How do cyber warfare models work?
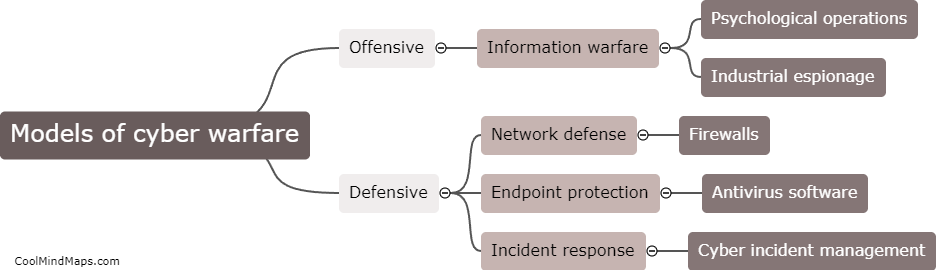
Cyber warfare models operate by utilizing various strategies, tactics, and techniques to carry out attacks in the digital realm. These models typically consist of different stages or elements that are executed sequentially to achieve specific objectives. The first stage involves intelligence gathering, where cyber attackers collect information about their target's vulnerabilities, assets, and infrastructure. This is followed by planning and reconnaissance, where attackers analyze the gathered information to identify potential entry points and select appropriate attack vectors. The next stage is the execution, where the actual attack is launched, using methods like malware deployment, social engineering, or exploiting software vulnerabilities. The attackers then employ techniques to maintain their presence, such as using backdoors or command-and-control servers. Throughout the process, attackers continuously adapt and refine their methods based on the target's defenses and evolving technologies. Ultimately, the goal of cyber warfare models is to disrupt or destroy critical infrastructure, steal sensitive data, or gain control over systems for strategic advantage.

This mind map was published on 9 October 2023 and has been viewed 99 times.