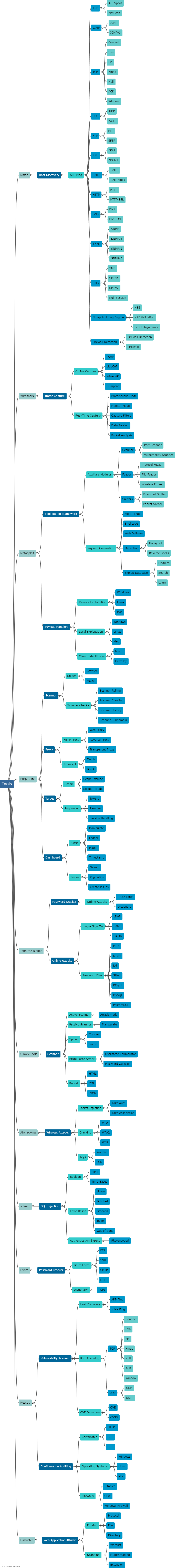
How can network penetration tools be categorized?
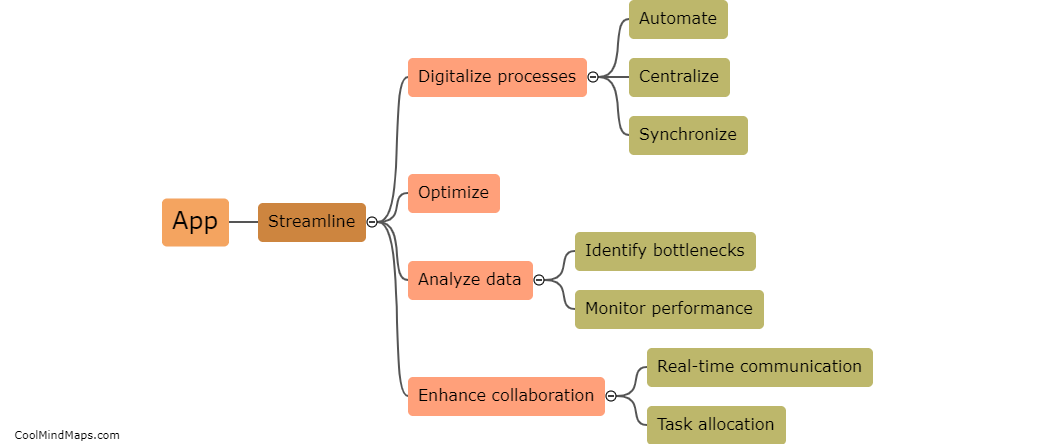
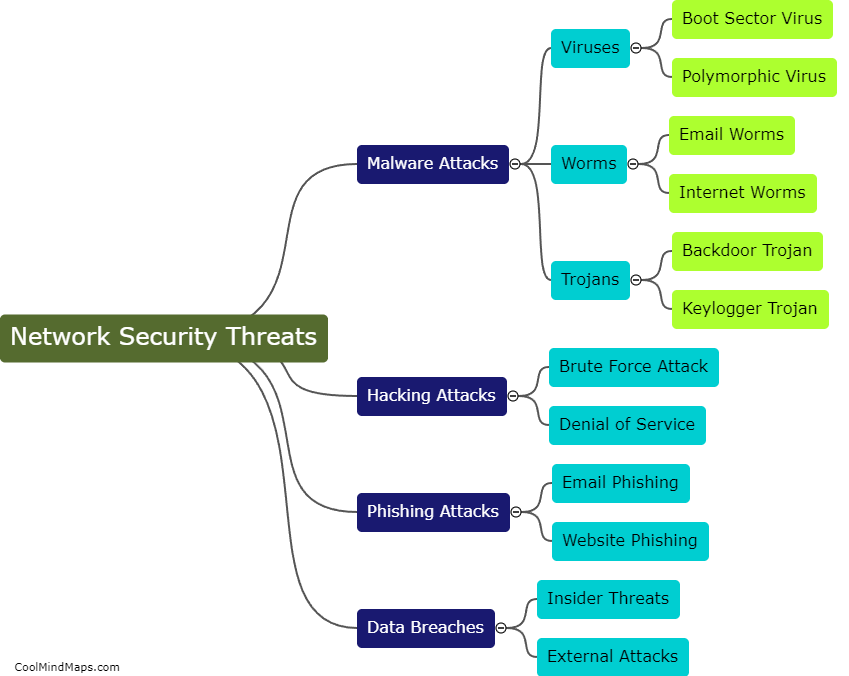
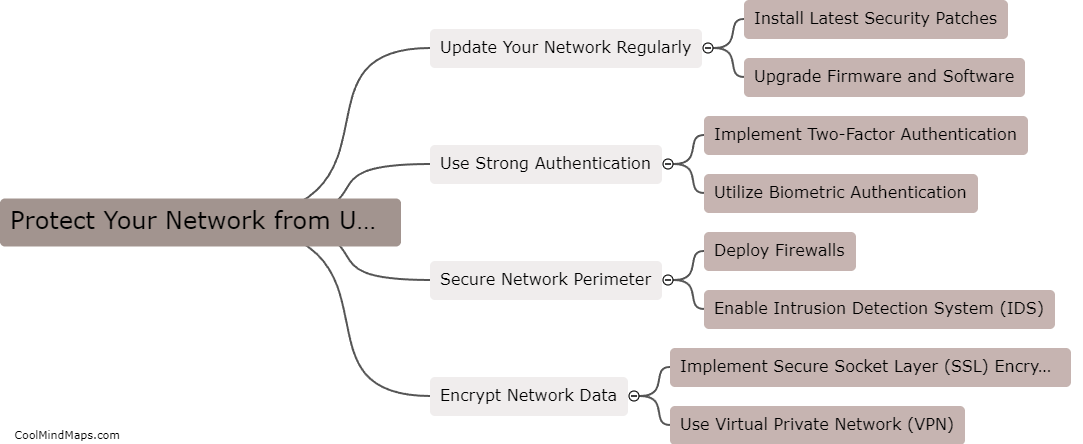
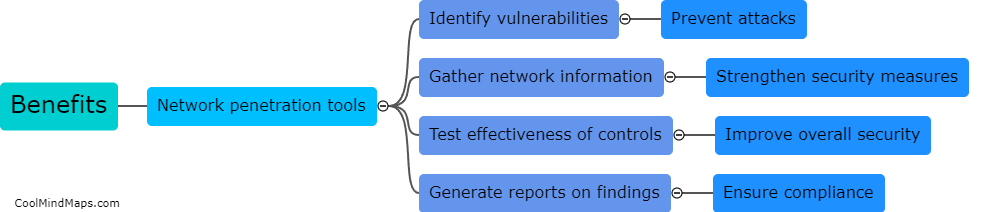
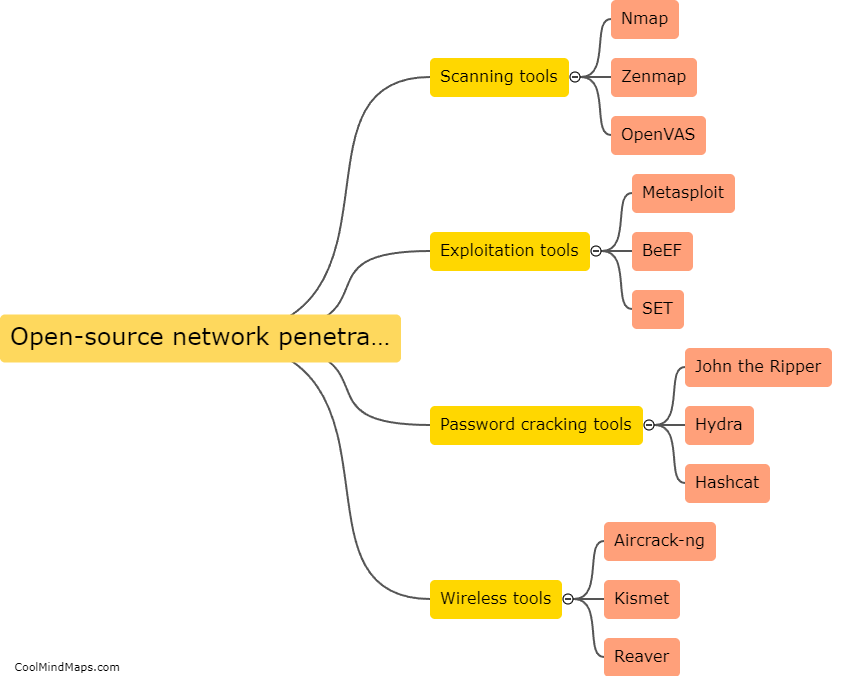
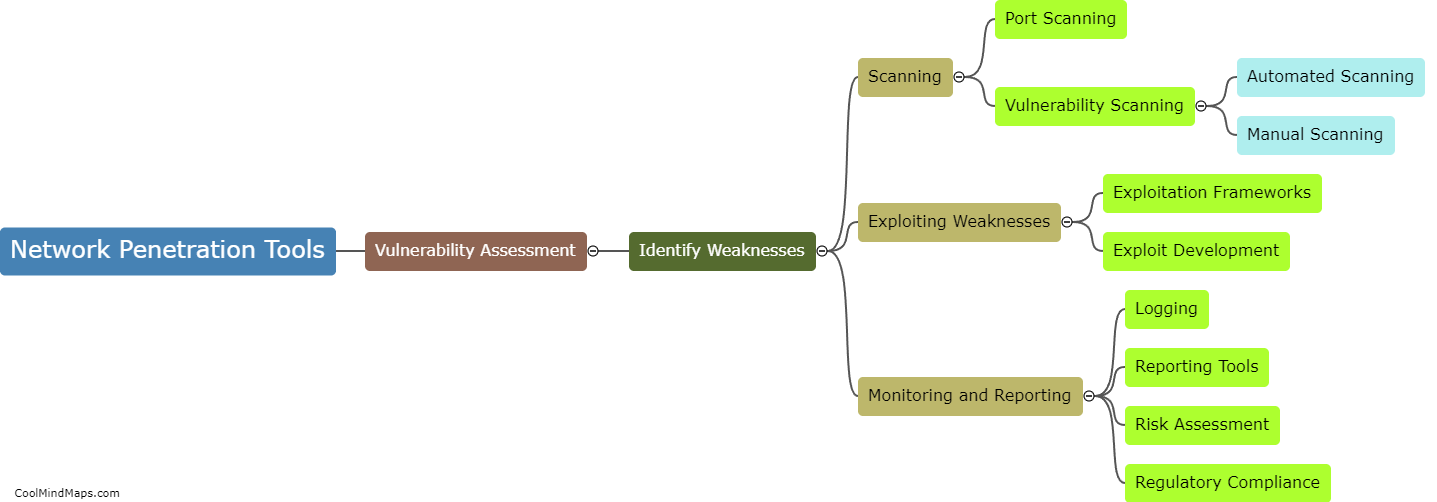
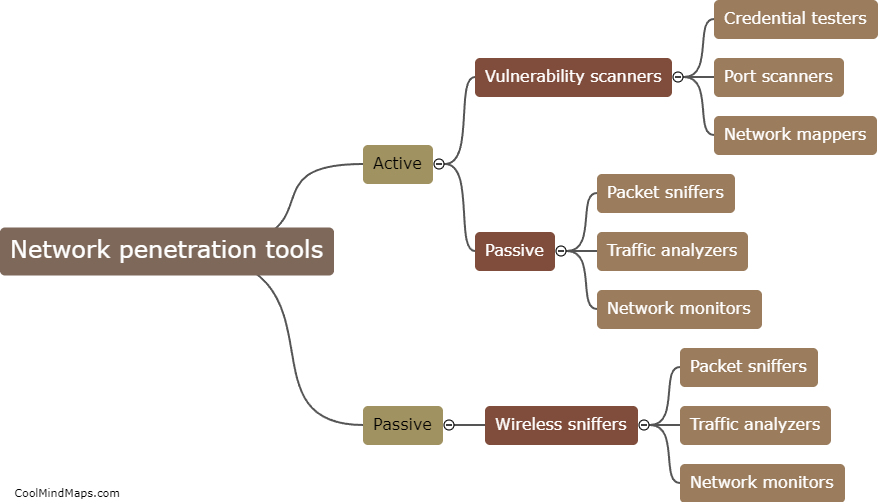
Network penetration tools can be categorized into several types based on their functionality and purpose. One common categorization is based on the stage of the penetration testing process they are used for. For example, there are tools specifically designed for information gathering and reconnaissance, such as port scanners and vulnerability scanners. Other tools are used for active exploitation and gaining unauthorized access, like password crackers and exploit frameworks. Some tools facilitate post-exploitation activities, including privilege escalation or lateral movement within a network. Another categorization can be based on whether the tools are open-source or commercial. Open-source tools, like Metasploit and Nmap, are widely used due to their flexibility and community support. Commercial tools, on the other hand, often offer additional features, customer support, and more polished interfaces. Overall, these categorizations help professionals select the most appropriate network penetration tools to effectively evaluate and strengthen the security of their networks.
This mind map was published on 5 October 2023 and has been viewed 84 times.