How are vulnerabilities in ICS exploited by hackers?
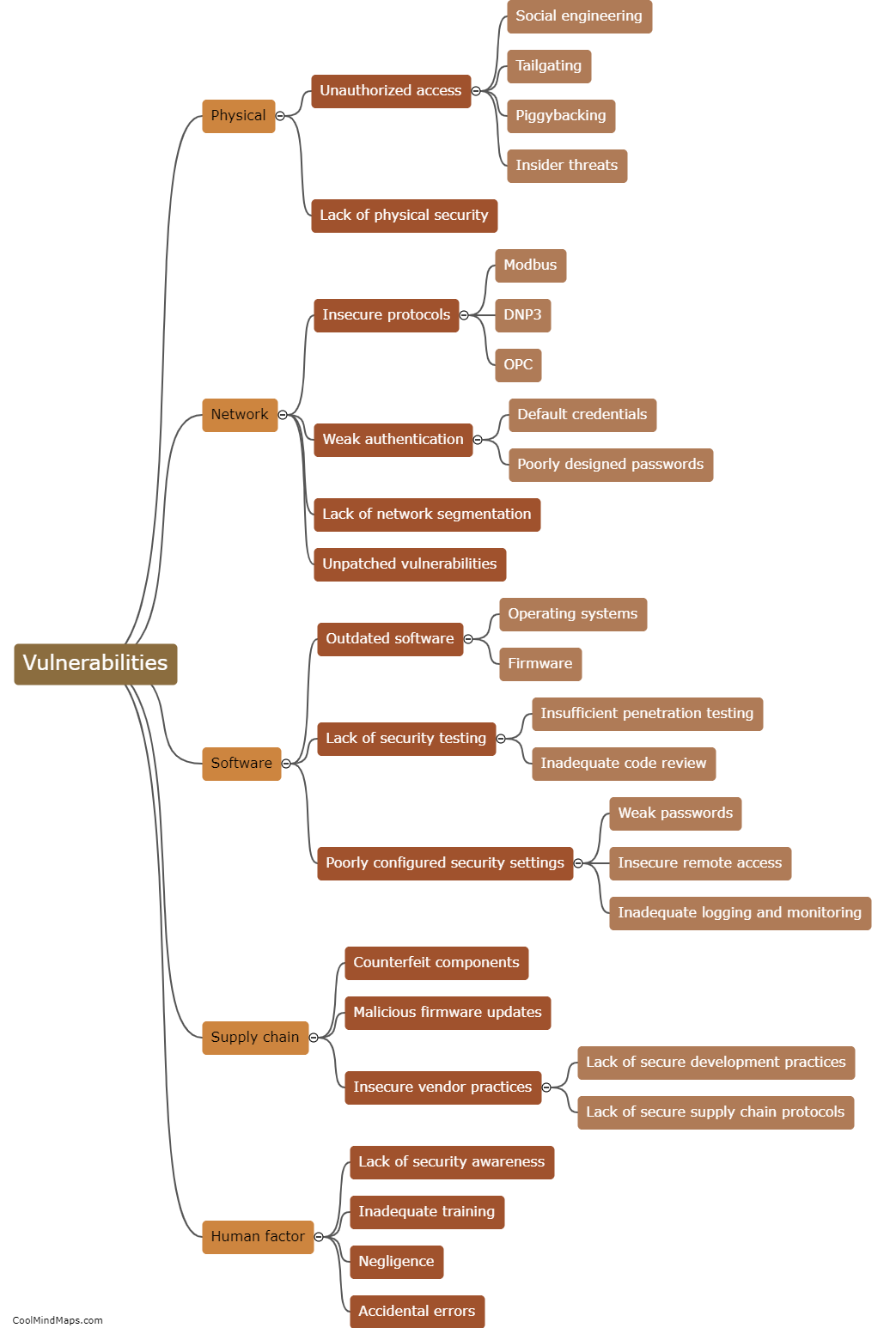
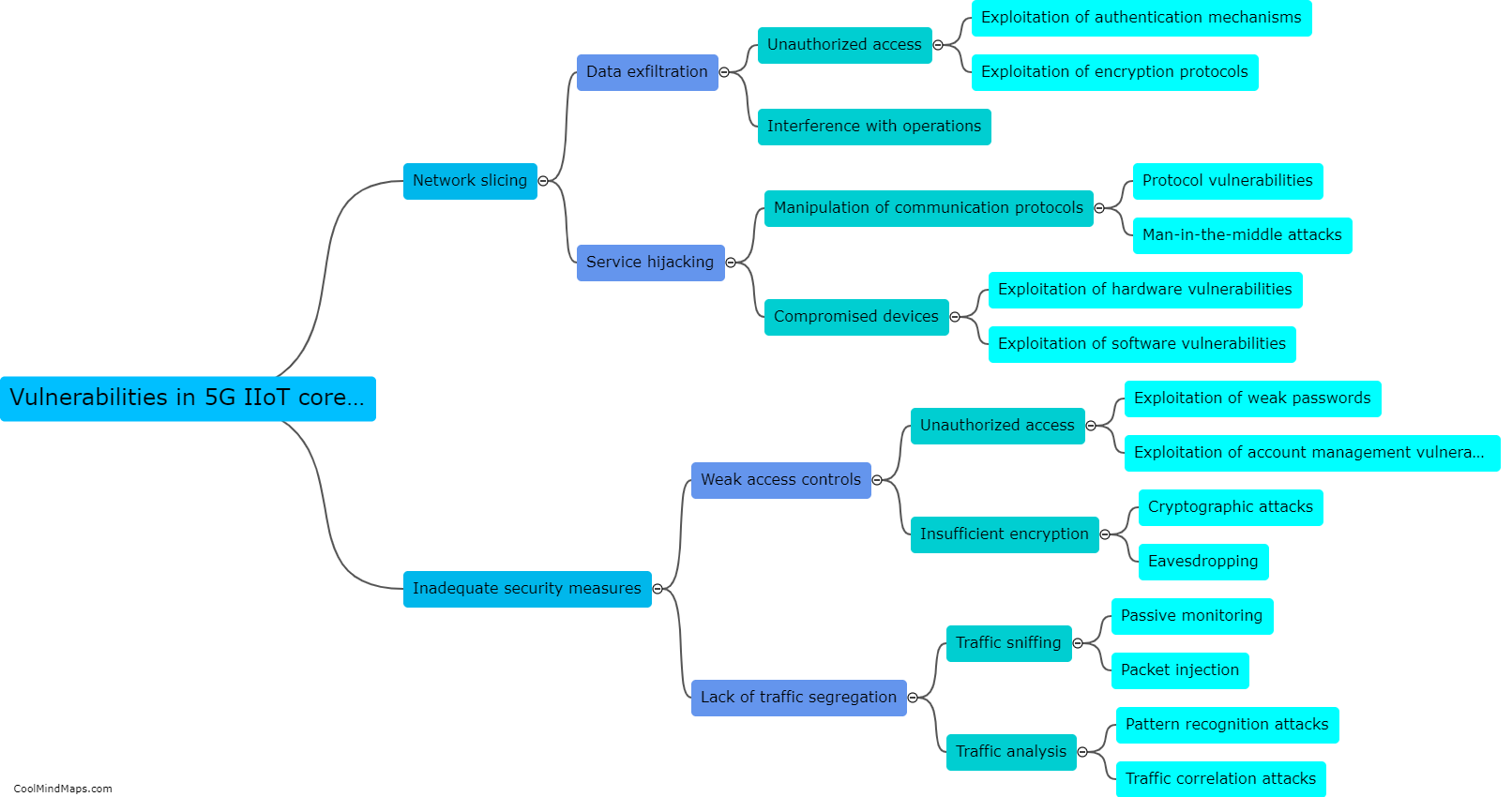
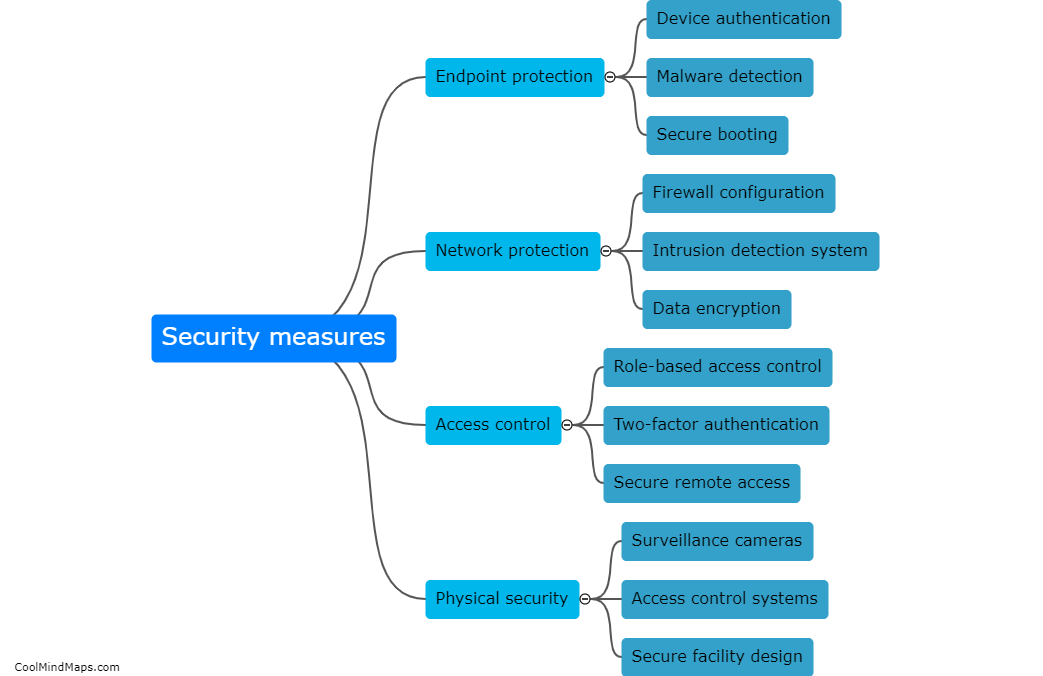
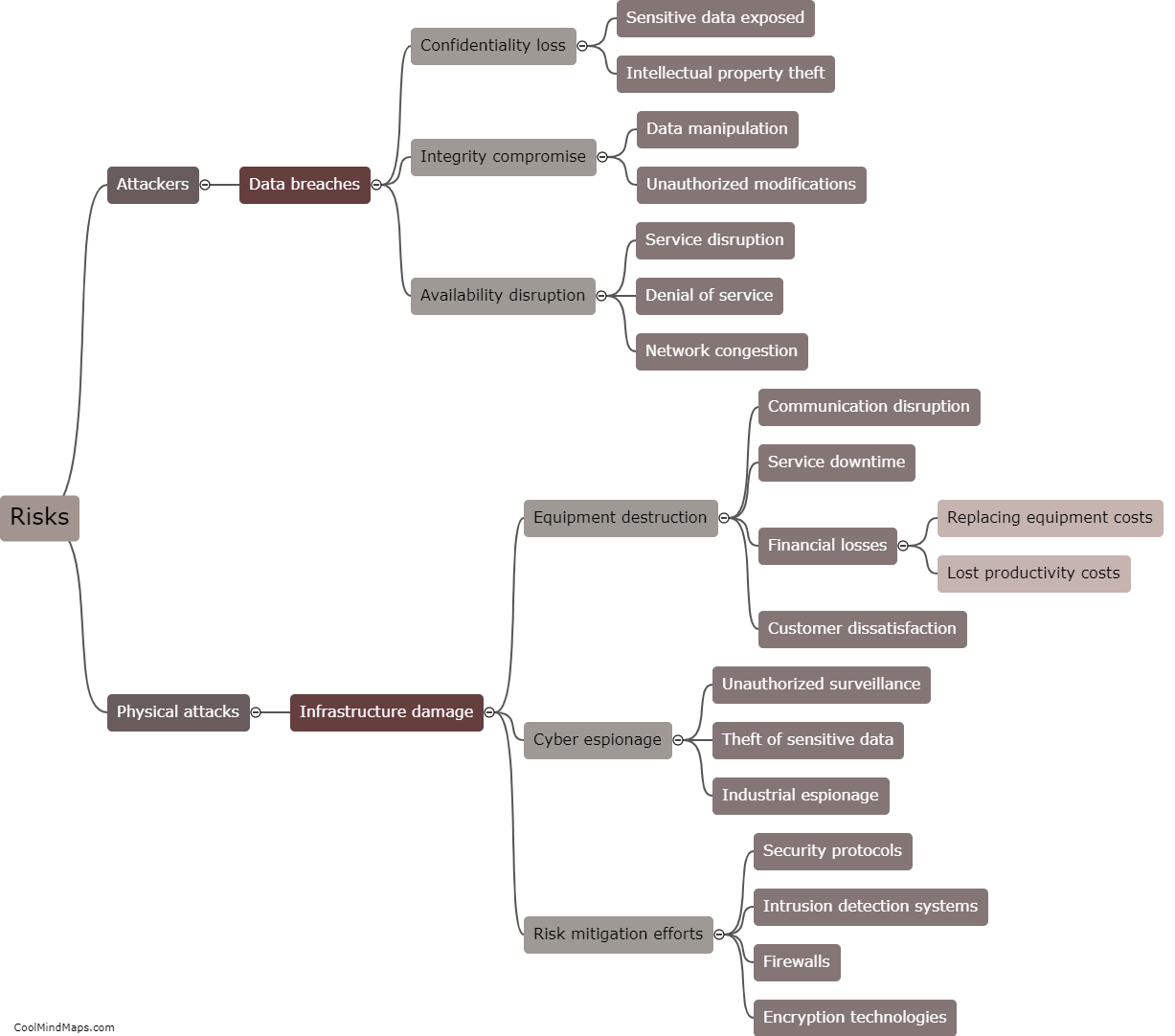
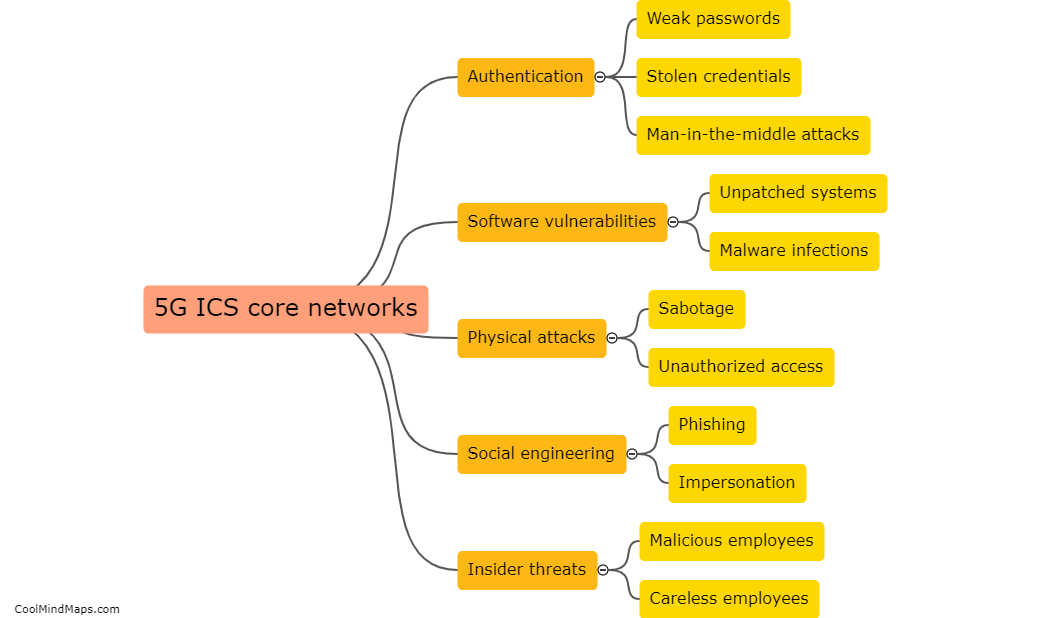
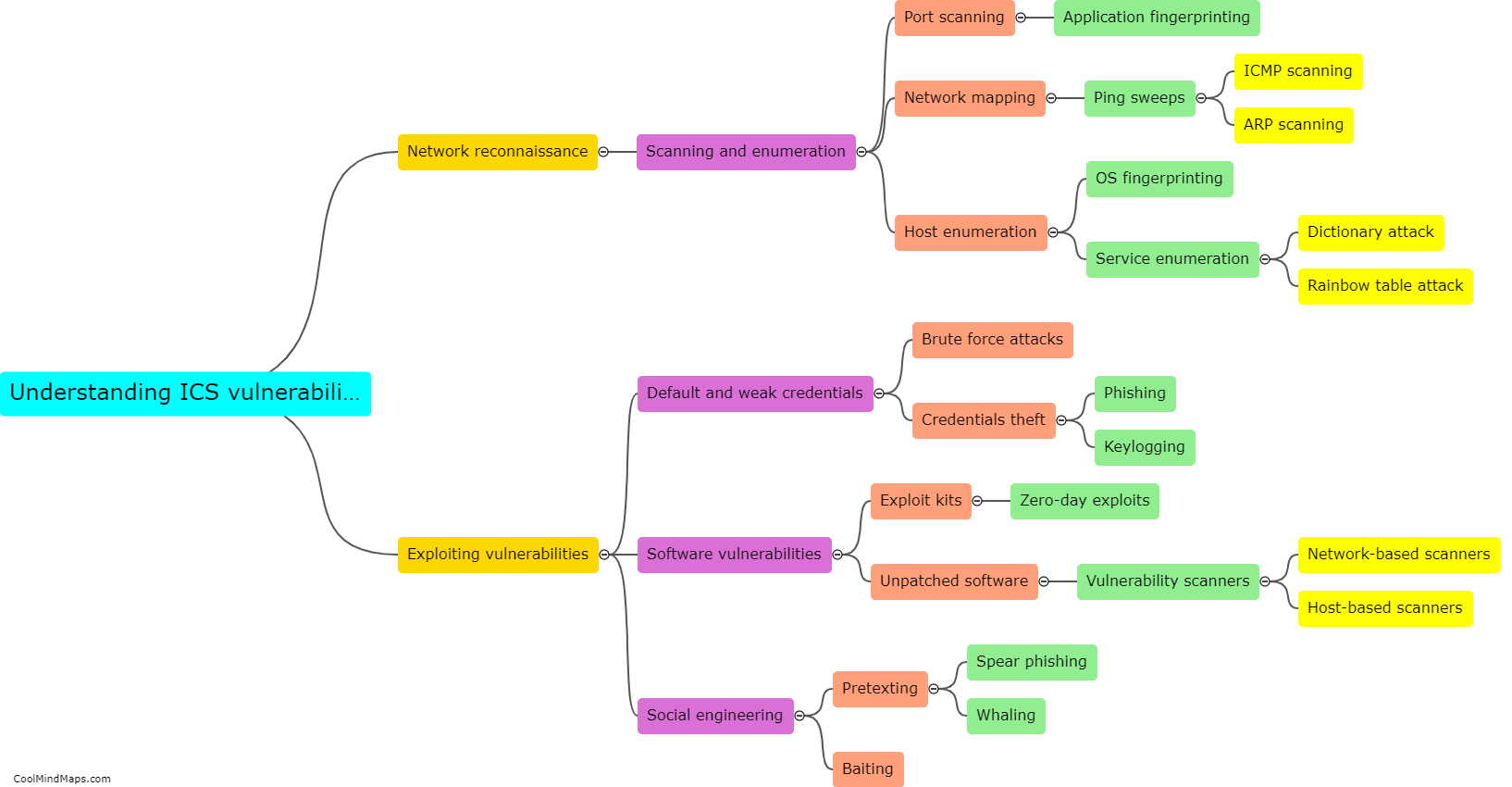
Vulnerabilities in Industrial Control Systems (ICS) are exploited by hackers using various techniques to gain unauthorized access and manipulate critical infrastructure. One common method is through the use of malware, which can be delivered via phishing emails or infected USB drives. Once the malware gains a foothold within the ICS network, it can exploit vulnerabilities in software or hardware components to carry out destructive or disruptive activities. Another approach is by targeting weak passwords or default credentials used to protect ICS devices or network access. Hackers may also exploit unpatched or outdated software, taking advantage of known vulnerabilities for which security updates have not been applied. These exploits can grant hackers control over ICS devices, allowing them to manipulate systems, disrupt operations, or cause physical damage. Ultimately, the exploitation of vulnerabilities in ICS can have severe consequences, including compromised safety, economic losses, and potential threats to national security.
This mind map was published on 27 January 2024 and has been viewed 120 times.