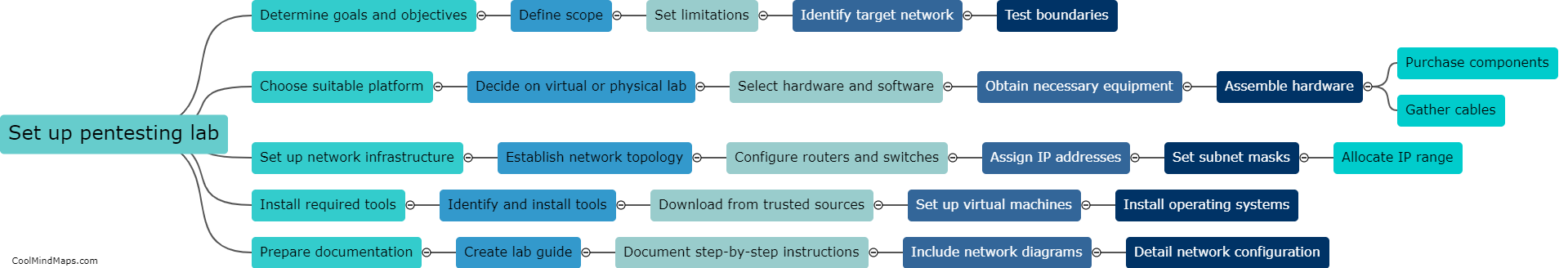
How to set up a network pentesting lab?
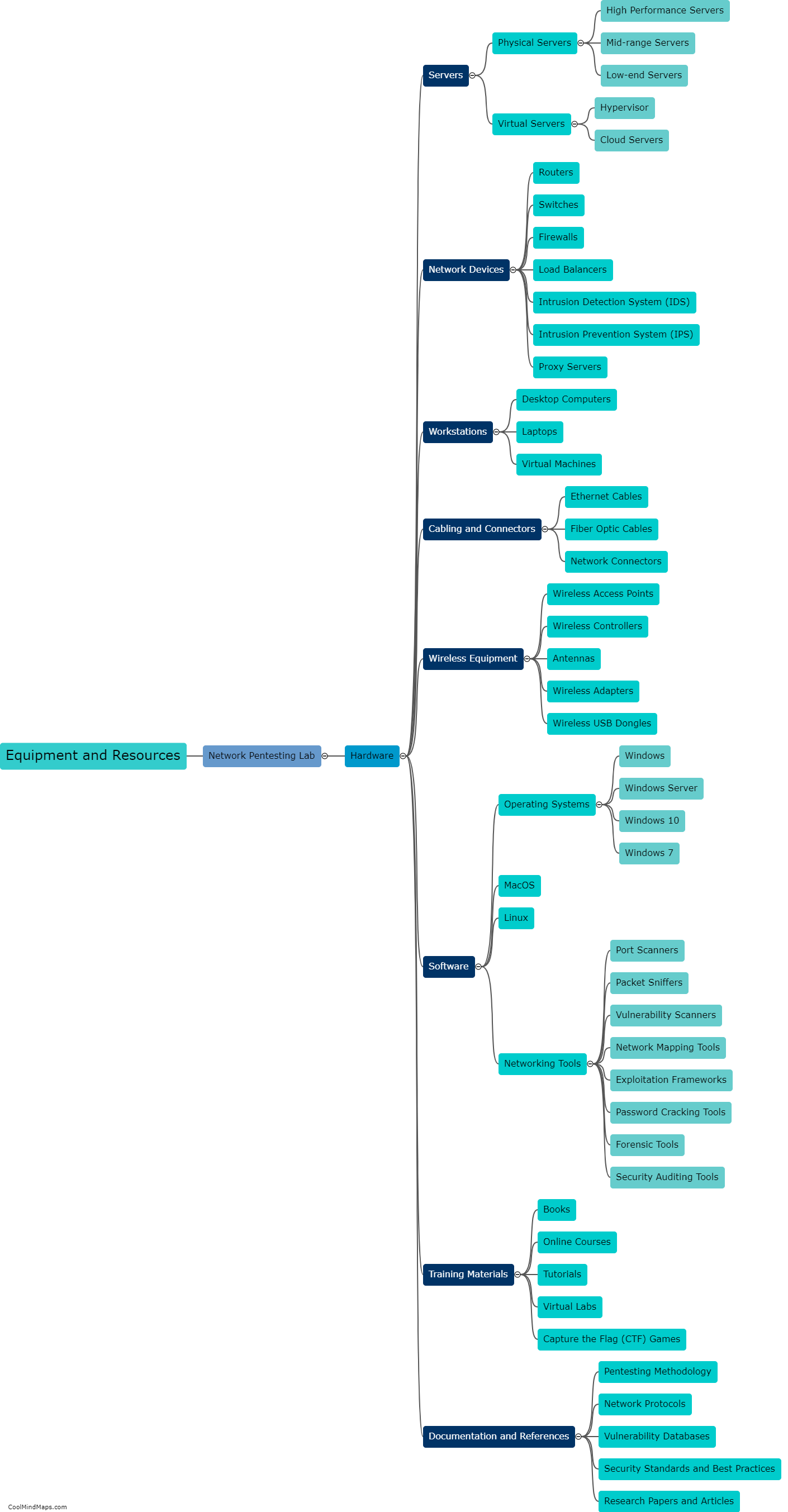
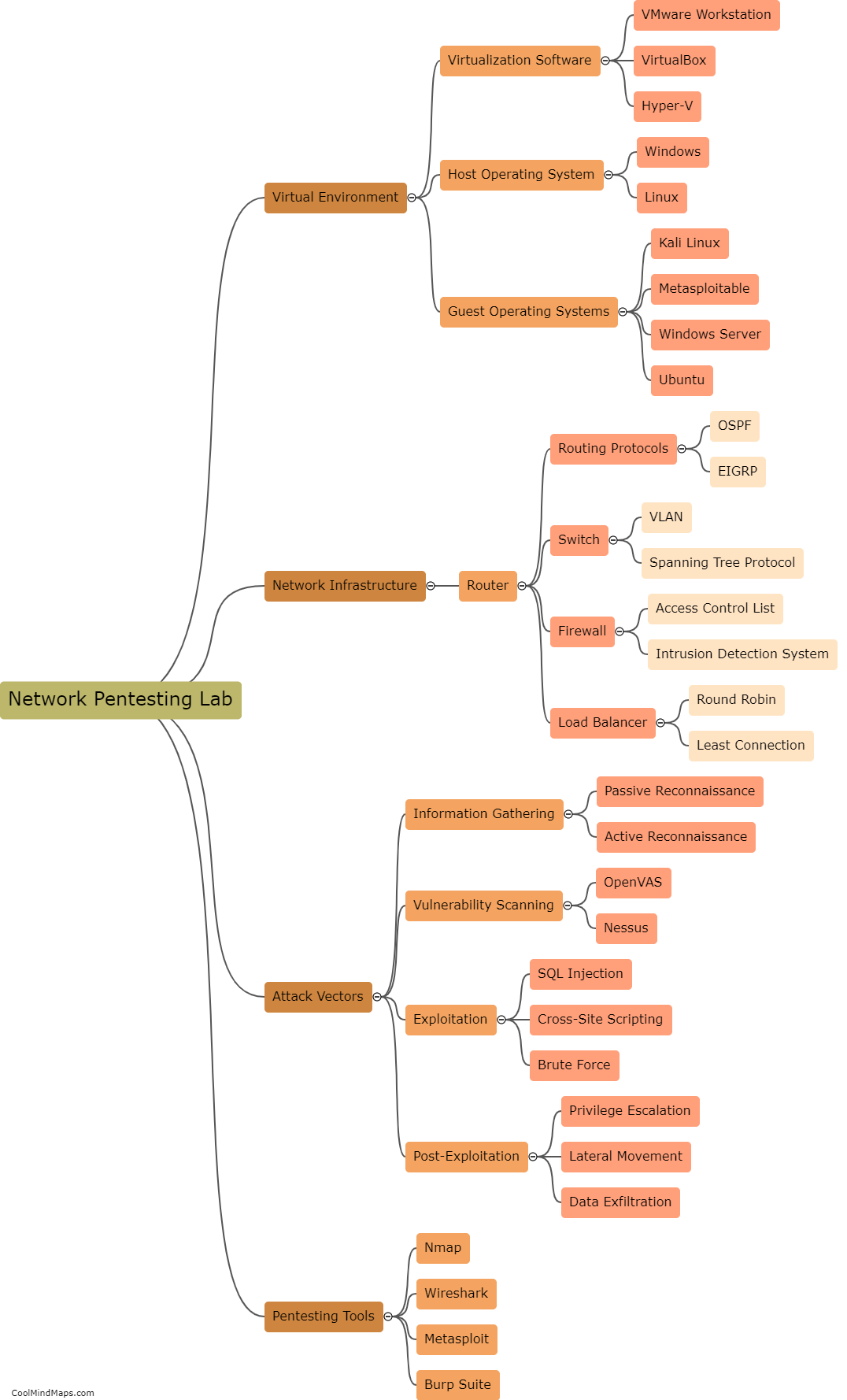
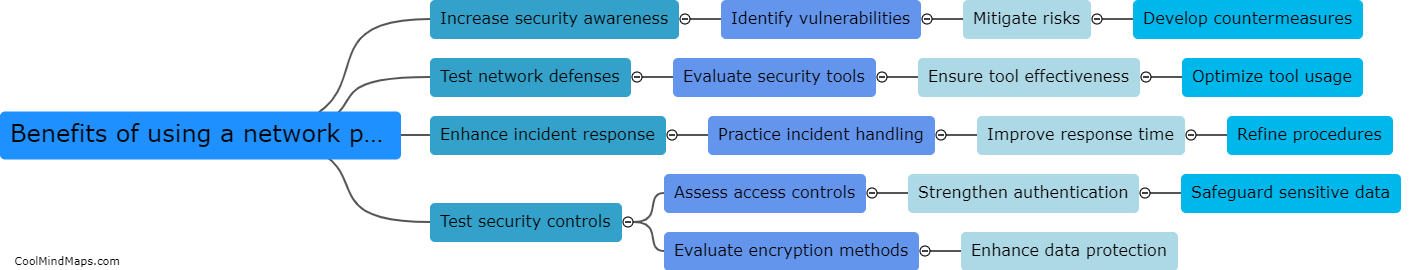
Setting up a network pentesting lab is essential for individuals seeking to enhance their cybersecurity skills. The first step is to acquire the necessary hardware, such as a dedicated machine or virtual machines and network switches. Virtualization software, like Oracle's VirtualBox or VMWare, enables the creation of multiple virtual machines with different operating systems. Next, installing and configuring tools like Kali Linux is crucial, as it provides a comprehensive suite of penetration testing tools. Creating a separate network segment, either physical or virtual, is important to isolate the lab from the main network. This can be done using VLANs or separate physical switches. Lastly, setting up target machines that simulate real-life vulnerabilities is crucial for effective practice. This involves intentionally configuring weak security settings or vulnerabilities to be exploited during the testing process. Overall, creating a network pentesting lab requires careful planning, proper hardware and software setup, and the establishment of realistic target machines.
This mind map was published on 21 September 2023 and has been viewed 115 times.