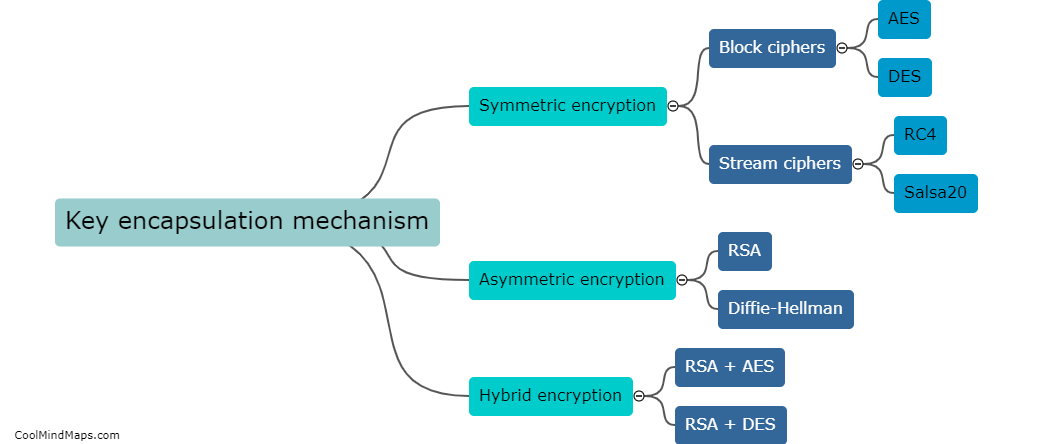
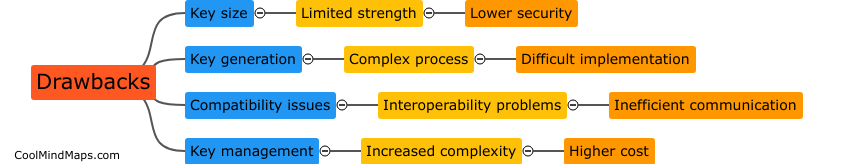
Are there any drawbacks or limitations to key encapsulation mechanisms?
While key encapsulation mechanisms (KEMs) offer several advantages, such as providing confidentiality and security, there are certain drawbacks and limitations associated with their use. One key limitation is the potential dependency on the computational hardness assumptions of certain mathematical problems, such as factoring large numbers or solving the discrete logarithm problem. If these assumptions are broken or feasible attacks are developed, it could render the security of KEMs compromised. Moreover, the performance of KEMs can sometimes be slower compared to other encryption methods, leading to increased computational overhead. Additionally, the scalability of KEMs has been a concern, as large-scale deployments might be challenging due to the sheer number of public-private key pairs generated and used. Despite these limitations, ongoing research and development efforts aim to address these drawbacks and enhance the effectiveness and efficiency of key encapsulation mechanisms.
This mind map was published on 4 February 2024 and has been viewed 96 times.