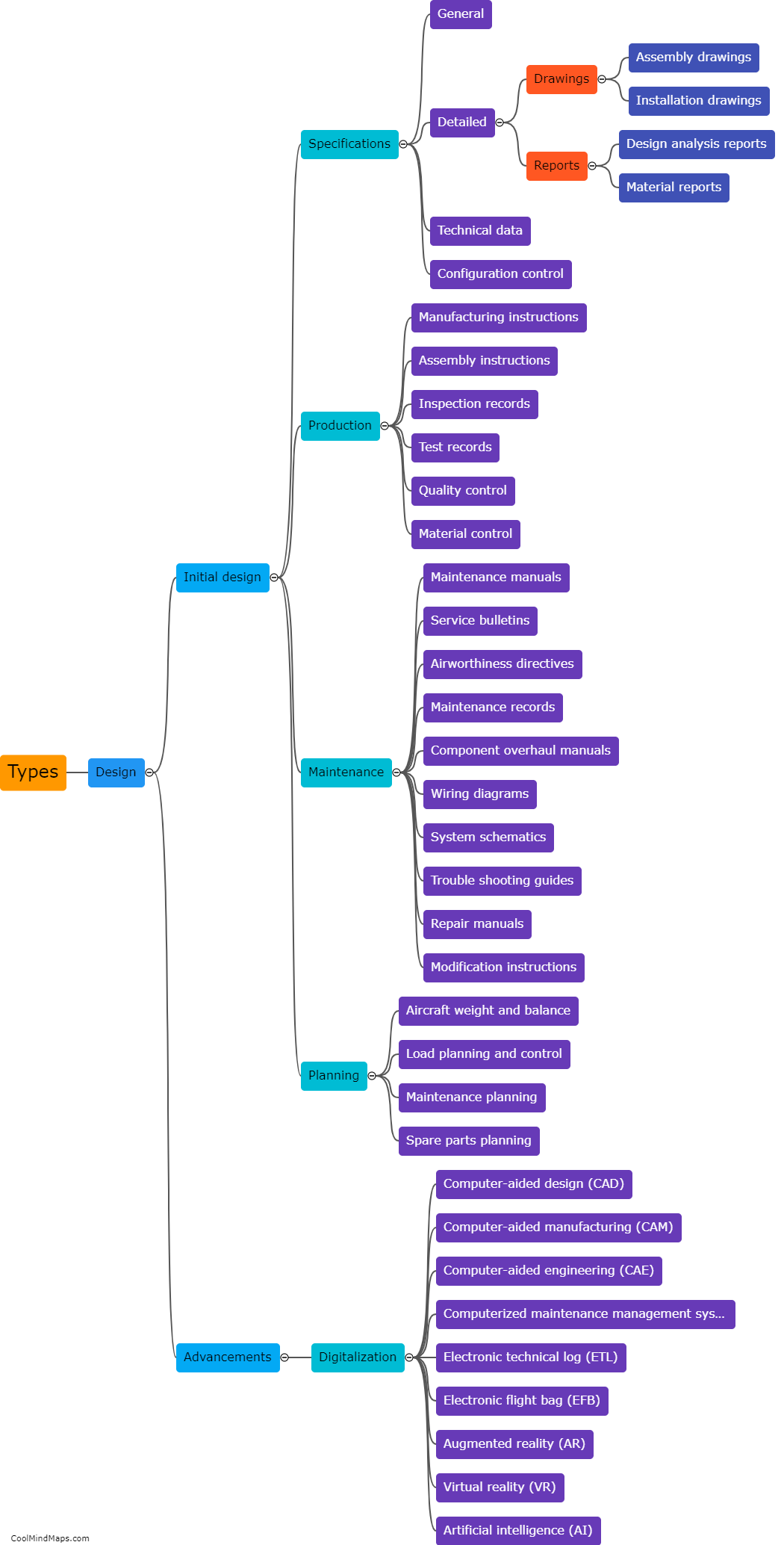
What are the common vulnerabilities in ICS policies and procedures?
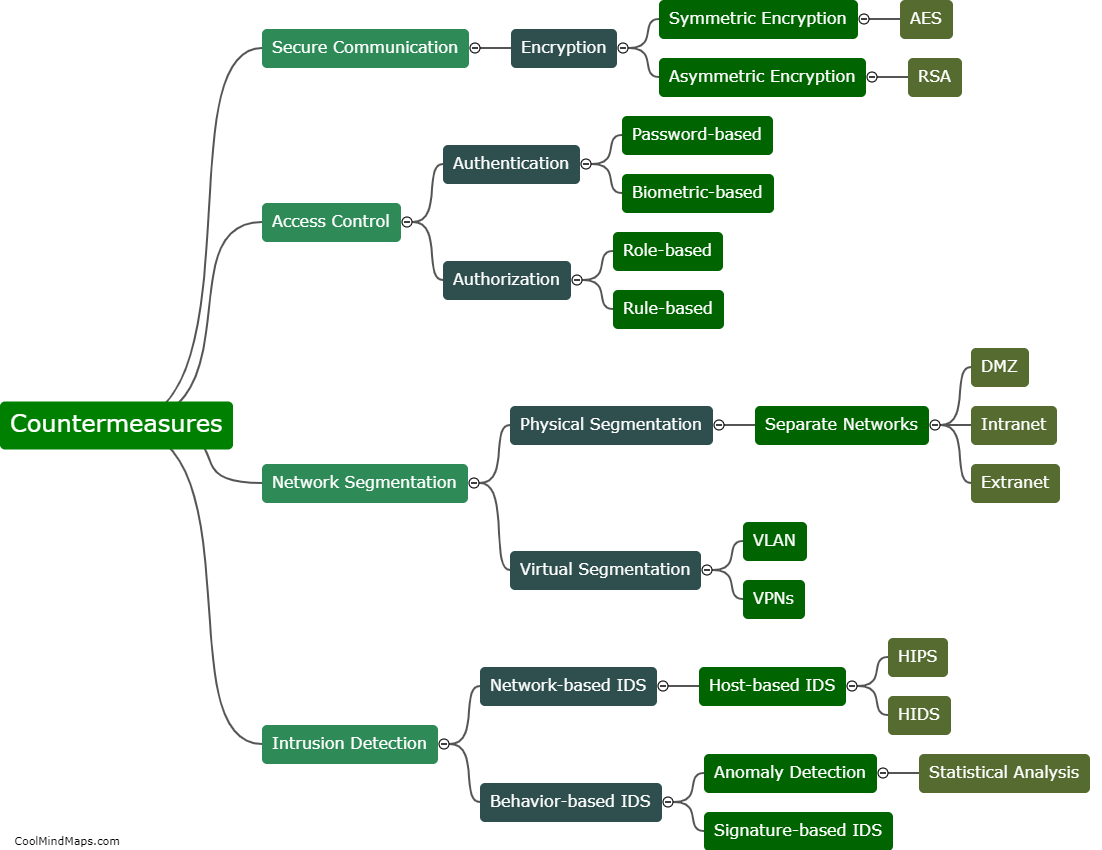
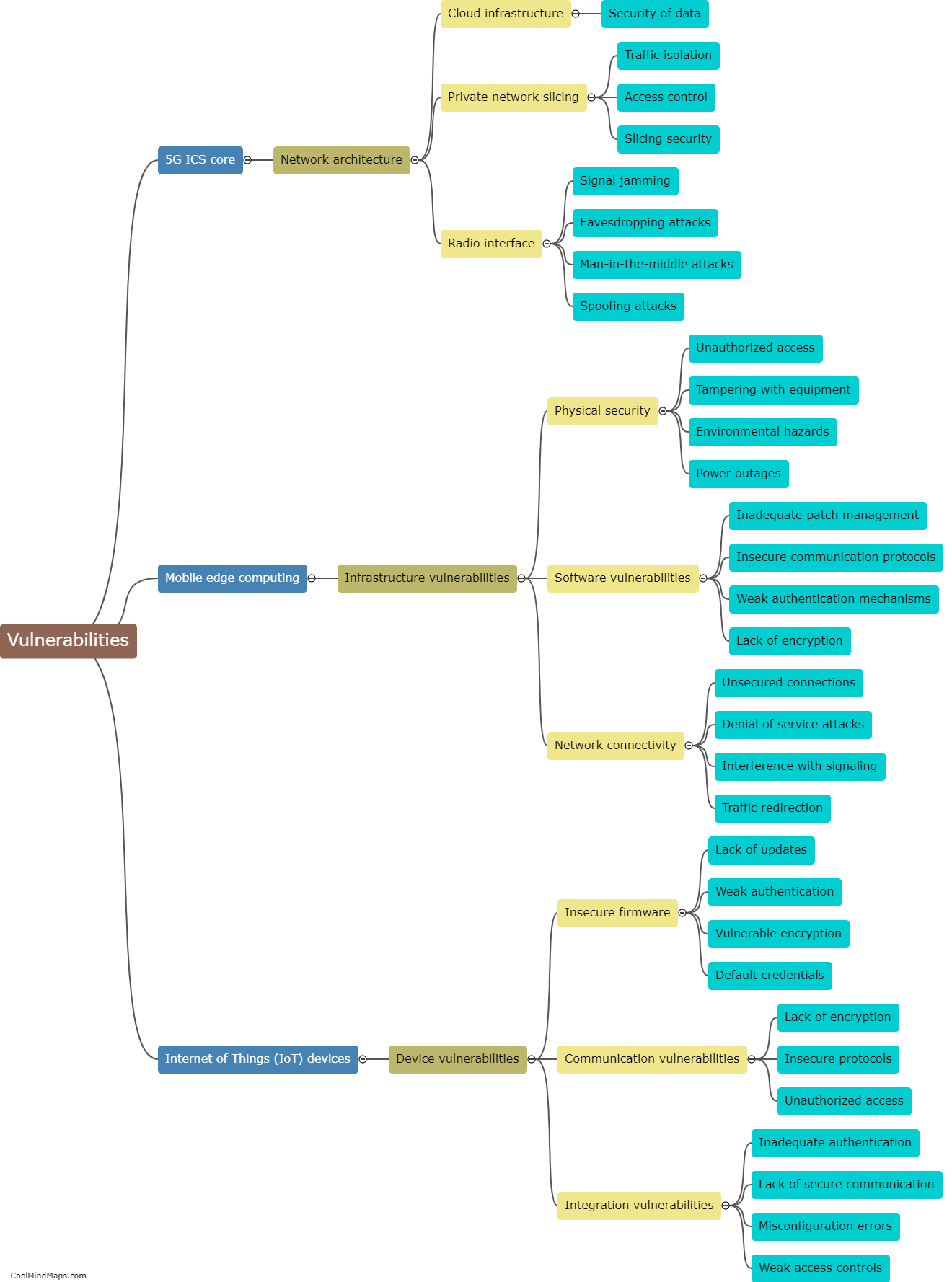
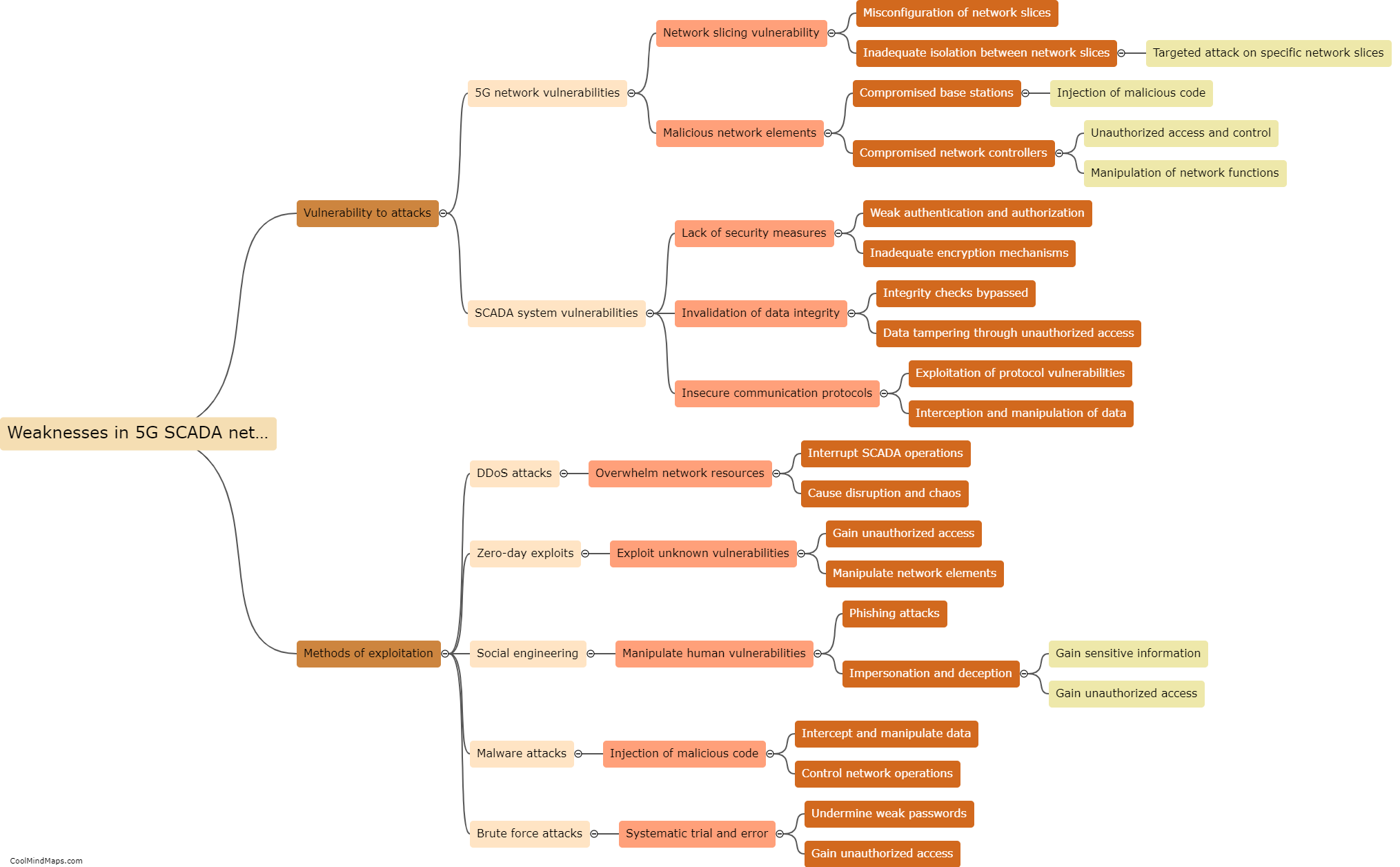
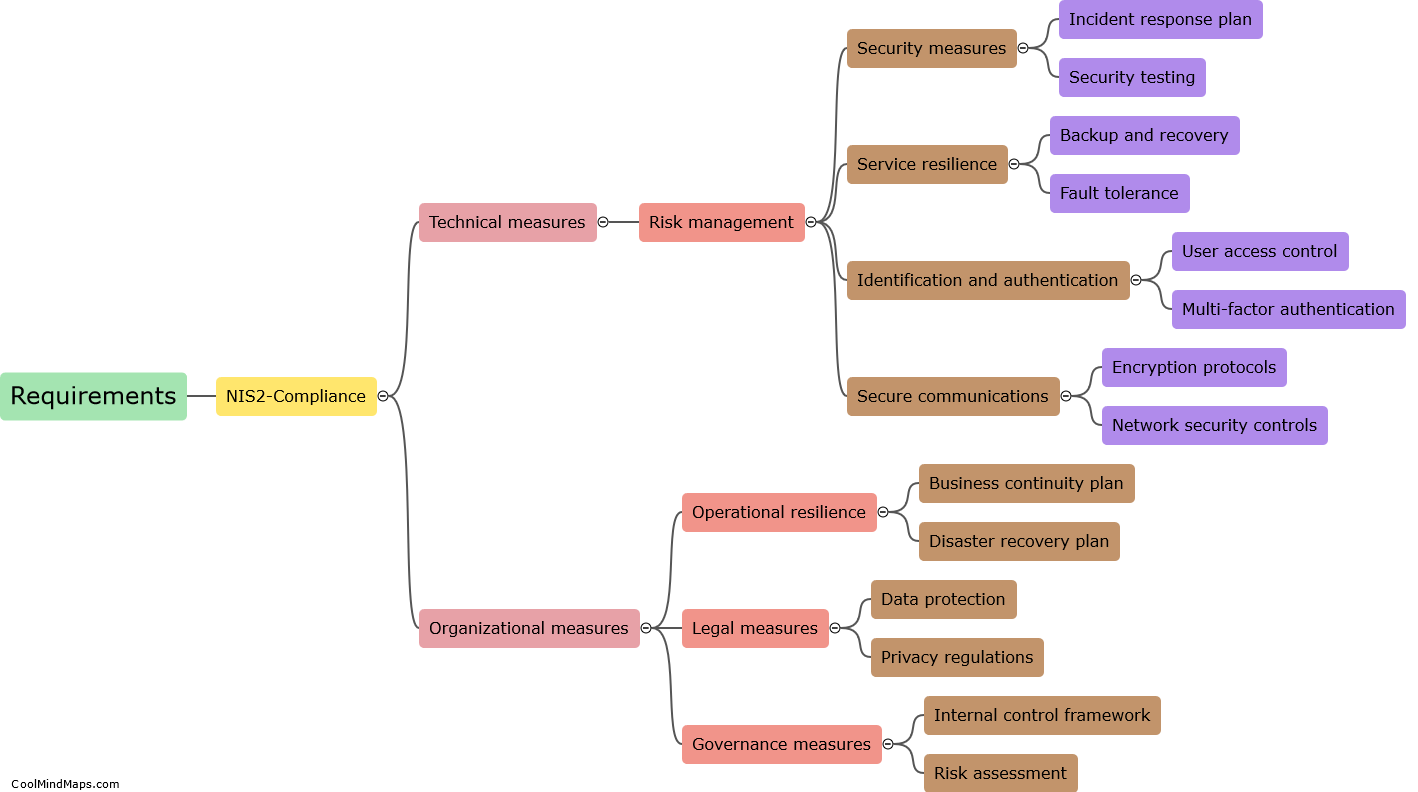
Common vulnerabilities in ICS (Industrial Control Systems) policies and procedures revolve around gaps in security measures and inadequate implementation practices. One significant vulnerability is the lack of proper access controls, where employees or unauthorized individuals may gain unauthorized access to critical systems. Inadequate authentication and authorization processes can also expose vulnerabilities, as weak or easily guessable passwords can be used by attackers to compromise ICS systems. Insufficient patch management and update procedures leave systems vulnerable to known exploits and attacks. Additionally, the lack of regular security assessments and audits can further heighten the risk of vulnerabilities in ICS policies and procedures. These vulnerabilities require continuous improvement and monitoring to ensure the protection and resilience of critical infrastructure systems.
This mind map was published on 27 January 2024 and has been viewed 116 times.