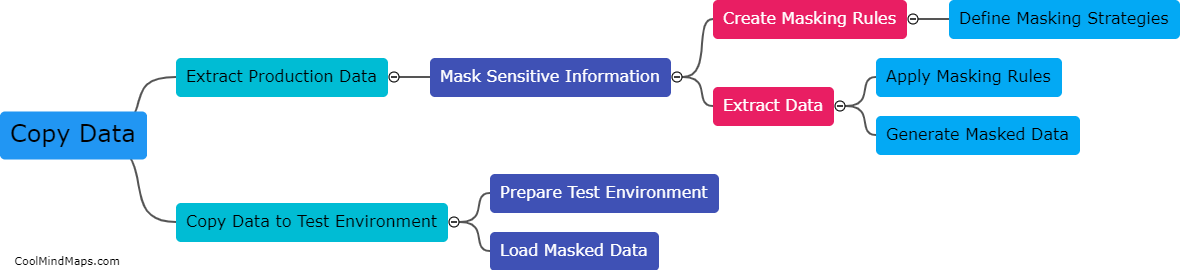
What are the steps involved in copying masked production data into a test environment?
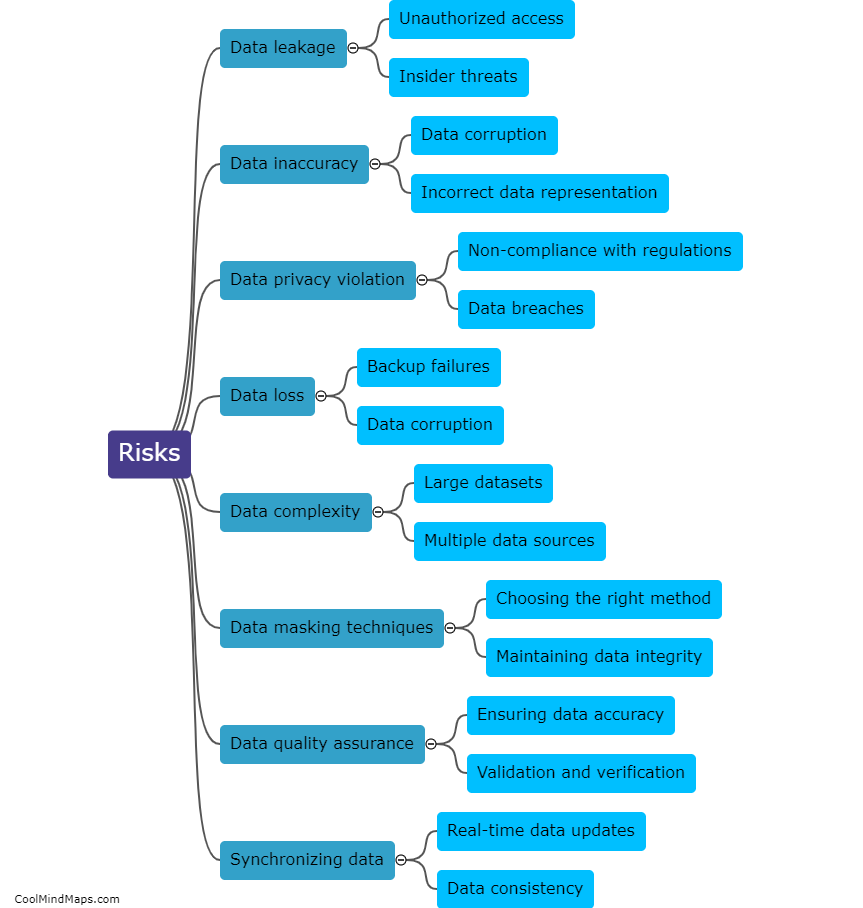
Copying masked production data into a test environment involves several steps to ensure the privacy and security of sensitive information. Firstly, a comprehensive data masking plan should be created, specifying the specific data elements that need to be masked, such as personally identifiable information (PII) or financial data. Secondly, a secure copy of the production data should be created, ensuring that it is encrypted and protected during transportation and storage. Next, the data masking process is executed, which involves replacing sensitive data with realistic but fictitious values. This includes techniques such as encryption, tokenization, or data shuffling. After masking, the data is verified to ensure both its quality and consistency with the original production data. Finally, the masked data is loaded into the test environment, ensuring proper access controls and monitoring throughout the process. These steps ensure that sensitive information is safeguarded while still providing realistic data for testing purposes.
This mind map was published on 27 July 2023 and has been viewed 103 times.