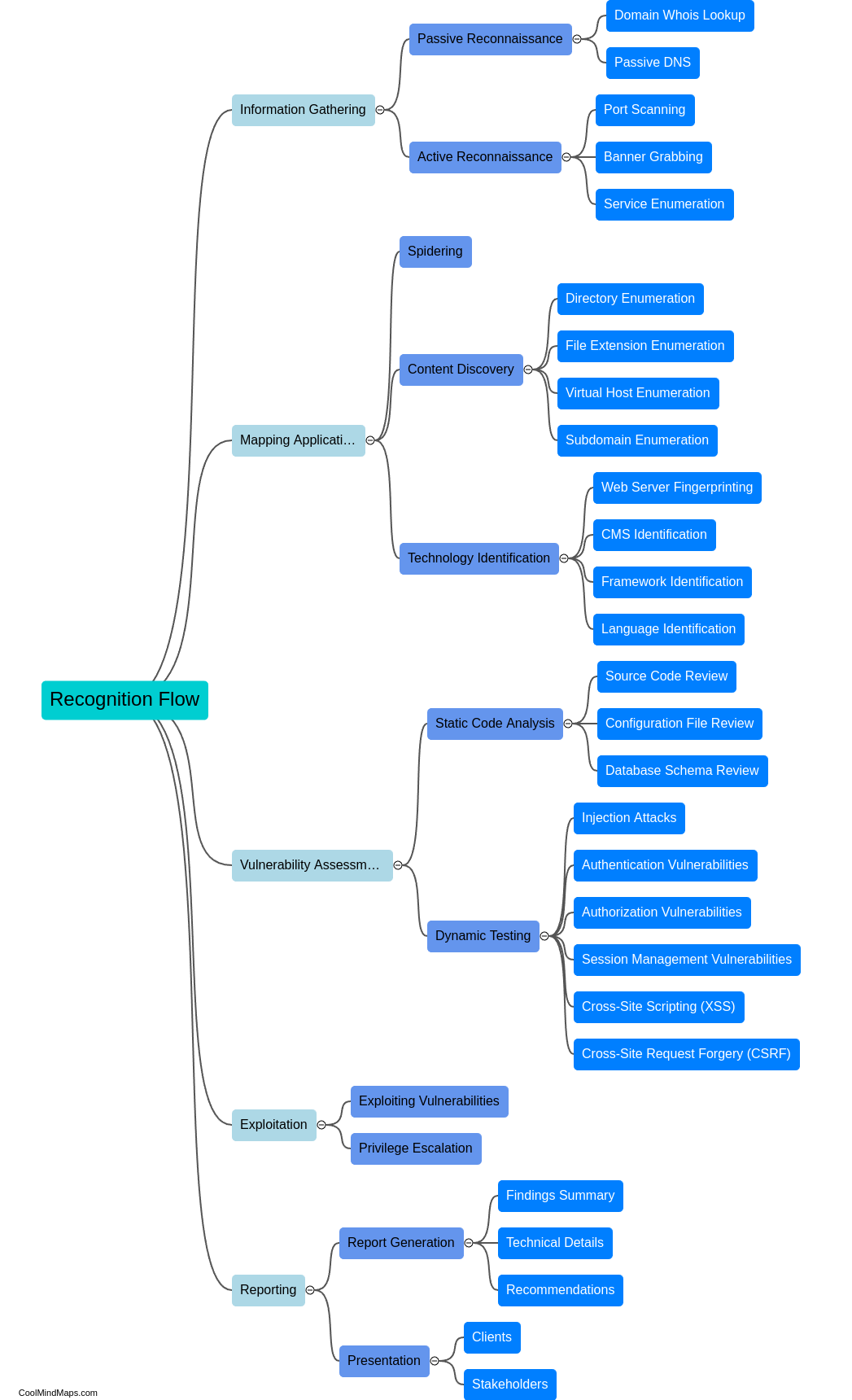
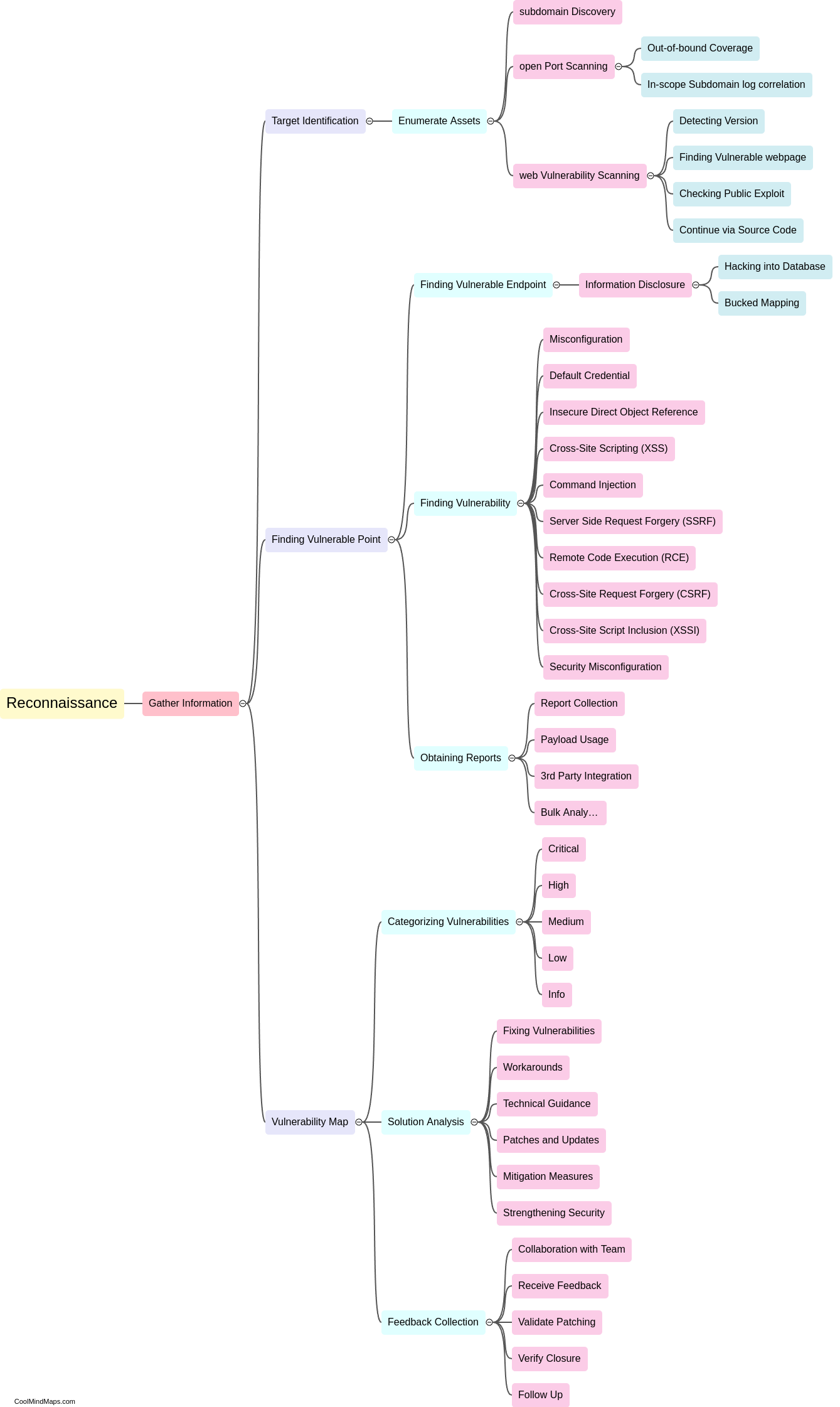
How to create a reconnaissance flow for bug bounty?
Creating a reconnaissance flow for bug bounty is crucial in order to maximize efficiency and effectiveness in finding vulnerabilities. To start, it is essential to gather as much information as possible about the target, such as its IP range, domain names, and associated subdomains. This can be done using tools like Nmap, Shodan, and DNS enumeration. The next step is to perform port scanning and service identification to uncover potential entry points. Following this, conducting web assessment using tools like Burp Suite and OWASP ZAP helps identify common web vulnerabilities. It is also essential to explore the target's APIs for potential security flaws. Finally, tracking and documenting all findings is crucial to create a comprehensive report for bug bounty submission.
This mind map was published on 16 December 2023 and has been viewed 89 times.