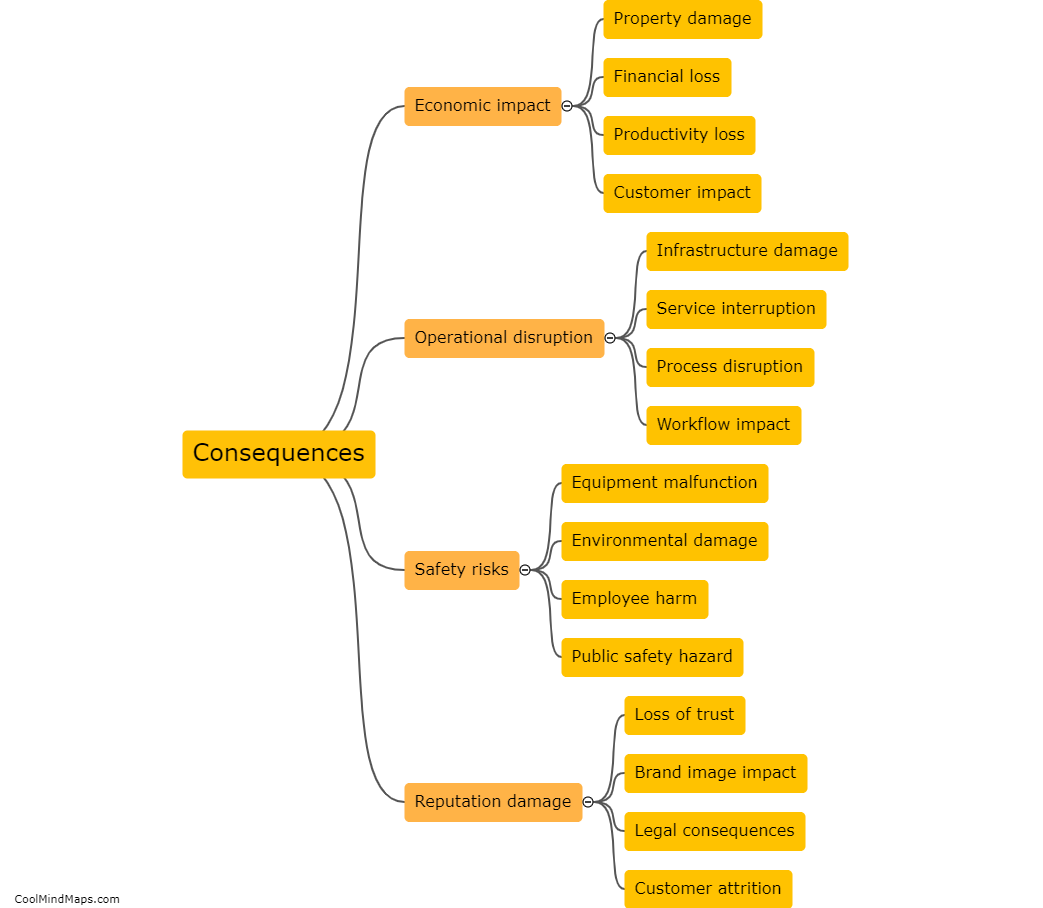
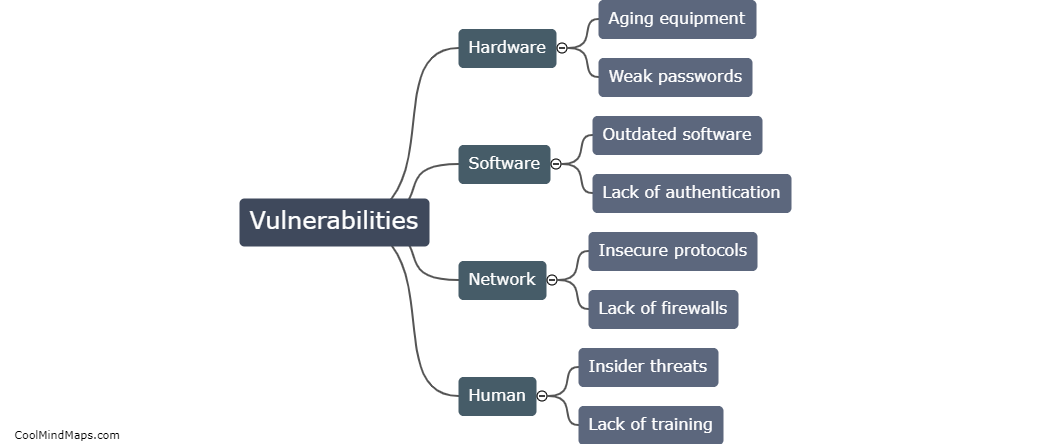
What are the vulnerabilities in SCADA systems?
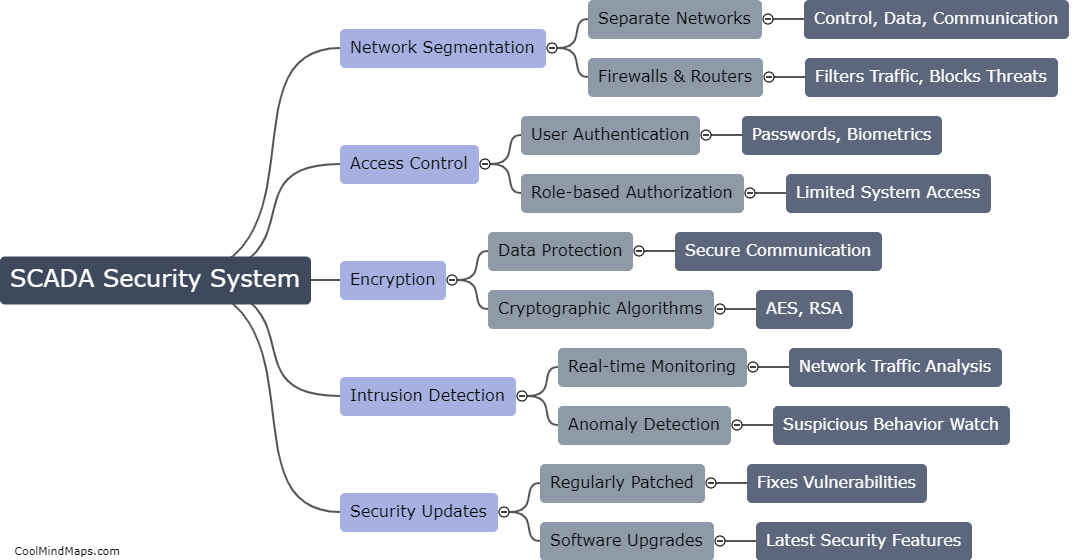
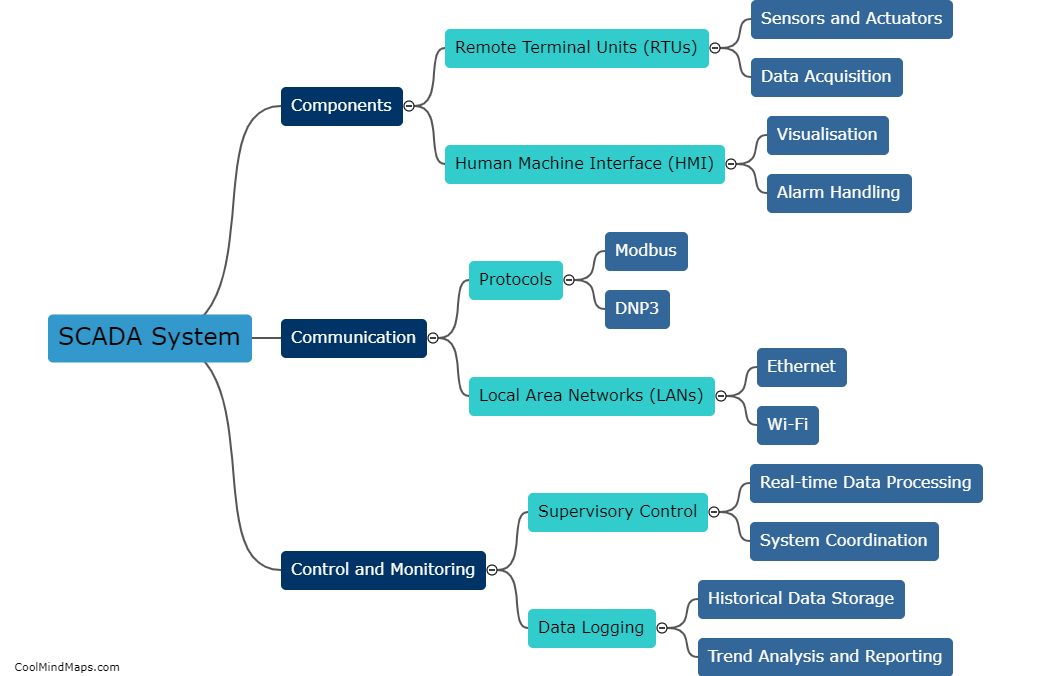
SCADA (Supervisory Control and Data Acquisition) systems are widely used in industries to monitor and control critical infrastructure and processes. While these systems have numerous benefits, they also possess vulnerabilities that can be exploited by malicious actors. One primary vulnerability is outdated or unpatched software, as SCADA systems often run on legacy operating systems with outdated security measures. Another vulnerability arises from insecure remote access, as remote connections to SCADA systems can be targeted by hackers. Additionally, weak authentication mechanisms, inadequate network segmentation, and insufficient physical security measures pose risks to SCADA systems. Moreover, the interconnectedness of these systems with other IT networks increases the attack surface and the potential impact of cyber threats. These vulnerabilities highlight the need for robust cybersecurity measures, regular system updates, and proactive monitoring to protect SCADA systems and the critical infrastructure they control.
This mind map was published on 26 January 2024 and has been viewed 98 times.