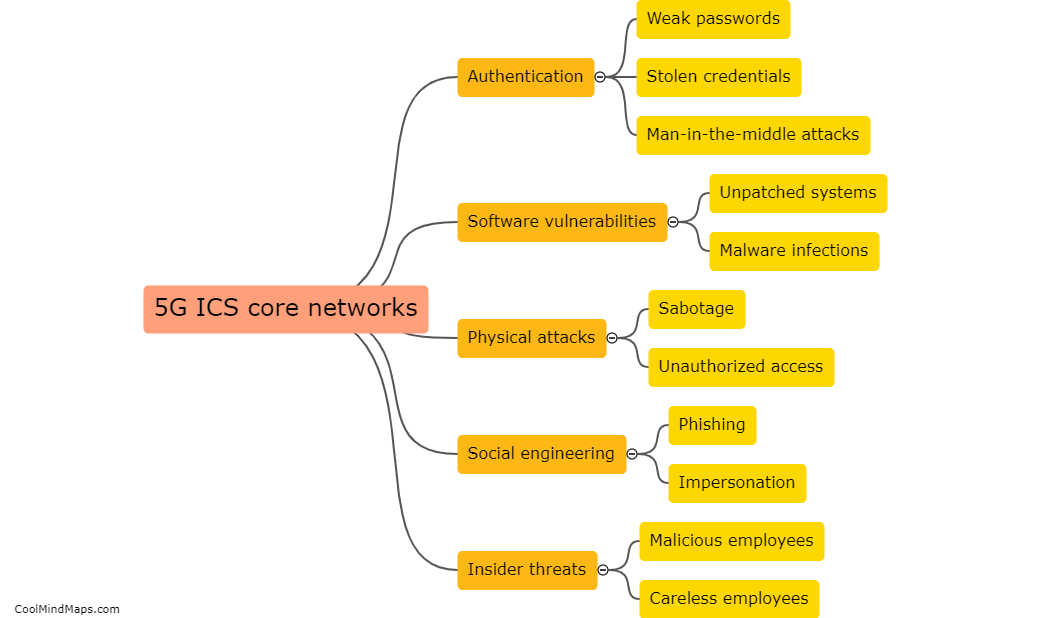
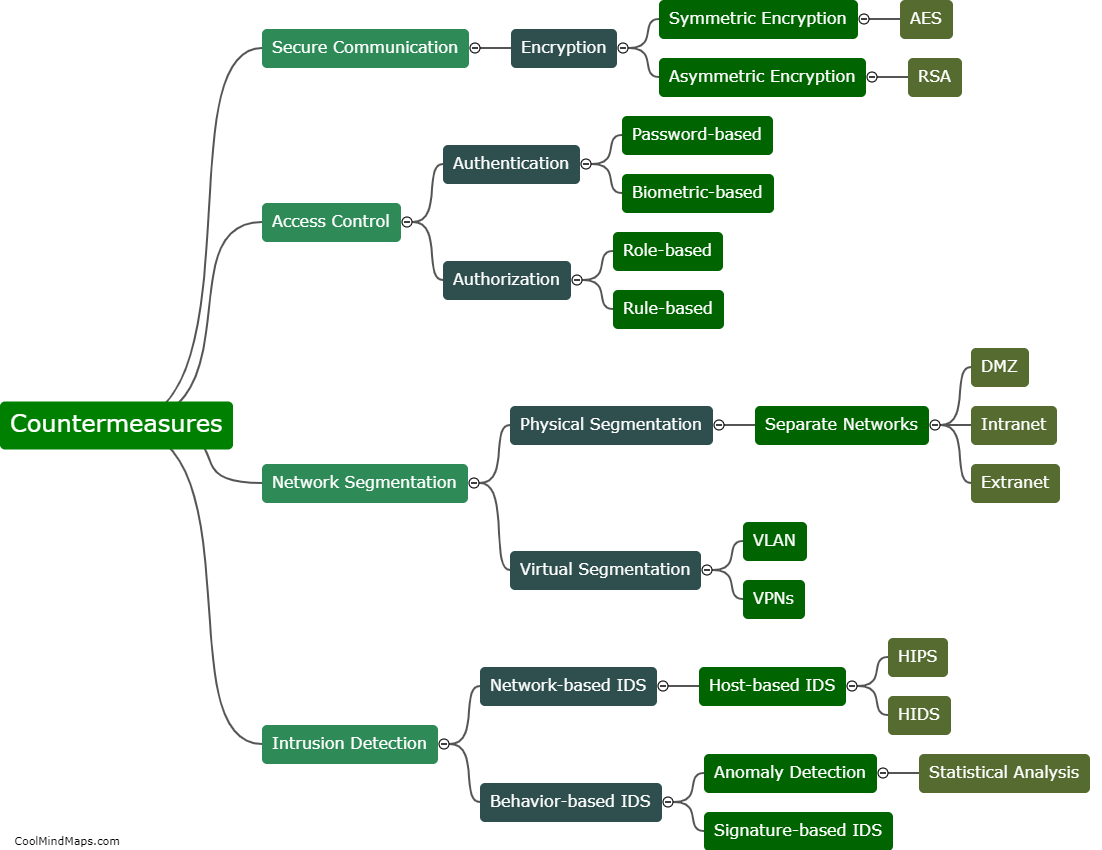
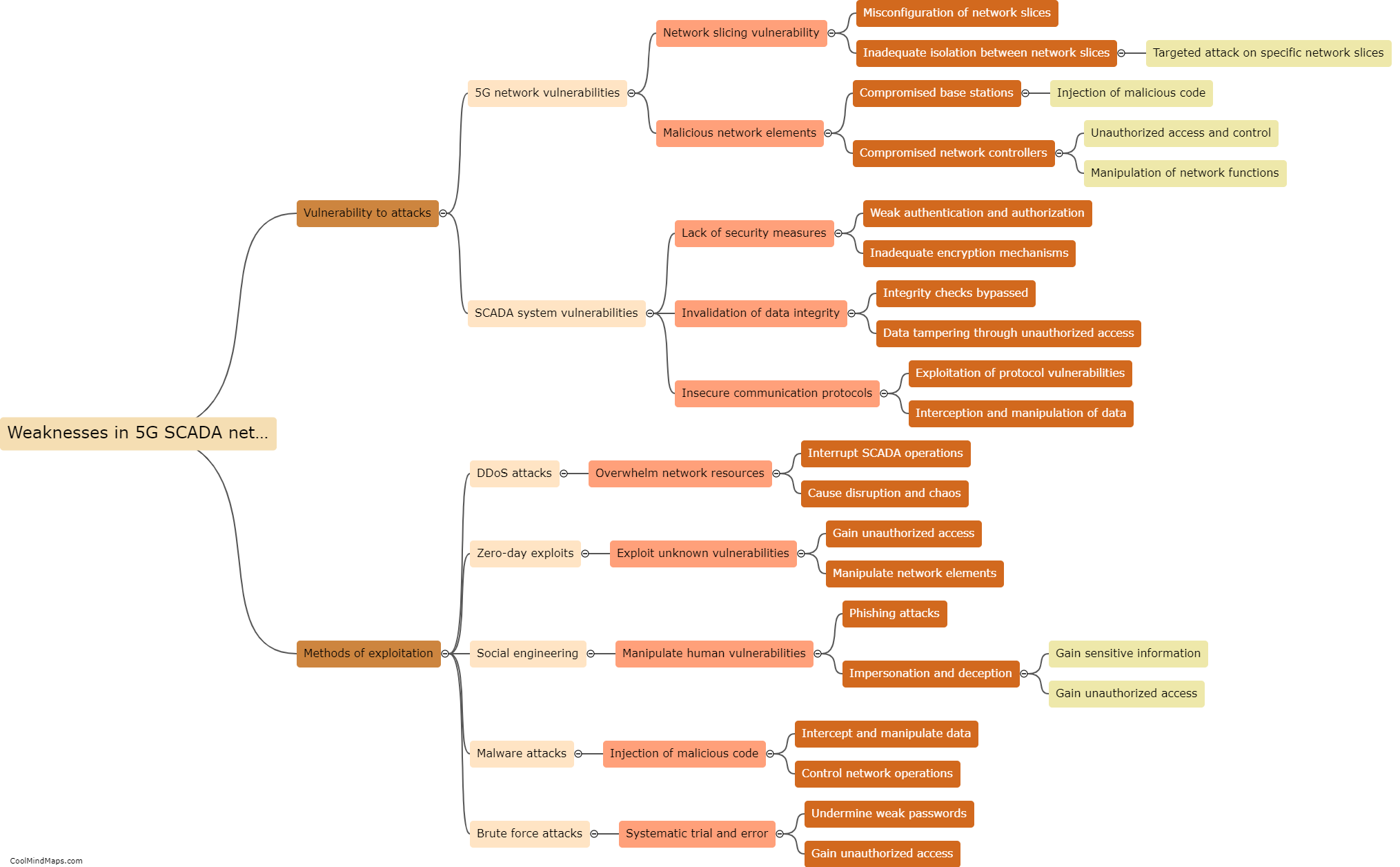
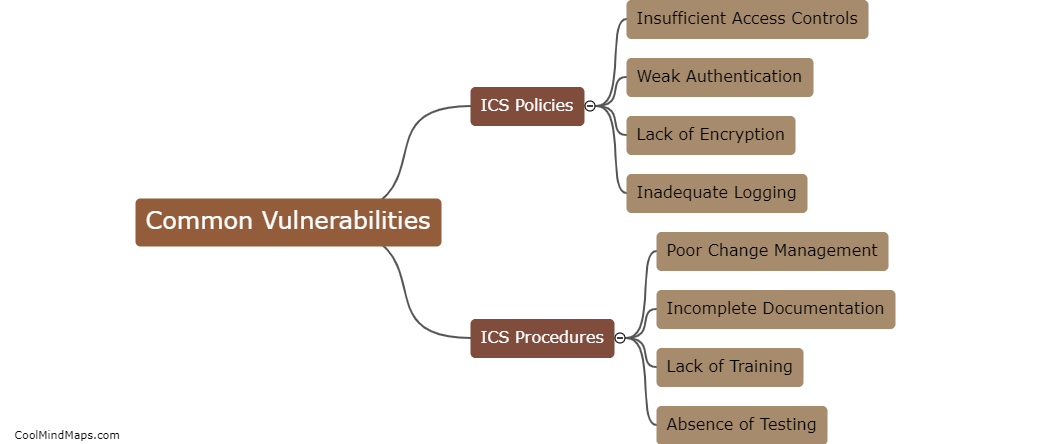
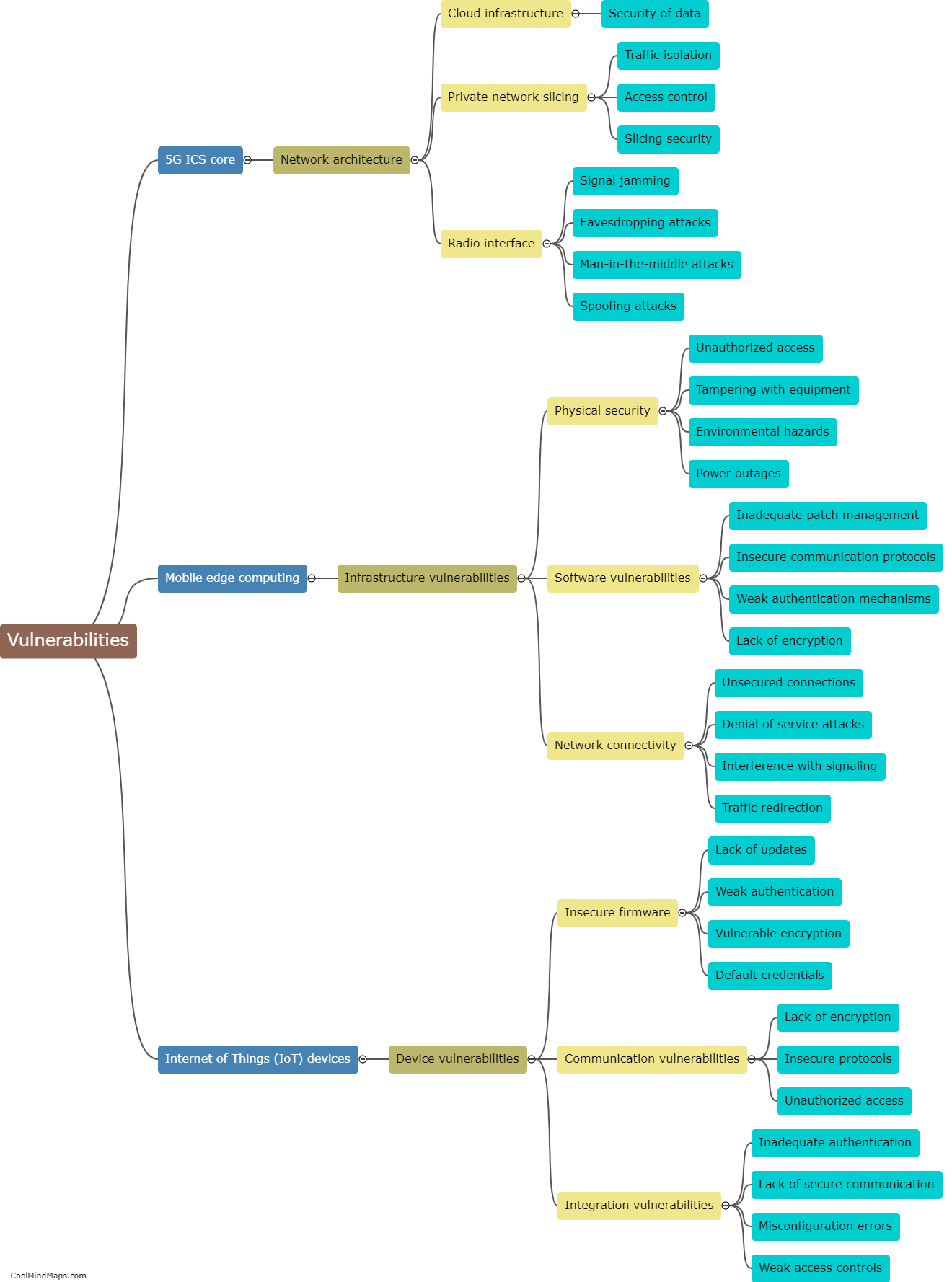
What are the vulnerabilities of 5G ICS core networks?
The implementation of 5G networks in industrial control systems (ICS) brings with it a host of benefits, such as increased speed, lower latency, and improved reliability. However, it also introduces new vulnerabilities that can pose significant risks to critical infrastructure. One vulnerability lies in the increased attack surface due to the proliferation of connected devices and expanded network architecture. With more devices and connections, there are more potential entry points for cyber attackers. Additionally, the reliance on software-defined networking and virtualization technologies introduces new risks, as they can be susceptible to various cyber threats. Furthermore, the high data rates and low latency of 5G networks may enable new attack vectors, such as distributed denial-of-service (DDoS) attacks at unprecedented scale. It is crucial to address these vulnerabilities through robust security measures and ongoing monitoring to protect the integrity and resilience of 5G ICS core networks.
This mind map was published on 27 January 2024 and has been viewed 58 times.