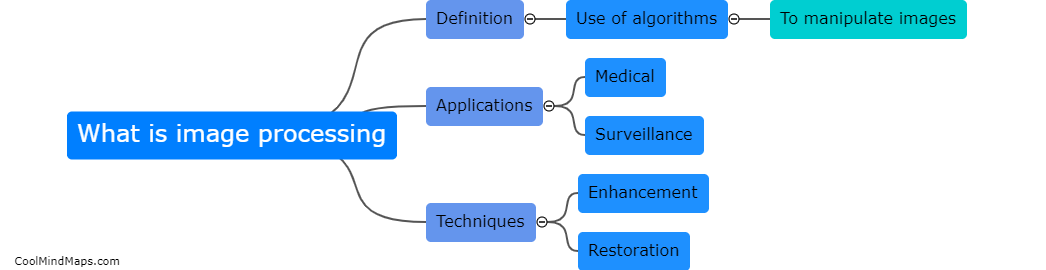
Image processing is the use of algorithms and techniques to manipulate and enhance digital images. This can involve tasks such as resizing, cropping, adjusting colors, removing noise, and applying filters to improve the overall quality or appearance of an image. Image processing is used in...

ESP, or extrasensory perception, is a phenomenon where individuals are able to perceive information through means other than the five senses. While the exact mechanism of how ESP works is not fully understood, some theories suggest that it may involve tapping into a universal consciousness...
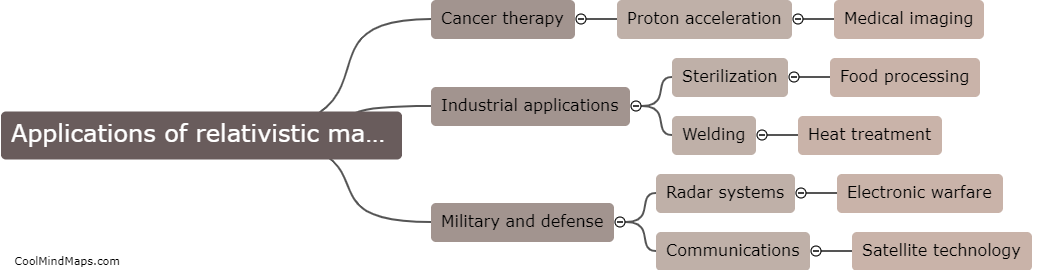
Relativistic magnetrons are advanced microwave generators that have a wide range of applications in various fields. One of the primary uses of relativistic magnetrons is in the generation of high-power microwaves for radar systems, particle accelerators, and communication devices. Additionally, relativistic magnetrons are also utilized...

Moral monitoring refers to the process of monitoring and regulating one's own behavior based on ethical principles, societal norms, and personal values. It involves being conscious and mindful of the impact of one's actions on oneself and others, as well as holding oneself accountable for...
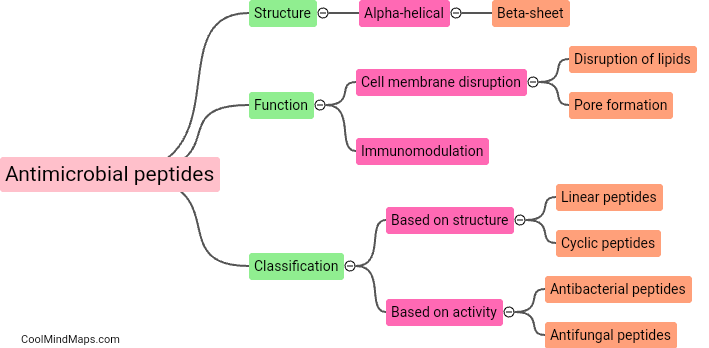
Antimicrobial peptides are small proteins that are part of the innate immune system and play a crucial role in defending the body against pathogens such as bacteria, viruses, and fungi. They work by disrupting the cell membranes of these pathogens, leading to their destruction. Antimicrobial...
To measure a target lesion in RECIST (Response Evaluation Criteria in Solid Tumors), one should take the longest diameter of the lesion as the measurement. This should be done using computed tomography (CT) or magnetic resonance imaging (MRI) scans. The measurement should be taken in...
RECIST (Response Evaluation Criteria in Solid Tumors) measurements are commonly used to assess tumor response to treatment in clinical trials and practice. To perform RECIST measurements, first identify the target lesions and measure their longest diameter using imaging modalities such as CT or MRI. Take...

Lõputöö eesmärk on tavaliselt olla üliõpilase viimase õppetöö ja uurimuse näitena, mis demonstreerib nende teadmisi, oskusi ja võimekust analüüsida ning lahendada konkreetse valdkonna probleeme. Lõputöö eesmärgiks on ka anda võimalus üliõpilasele süvendada oma teadmisi ning arendada oma uurimis- ja kirjutamisoskusi. Lisaks annab lõputöö võimaluse teha...
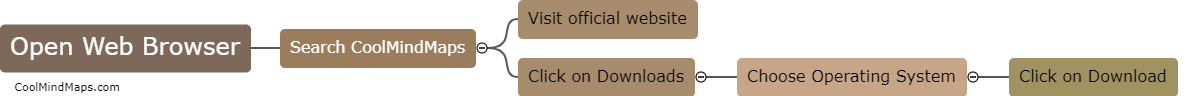
To download CoolMindMaps, simply visit the official website or app store for your device. Look for the CoolMindMaps application and follow the prompts to download and install it onto your device. Once the download is complete, you can start creating and organizing your mind maps...
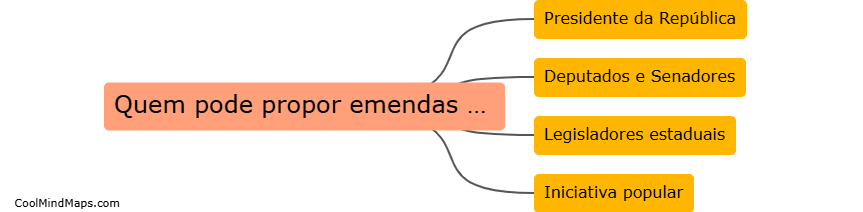
No Brasil, apenas os membros do Congresso Nacional têm a prerrogativa de propor emendas à Constituição. De acordo com o artigo 60 da Constituição Federal, as emendas podem ser apresentadas por um terço dos deputados da Câmara dos Deputados ou do Senado Federal, pelo Presidente...
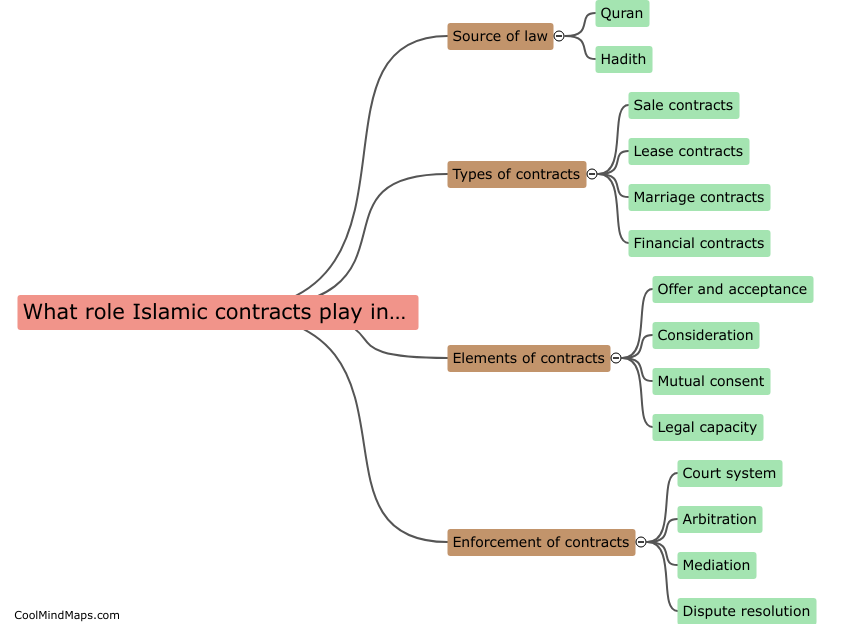
Islamic contracts play a crucial role in Sharia law as they govern the relationships and transactions between individuals in accordance with Islamic principles. These contracts are rooted in the principles of fairness, justice, and mutual consent, and serve as a means for individuals to conduct...
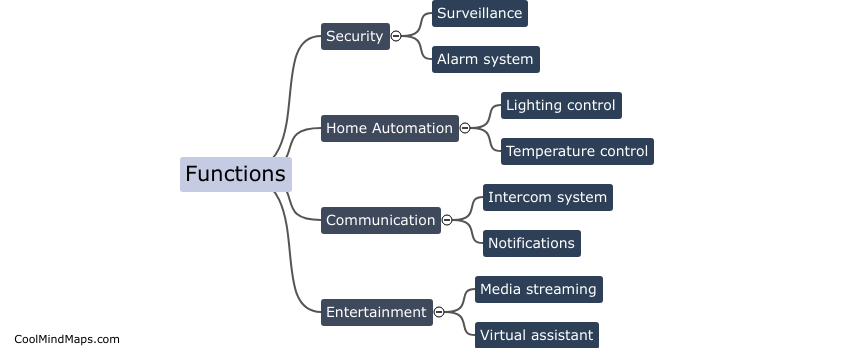
Haus Assistent offers a wide range of functions to help automate and simplify household tasks. Some of the key functions include controlling smart home devices such as lights, thermostats, and security cameras, creating schedules and routines for appliances and gadgets, setting reminders and timers, managing...

Vernacularization in language is essential for ensuring effective communication and understanding among diverse populations. By translating or adapting content into the vernacular or local language spoken by a particular community, individuals are more likely to engage with and comprehend the information being conveyed. This approach...
![Prove: [vdash forall x (P(x) rightarrow Q(x)) rightarrow (exists x P(x) rightarrow exists x Q(x))]](mindmaps/3d8e73370313a73849616760ef1a4443.png)
The statement being proven is "For all x, if P(x) implies Q(x), then if there exists an x such that P(x) is true, then there exists an x such that Q(x) is true." This can be proven by assuming the antecedent, \forall x (P(x) \rightarrow...

A parse tree is a graphical representation of the syntactic structure of a formula or sentence in a formal language. It shows how the components of the formula are related to each other and how they combine to form the overall structure. Drawing a parse...
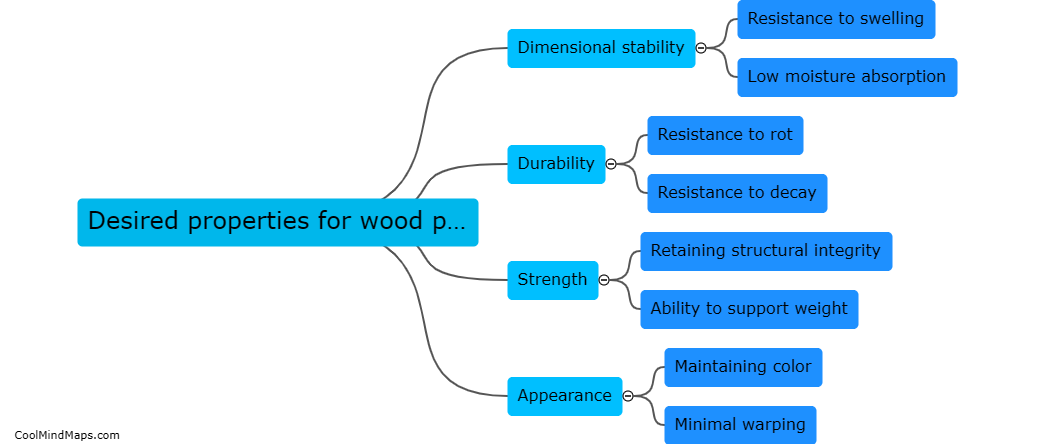
When selecting a wood product for use in water, several desired properties should be considered. Water resistance is key, as the wood should be able to withstand exposure to moisture without warping, rotting, or deteriorating. Additionally, durability is important to ensure the wood can withstand...
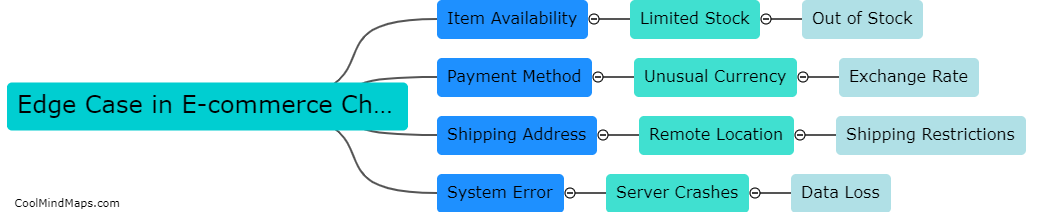
An example of an edge case in an e-commerce checkout process is when a customer attempts to purchase an item using a gift card that has an exact value equal to the total cost of the order. In this scenario, the customer may encounter issues...
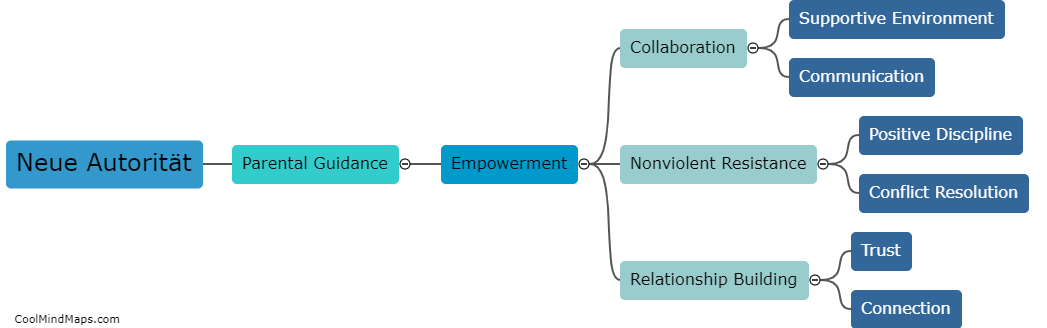
Neue Autorität, or New Authority, is a concept developed by Haim Omer and Arist von Schlippe as an approach to parenting and discipline. It emphasizes the importance of building a relationship of trust and collaboration between parents and their children, rather than relying on traditional...
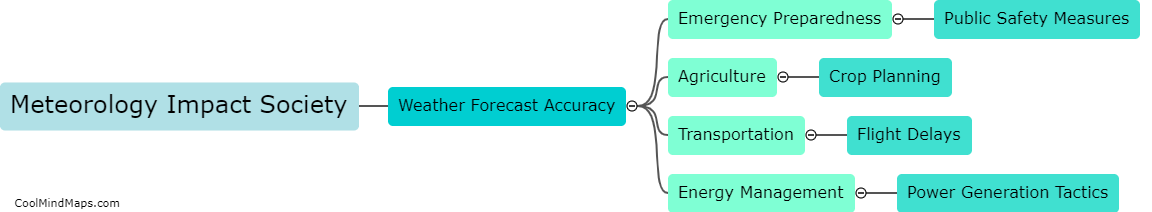
Meteorology plays a crucial role in society by providing essential information about weather patterns and trends. This information is important for a wide range of industries, including agriculture, aviation, transportation, construction, and energy production. By predicting and tracking weather events such as storms, hurricanes, and...
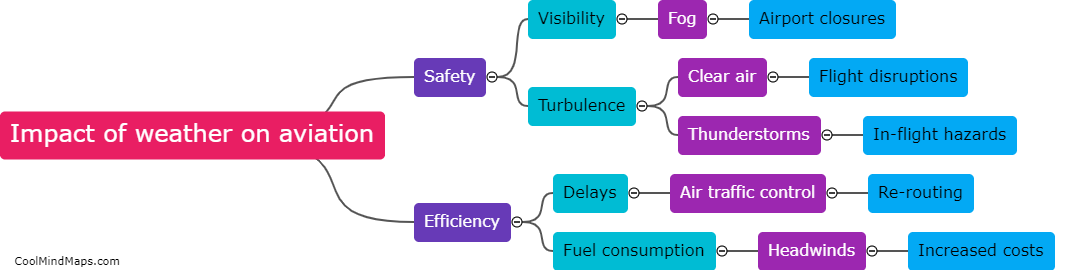
Weather has a significant impact on aviation, as it can affect safety, efficiency, and overall flight operations. Poor weather conditions such as thunderstorms, icing, fog, or strong winds can lead to flight delays, diversions, or cancellations. Pilots must account for weather conditions when planning flights,...
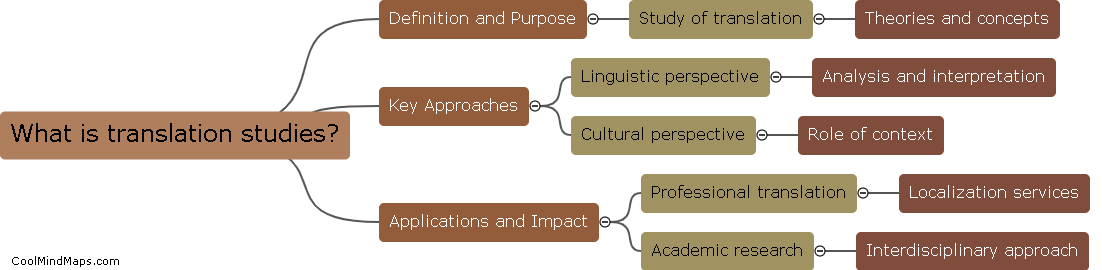
Translation studies is the academic field that focuses on the theory, history, and practice of translating texts from one language to another. It examines the various challenges and considerations involved in transferring meaning and culture between languages, as well as the impact of translation on...
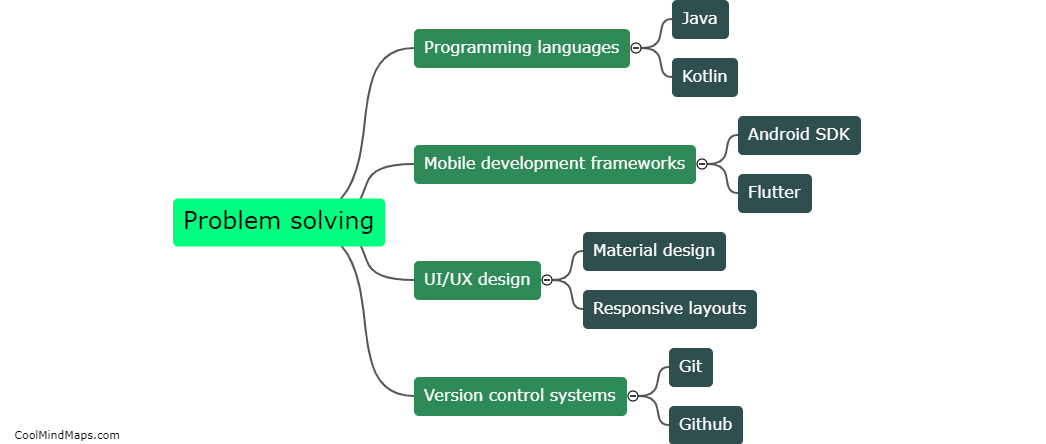
Key skills for an Android developer include proficiency in Java and the Android SDK, knowledge of Android Studio and other development tools, familiarity with XML and JSON for data exchange, understanding of app design principles, and experience with debugging and testing. Additionally, strong problem-solving abilities,...
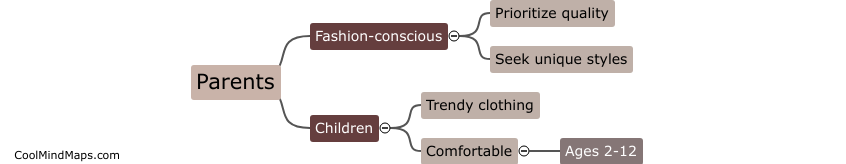
The target market for Mini Classy clothing brand is trendy and fashionable parents who are looking for unique and stylish clothing options for their children. The brand's designs are modern, edgy, and playful, catering to parents who want their kids to stand out and express...

Mini Classy is a children's clothing brand that was founded in 2014 by designer Michelle Lopez. The brand quickly gained popularity for its unique and edgy designs that catered to children who wanted to stand out and express their individuality. Mini Classy has collaborated with...
مقدمه مقاله ISI یک بخش بسیار مهم است که باید به دقت و با استفاده از تکنیکها و الگوهای مربوط به نگارش مقالات علمی تهیه شود. این بخش باید اطلاعات عمیق و کاملی ارائه دهد تا خواننده بتواند به راحتی متوجه هدف و اهداف آن...

پیشرفت حرفه ای مجری های تلویزیون معمولاً از طریق تجربه، آموزش و به روز بودن با تکنولوژی های جدید صورت میپذیرد. آموزش های مربوط به رسانه ها و روش های ارتباطی، ارتقاء مهارت های زبانی، انعطاف پذیری در مواجهه با شرایط مختلف و توانایی برقراری...
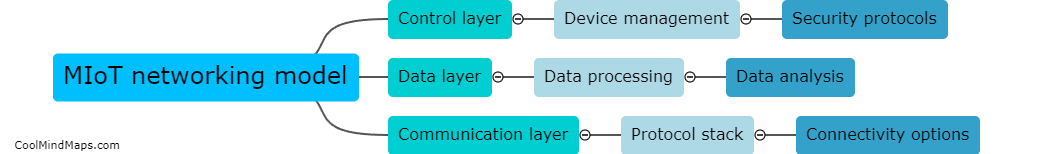
The MIoT (Massive Internet of Things) networking model is a complex system that enables the seamless connection and communication between a vast number of devices. While there may not be a single visual representation that encapsulates all aspects of this networking model, diagrams and illustrations...
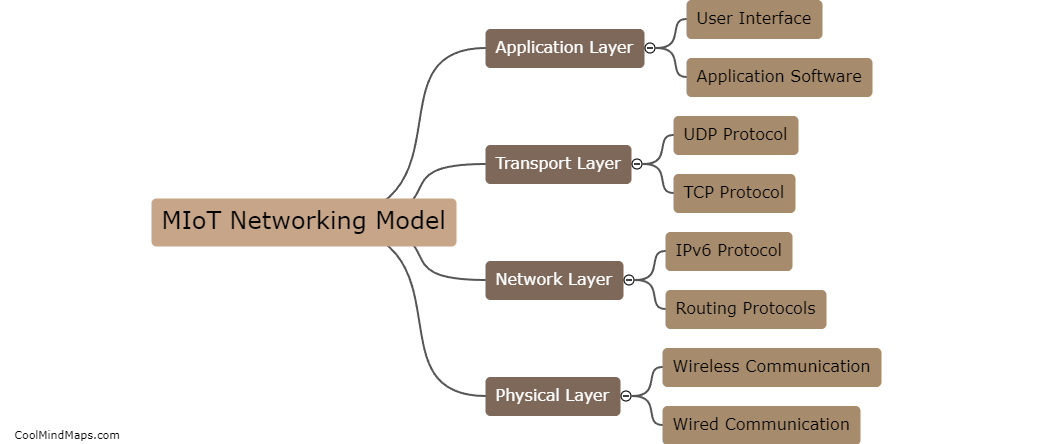
The MIoT (Massive Internet of Things) networking model consists of three main layers: the perception layer, the network layer, and the application layer. The perception layer includes sensors and devices that collect data from the physical environment. The network layer involves communication protocols and technologies...
The layers in the MIoT networking model interact through a hierarchical structure that allows for efficient communication and data exchange between devices. The physical layer is responsible for transmitting and receiving data packets through various communication channels. The data link layer ensures that data is...
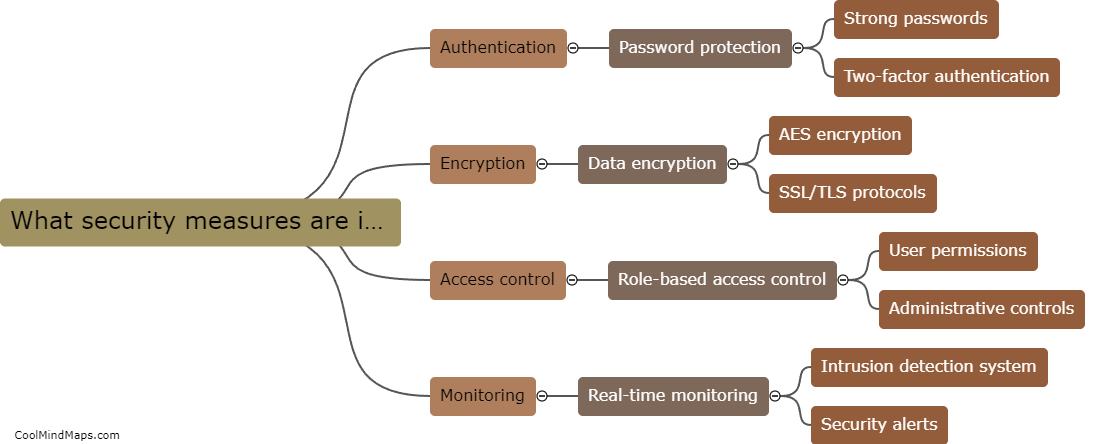
Security measures for MIoT systems typically include encryption of data transmitted between devices and networks, secure authentication protocols to prevent unauthorized access, regular software updates to patch vulnerabilities, and network segmentation to isolate critical systems from potential threats. Additionally, many organizations employ intrusion detection systems,...
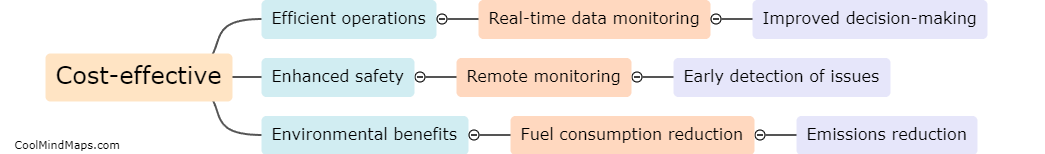
The benefits of using Maritime Internet of Things (MIoT) in maritime industries are numerous. MIoT technology allows for better monitoring and management of vessel operations, leading to increased efficiency and safety. By using sensors and connected devices, MIoT enables real-time data collection on the condition...

These components interact with each other through a series of interconnected processes and communication channels. For example, the CPU processes instructions from the software and sends signals to the memory to retrieve data. The memory then sends that data back to the CPU for further...
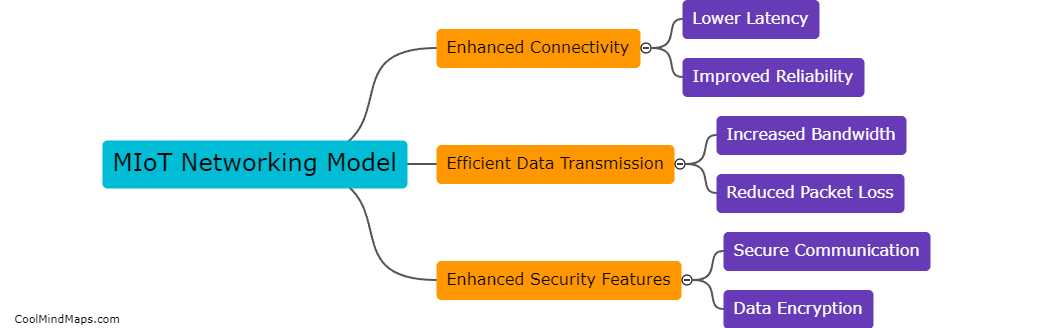
The MIoT (Mesh Internet of Things) networking model improves efficiency by creating a self-organizing network of interconnected devices that can communicate with each other, without the need for a centralized hub. This allows for faster and more reliable data transmission, as the devices can route...
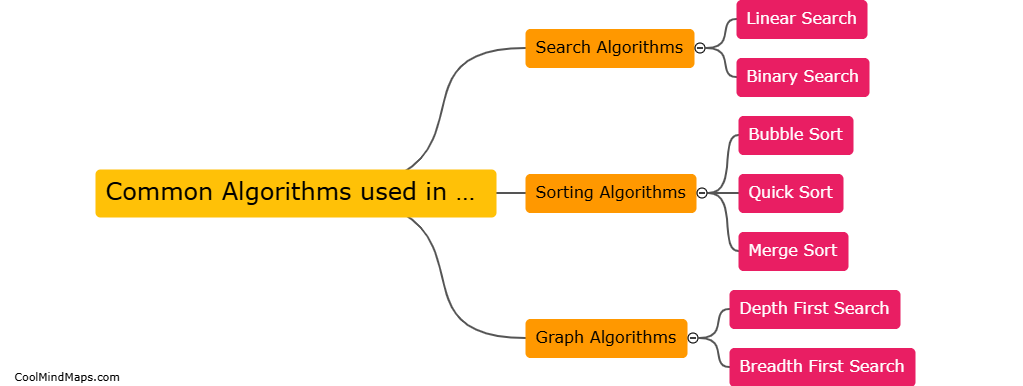
Some common algorithms used in data structures include sorting algorithms such as quicksort, merge sort, and bubble sort for arranging data in a specific order, searching algorithms like linear search and binary search for finding a particular value within a dataset, and traversal algorithms like...
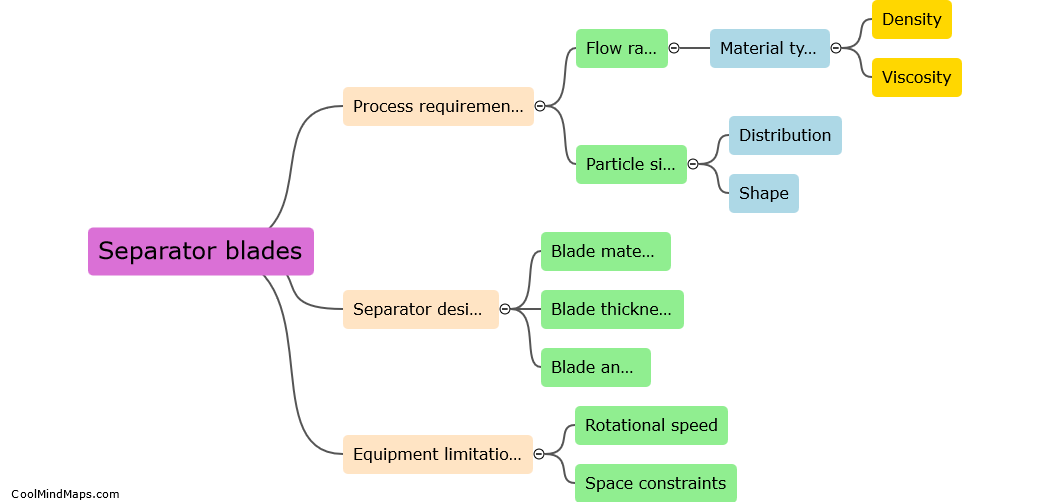
The optimal number of separator blades to use in a process is determined by several factors, including the size of the particles being separated, the desired level of separation efficiency, the flow rate of the material being processed, and the physical characteristics of the separator...
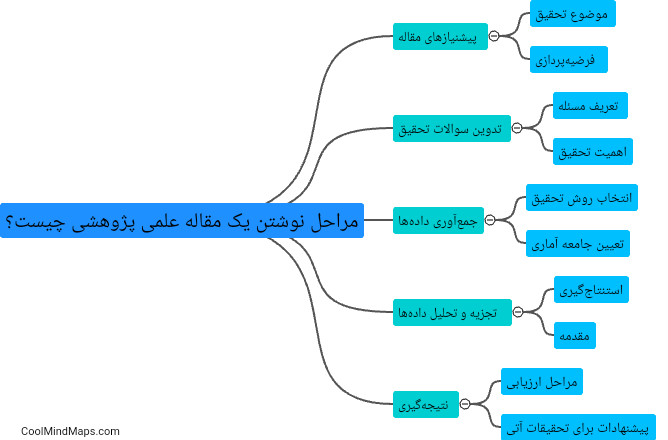
مراحل نوشتن یک مقاله علمی پژوهشی شامل مراحل گوناگونی است که نویسنده باید طی کند تا به نتیجه نهایی برسد. این مراحل شامل انتخاب موضوع، جمع آوری اطلاعات، تحلیل داده ها، نوشتن متن و حتی انتشار نهایی مقاله در یک ژورنال علمی معتبر میباشد. اهمیت...
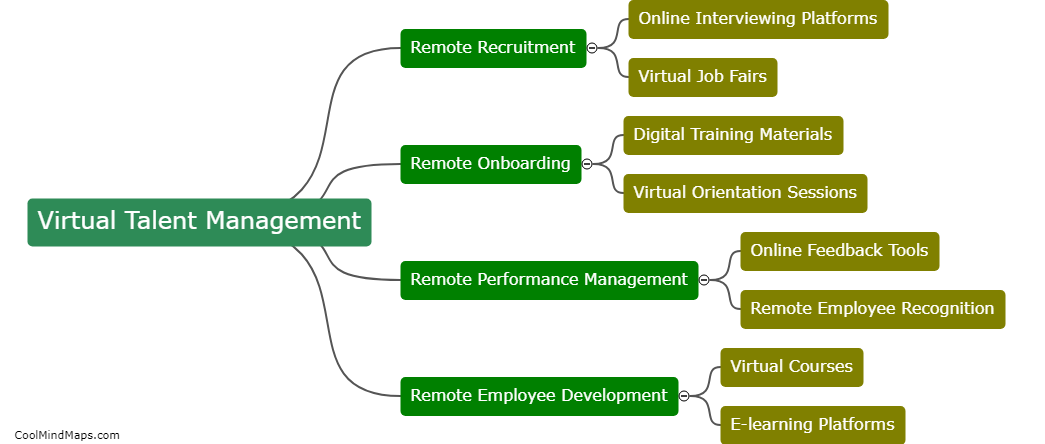
Virtual talent management is the practice of recruiting, developing, and retaining employees using digital tools and platforms. This approach allows organizations to manage their talent remotely, without the need for in-person interactions. Virtual talent management encompasses activities such as virtual recruitment, training, performance management, and...

برای انتخاب بهترین شکل قهوه ای، ابتدا نیاز است که از منابع قهوه ای معتبر و با کیفیت خرید کنید. قهوه هایی که از بعضی مناطق معروف برای پرورش قهوه مثل کلمبیا یا اتیوپی آورده می شوند، معمولاً کیفیت بهتری دارند. همچنین می توانید به...
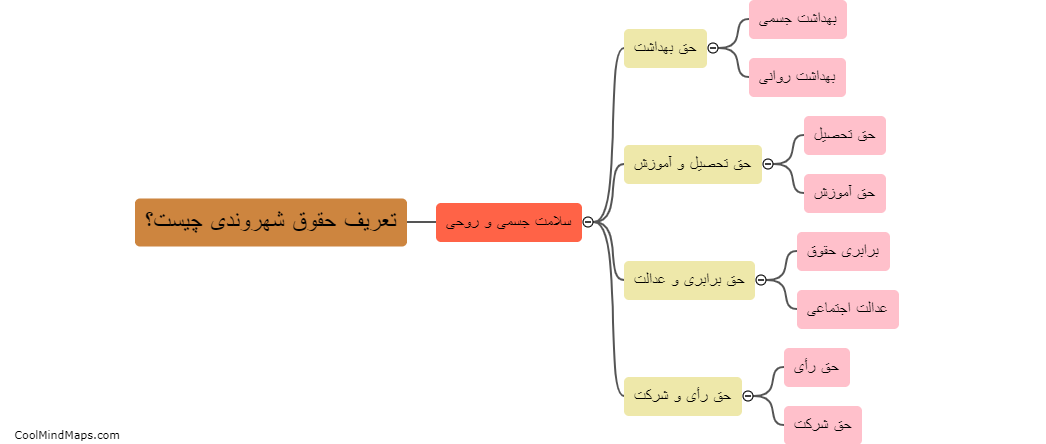
تعریف حقوق شهروندی به مجموعه حقوق و وظایفی اطلاق میشود که به افراد در یک جامعه داده میشود تا بتوانند به آزادی و عدالت دست یابند. این حقوق اساسی شامل حقوق مدنی، سیاسی و اجتماعی است که تضمین میکند تا هر فرد به طور مساوی...
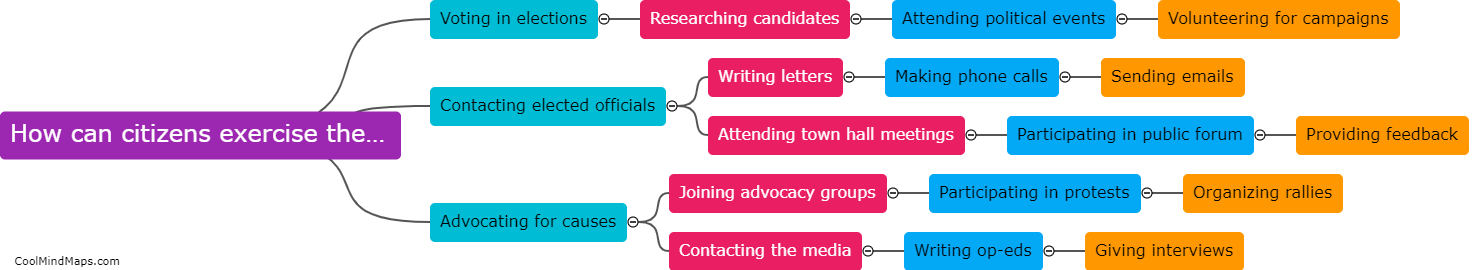
Citizens can exercise their rights by actively participating in the democratic process, such as voting in elections, contacting their elected officials to express their opinions, attending public meetings, and engaging in peaceful protests or demonstrations. Additionally, citizens can educate themselves on their rights and responsibilities...

A hormona antidiurética, também conhecida como vasopressina, é responsável pelo controle da reabsorção de água pelos rins. Sua principal função é regular o equilíbrio de líquidos no organismo, ajudando a manter a pressão sanguínea e os níveis de hidratação adequados. Quando os níveis de água...

A horizontal merger refers to a business combination involving two or more companies operating in the same industry and at the same stage of production. This strategic move allows the merging firms to achieve economies of scale, reduce competition, expand market share, and enhance overall...
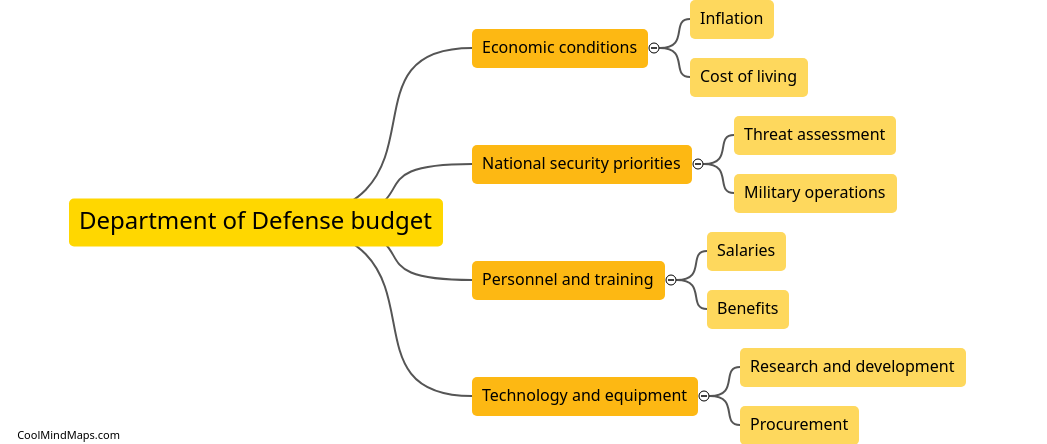
The Department of Defense budget is influenced by a variety of factors including national security threats, military readiness needs, technological advancements, and political priorities. The level of defense spending is often tied to the perceived threats facing the country, with increased funding necessary during times...
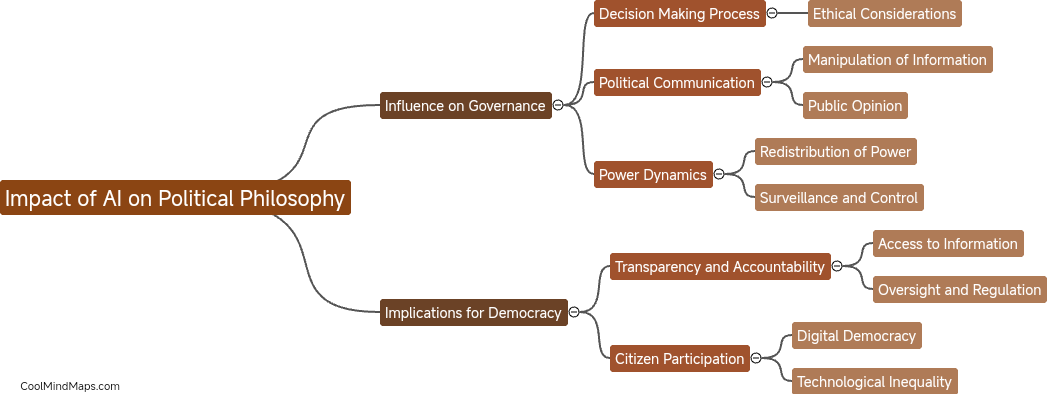
Artificial intelligence is transforming political philosophy by challenging traditional notions of democracy, power, and governance. The integration of AI technology in governance systems has the potential to enhance decision-making processes, increase efficiency, and improve public service delivery. However, concerns have been raised about the ethical...
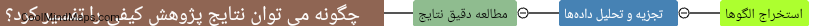
پژوهشهای کیفی معمولاً درک عمیقتری از مسائل ارائه میدهند و نتایج آنها نیازمند تفسیر است که گاهی اوقات چالشبر است. برای تفسیر نتایج پژوهش کیفی، ابتدا باید دادهها را با دقت بررسی کرده و الگوها و تم برگزیده را شناسایی کرد. سپس بیان کنید که...
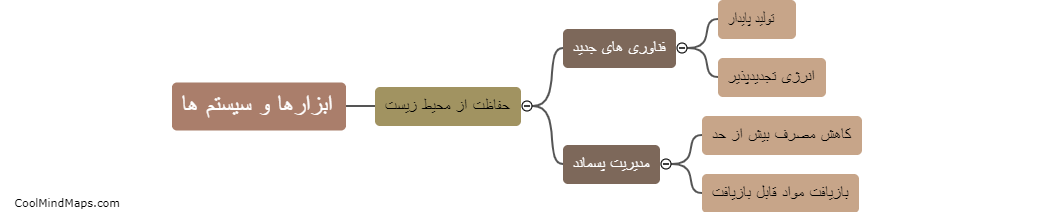
در حفاظت از محیط زیست از ابزارها و سیستمهای مختلفی بهره میگیریم که به وسیله آنها میتوانیم از منابع طبیعی محافظت کنیم. این ابزارها شامل استفاده از انرژی های تجدیدپذیر و پاک، کاهش زبالهها، استفاده از خودروهای تمیز و صفر انتشار، حفظ و نگهداری از...
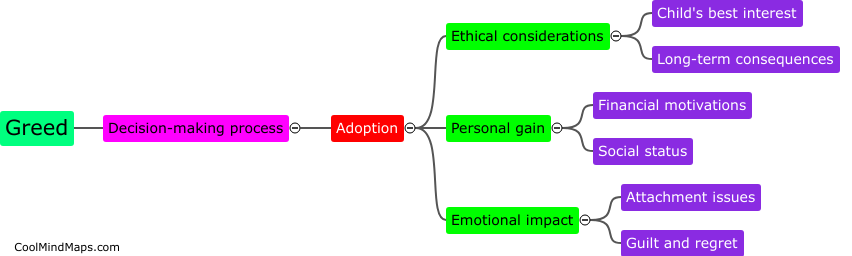
Greed can significantly impact the decision-making process in adoption by clouding judgment and leading individuals to prioritize financial gain over the well-being of the child. Some prospective adoptive parents may be driven by a desire to amass wealth or assets through adoption, leading them to...
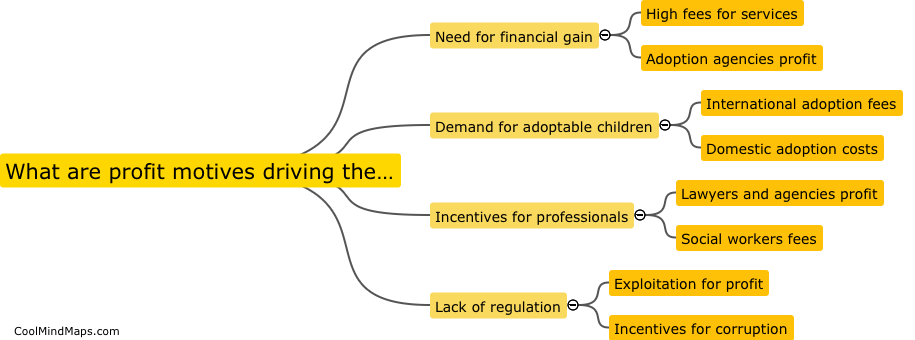
Profit motives are a key driving force in the adoption industry, as agencies and organizations involved in facilitating adoptions stand to gain financially from the process. This can create a conflict of interest, as the desire for profit may incentivize unethical practices such as pressuring...
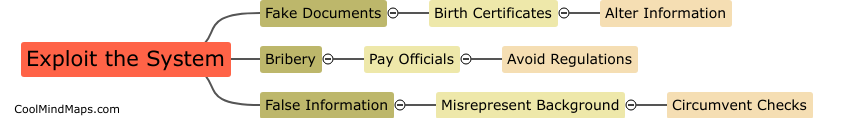
Adoptive parents can exploit the system by falsifying information on their adoption applications, such as their financial status or criminal record, in order to appear more favorable to adoption agencies. They may also manipulate birth parents or guardians into giving up their rights to the...
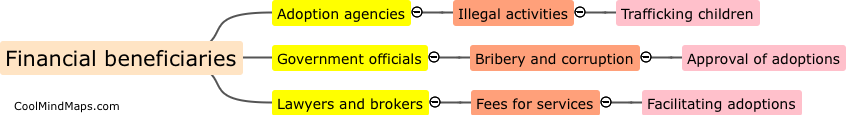
The individuals who benefit financially from adoption trafficking are often the intermediaries involved in the process, such as adoption agencies, lawyers, and facilitators. These parties profit from arranging and completing adoptions, often through unethical and illegal means such as coercion, deception, and bribery. In some...