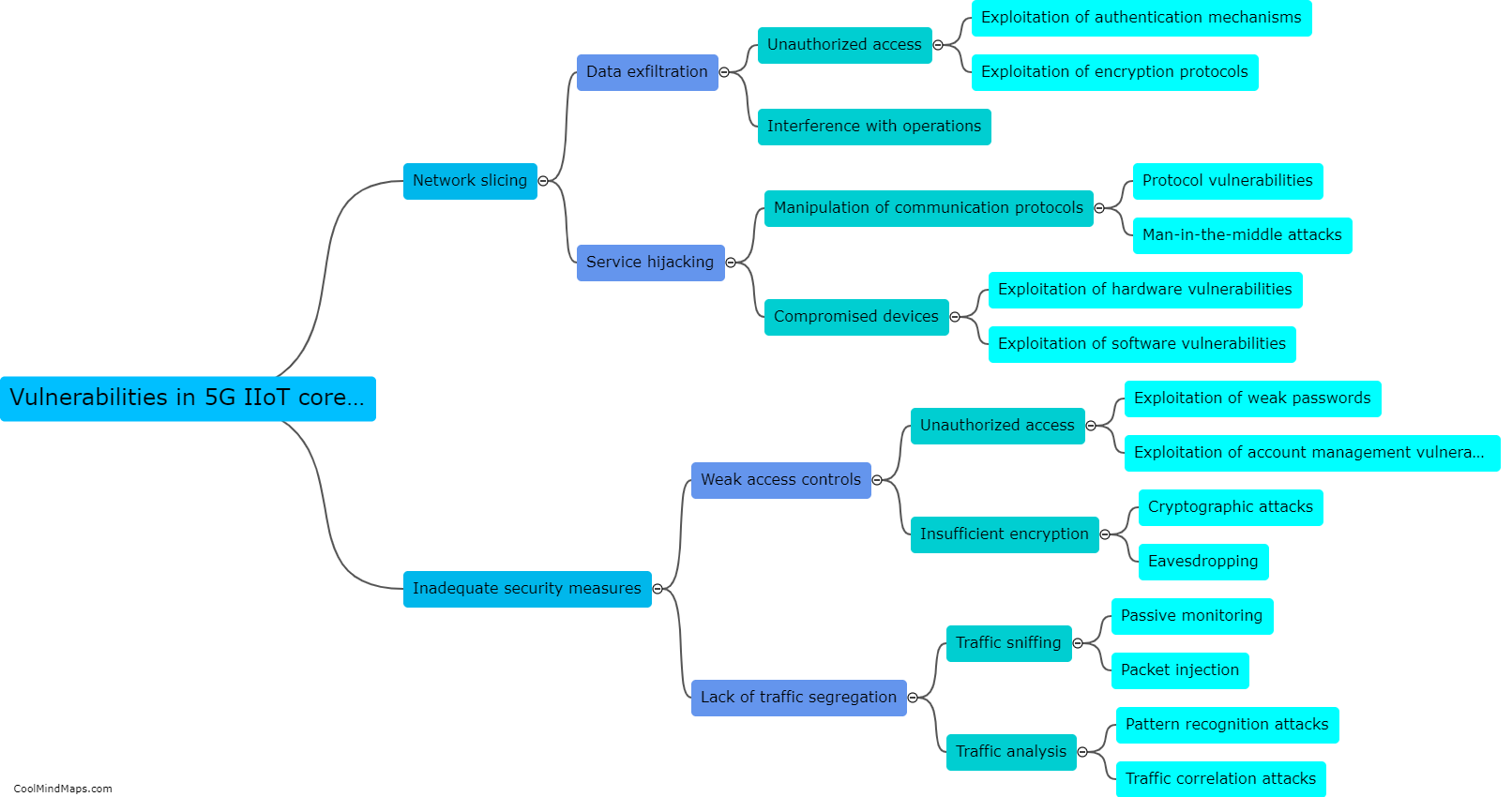
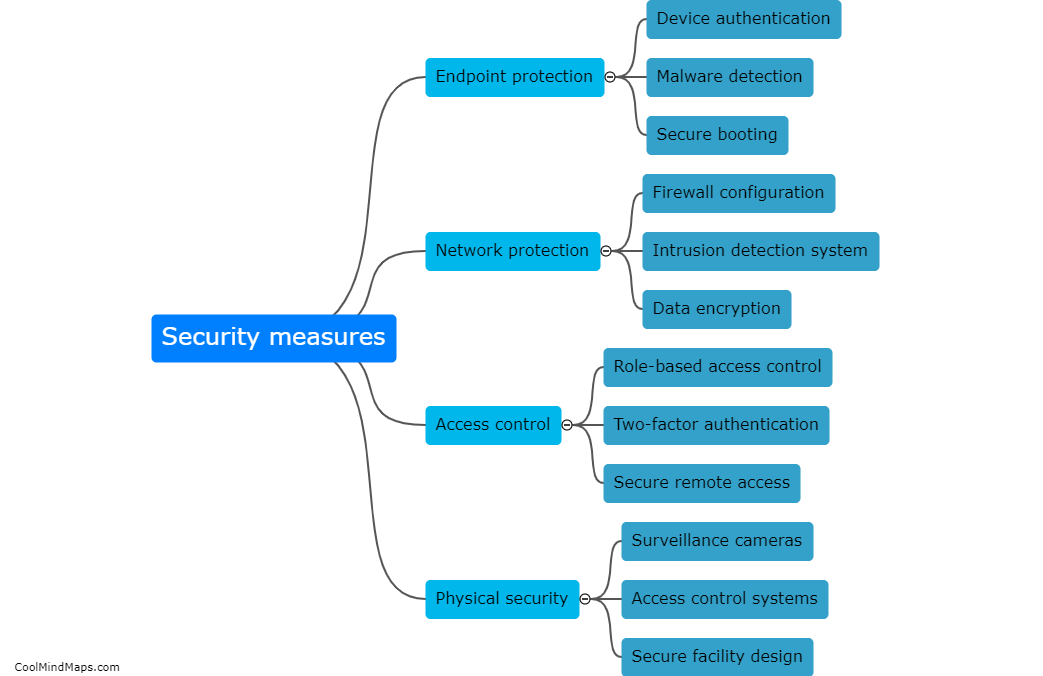
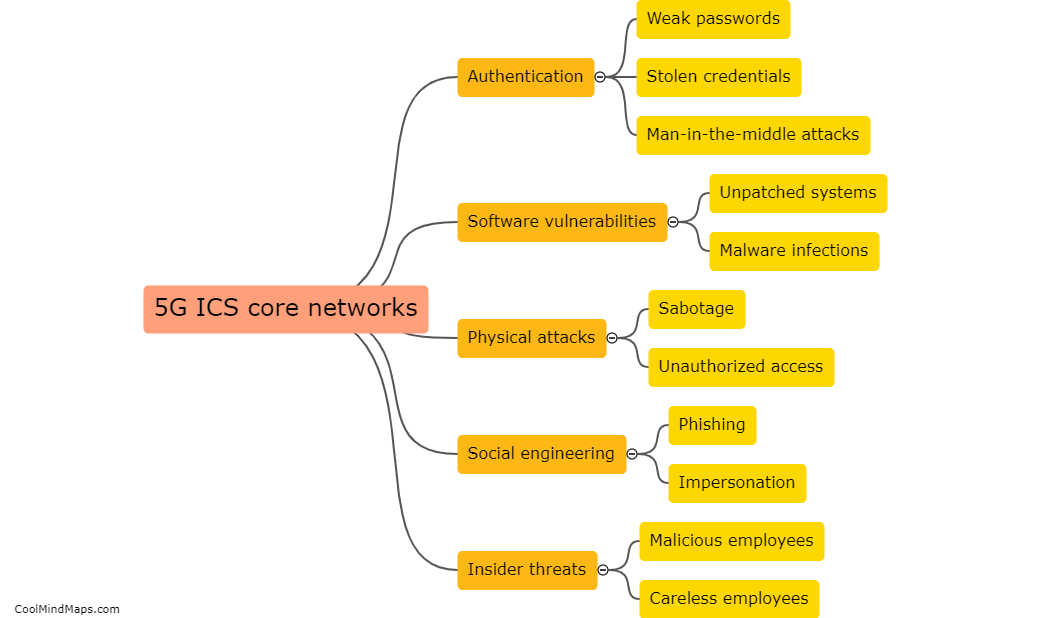
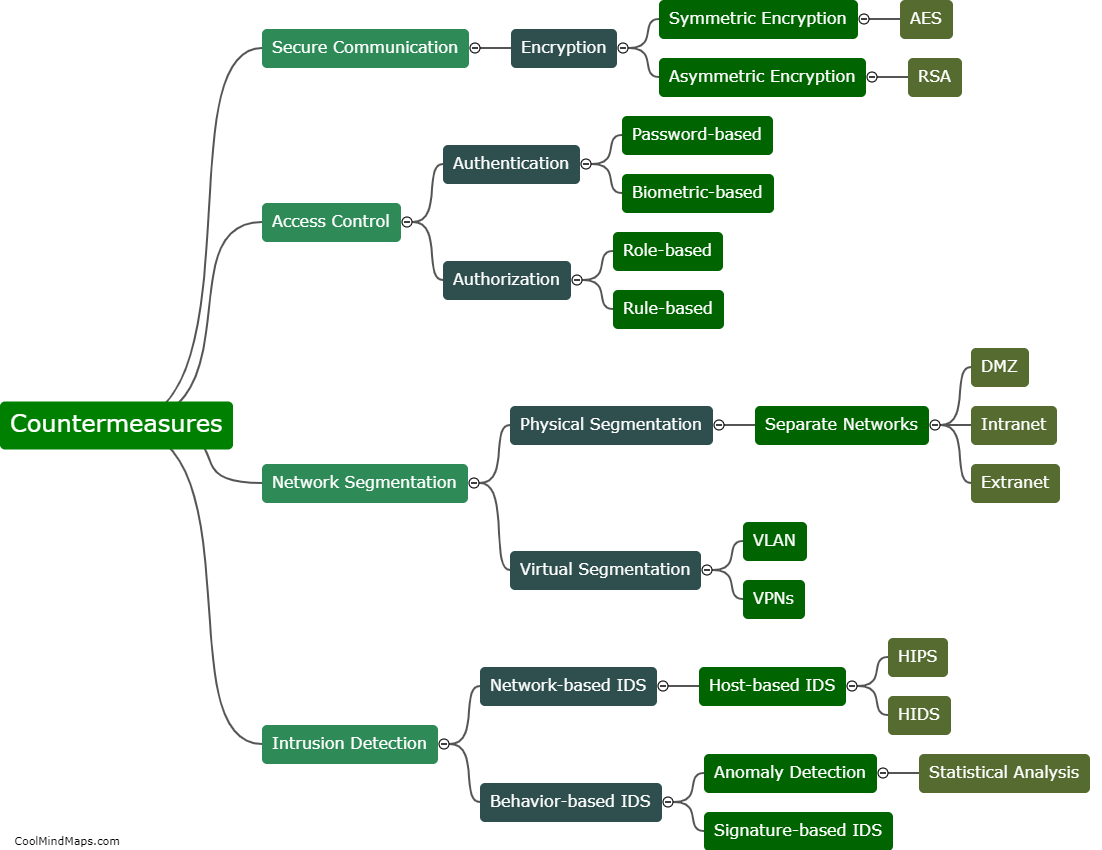
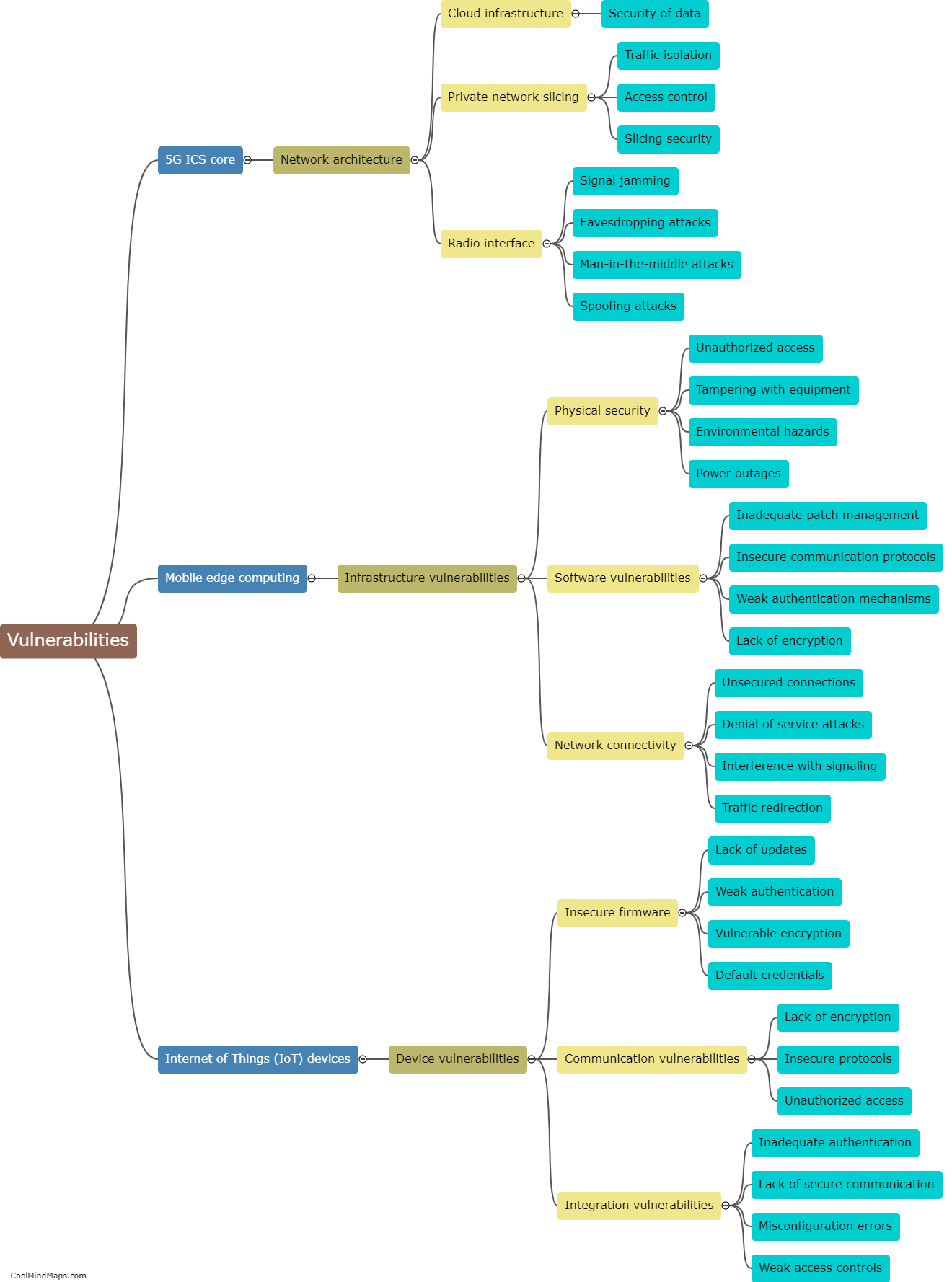
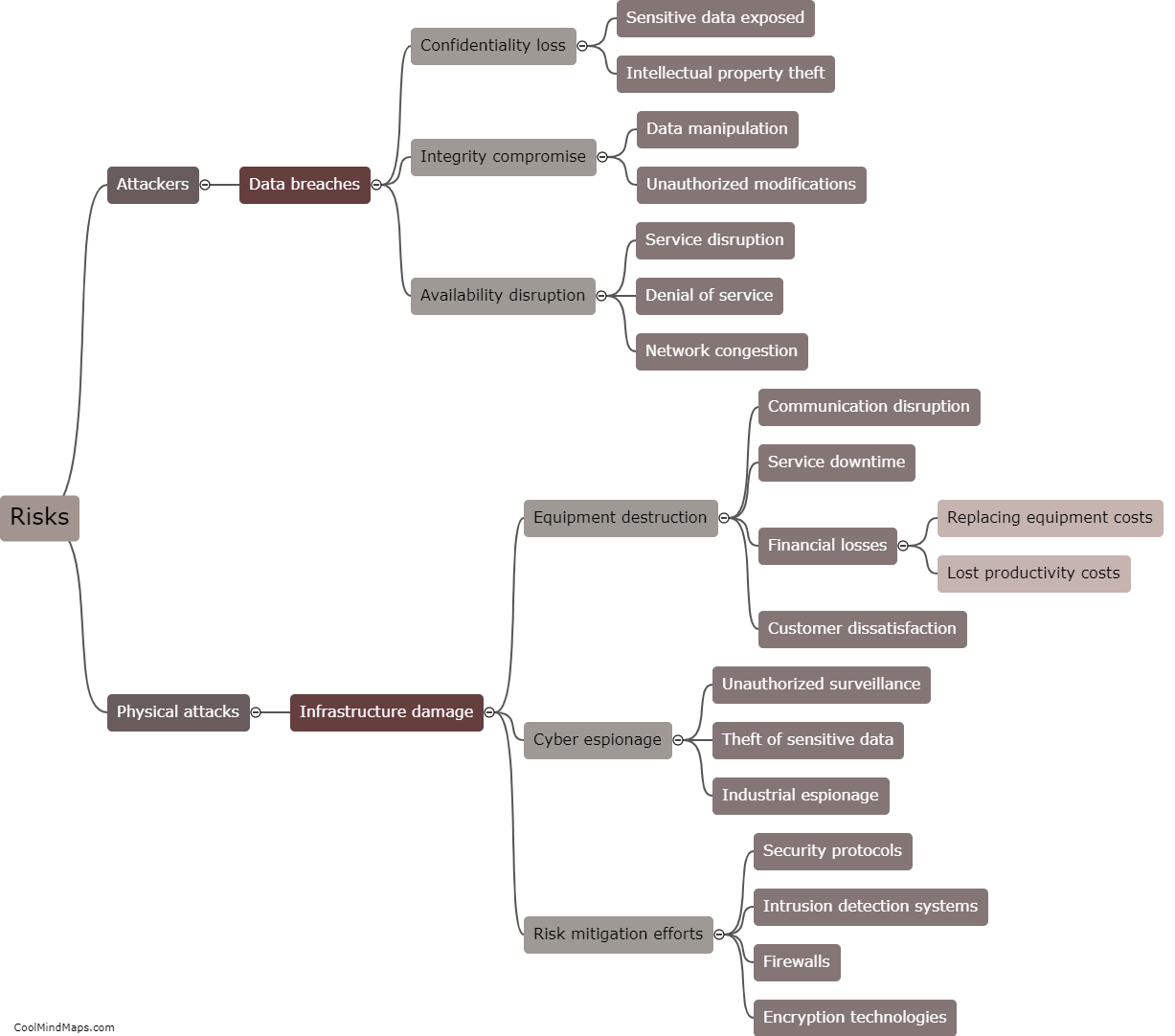
Attacks on 5G IIoT core networks pose significant risks to industries and critical infrastructure. One major concern is the potential for data breaches and unauthorized access to sensitive information, including trade secrets, intellectual property, and operational details. These attacks can disrupt the functioning of industrial processes, leading to production delays, financial losses, and even physical damage. Additionally, attackers can exploit vulnerabilities in the core network to launch large-scale denial-of-service attacks, impairing network availability and reliability. Furthermore, compromised IIoT devices can serve as entry points for broader cyber-attacks, allowing hackers to infiltrate and compromise other parts of the network ecosystem. Consequently, safeguarding the integrity and security of 5G IIoT core networks is of paramount importance to protect critical systems and prevent potential cascading effects on a global scale.
This mind map was published on 27 January 2024 and has been viewed 91 times.