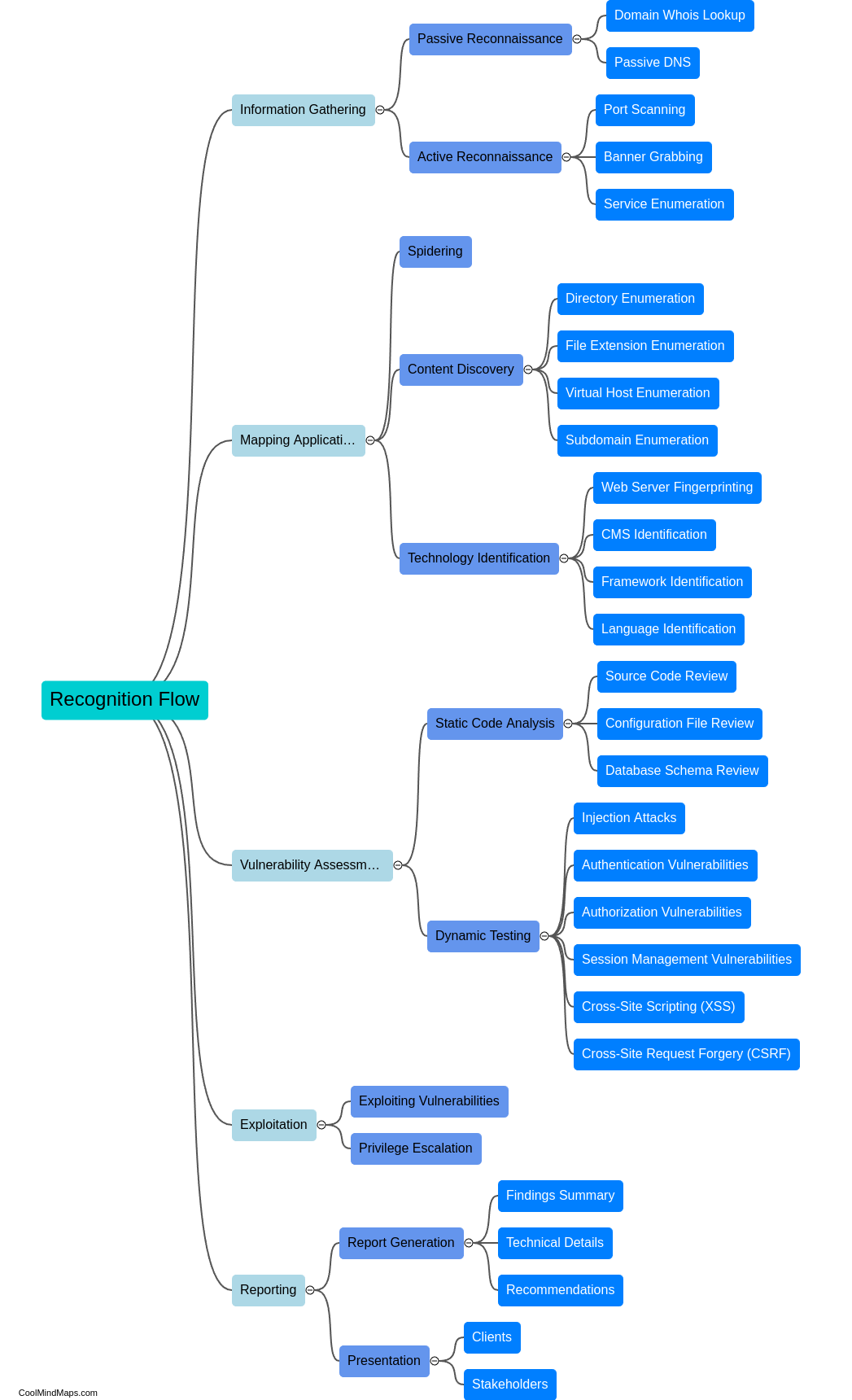
What is a recognition flow for pentesting in web applications?
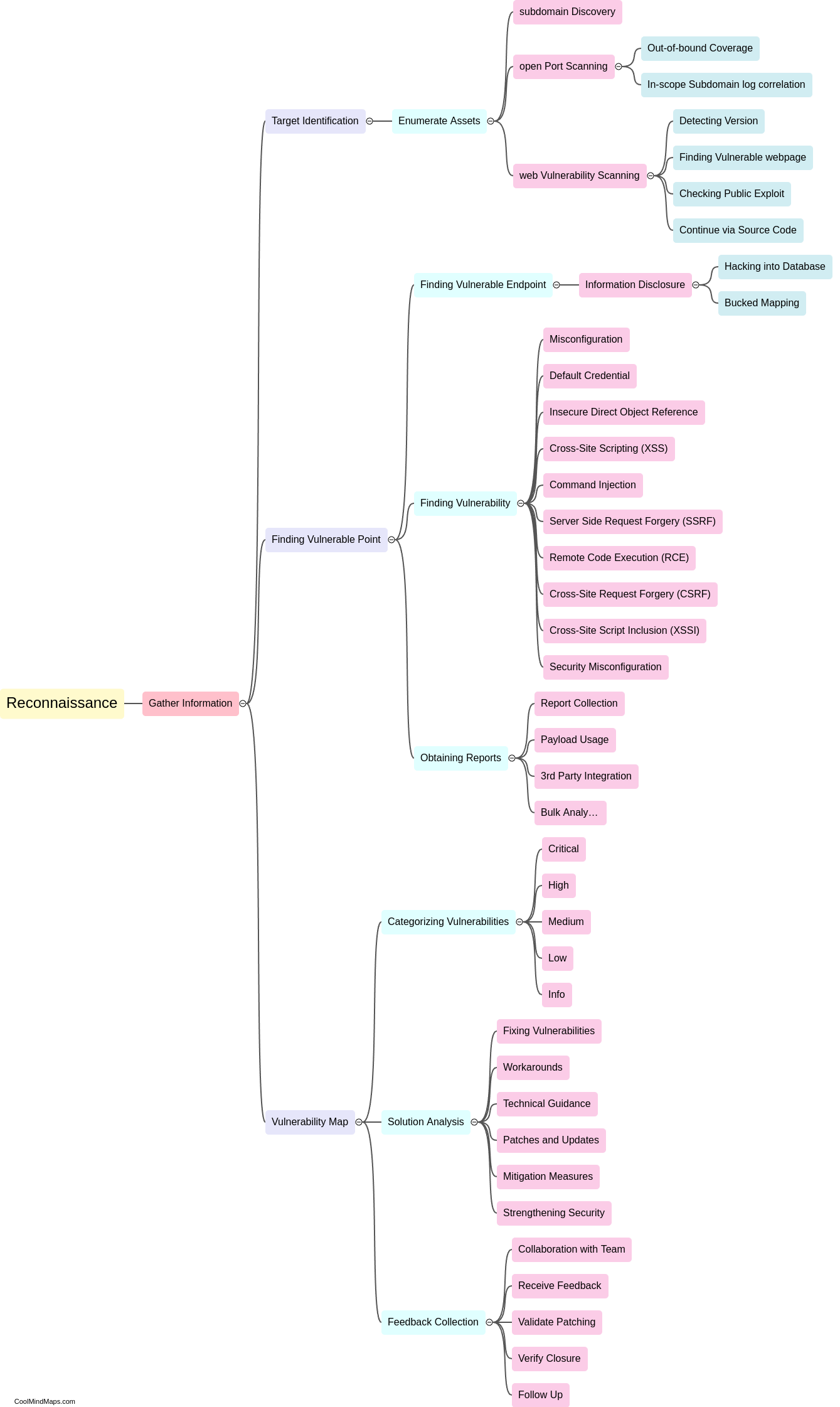
A recognition flow, also known as a recon flow, for pentesting in web applications refers to the systematic process of gathering information and identifying potential vulnerabilities in a target website or web application. This pre-engagement phase commonly involves various techniques like passive information gathering, open-source intelligence (OSINT) collection, network scanning, port scanning, fingerprinting, and web application profiling. The objective is to gain a comprehensive understanding of the target's architecture, technologies in use, potential attack vectors, and any other relevant information that can aid in the subsequent penetration testing process. A well-executed recognition flow enables pentesters to develop effective strategies and methodologies for identifying vulnerabilities and enhancing the security posture of the targeted web application.
This mind map was published on 17 December 2023 and has been viewed 97 times.