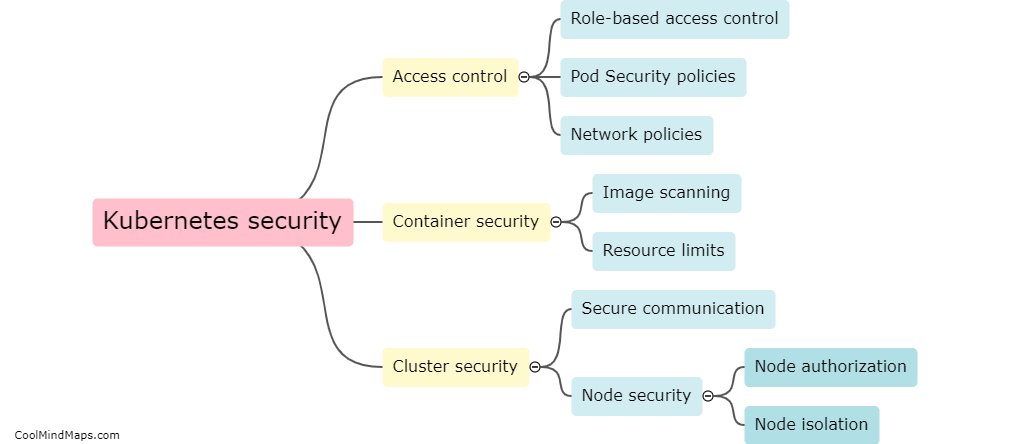
What are the best practices for Kubernetes security?
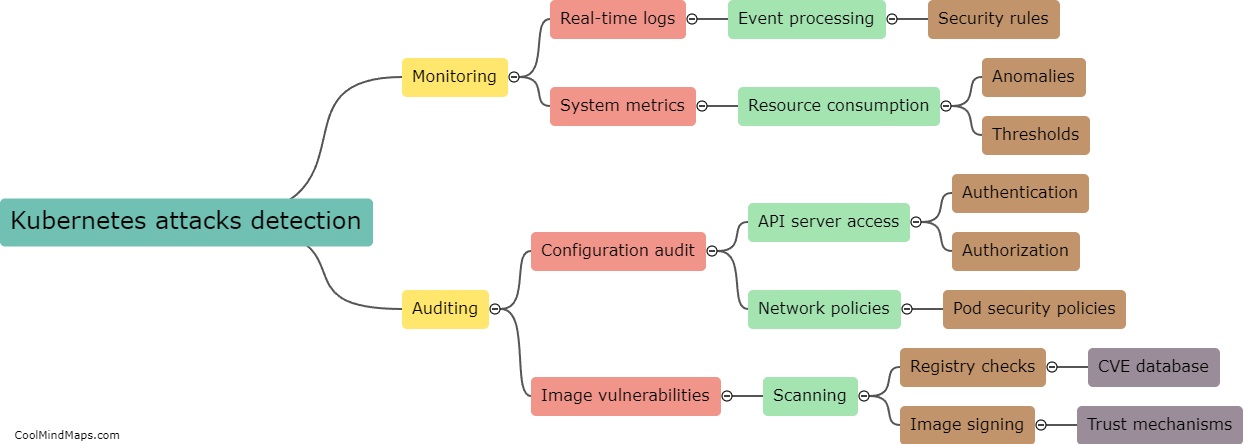
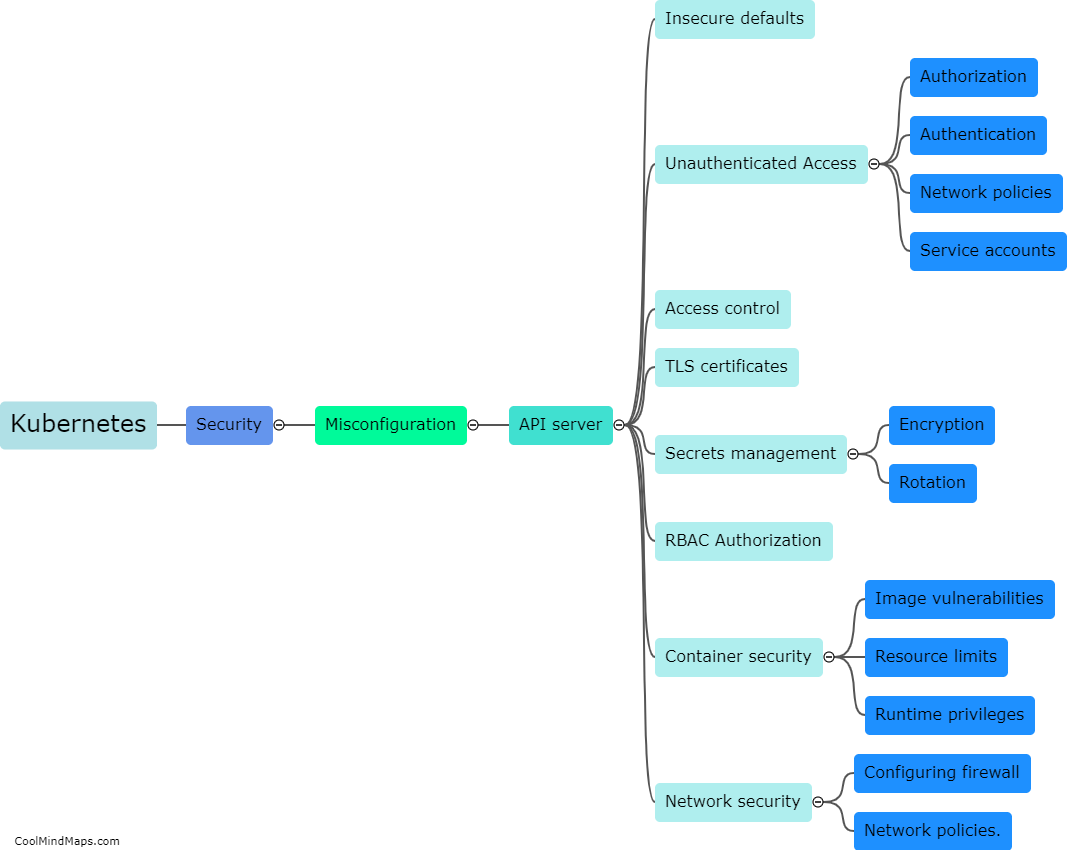
Kubernetes has become the go-to platform for managing containerized applications at scale, but as with any powerful technology, it also comes with a range of security challenges. Best practices for Kubernetes security include securing the network by limiting traffic between pods, monitoring and controlling access to cluster APIs, implementing pod security policies to prevent containers from running as root, and using RBAC policies to manage user access. Additionally, it is important to regularly audit and update the system to ensure that vulnerabilities are detected and addressed promptly. By following these practices, organizations can ensure that their Kubernetes environment remains secure and their containerized applications are protected against potential threats.
This mind map was published on 26 June 2023 and has been viewed 93 times.